Azure AD Identity Protection is part of AAD and it helps us to understand and remediate identity-based risks associated with a user sign-in process. This service understands the usage pattern of a user’s login on a daily basis such as the IP Details, the device he chooses to log in, and location and suggests to admins the course of action to take when an odd behaviour is spotted.
Azure review is part of Azure governance and it helps us to periodically validate user’s access that are part of an administrative unit or group when the user’s role has changed in an organization.
Licensing Requirements for Identity Protection
We will need an Azure AD P2 license to configure Identity Protection
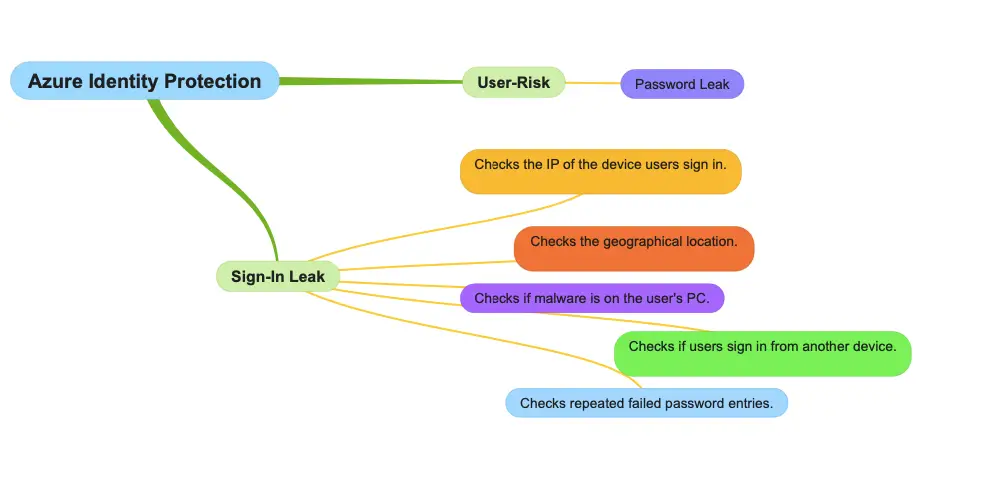
Risks Associated with AAD
There are two risks AD Identity tries to address
- User-Risks – That can be fixed with a password change.
- Sign-in Leaks – That can be fixed with an MFA enabled.
Permissions Associated with AAD
| Global Admin | Full access to identity protection |
| Security Admin | same as above but can’t reset the user’s password |
| Security Operator | Can view Identity protection reports and take action on user risks |
| Security Reader | a monitoring account |
Under the Azure portal, search for Azure AD Identity Protection
User risk policy is based on leaked user credentials
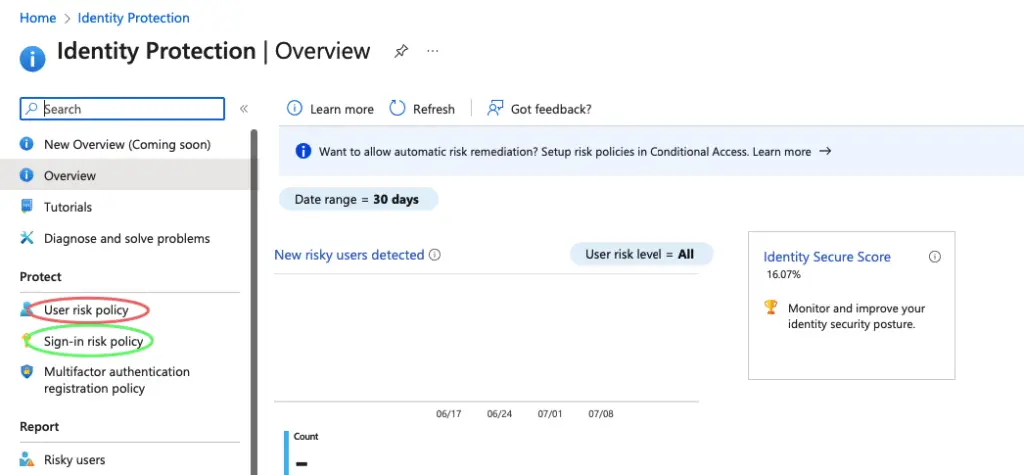
User risk policy is based on leaked user credentials so we will choose default risk control as “Low and Above”
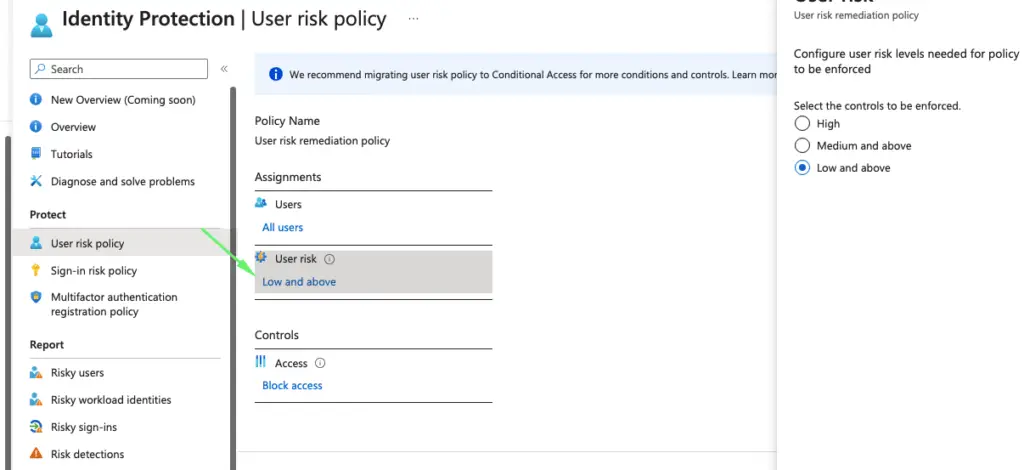
If the policy gets enforced, let’s ensure the user changes their password on login.
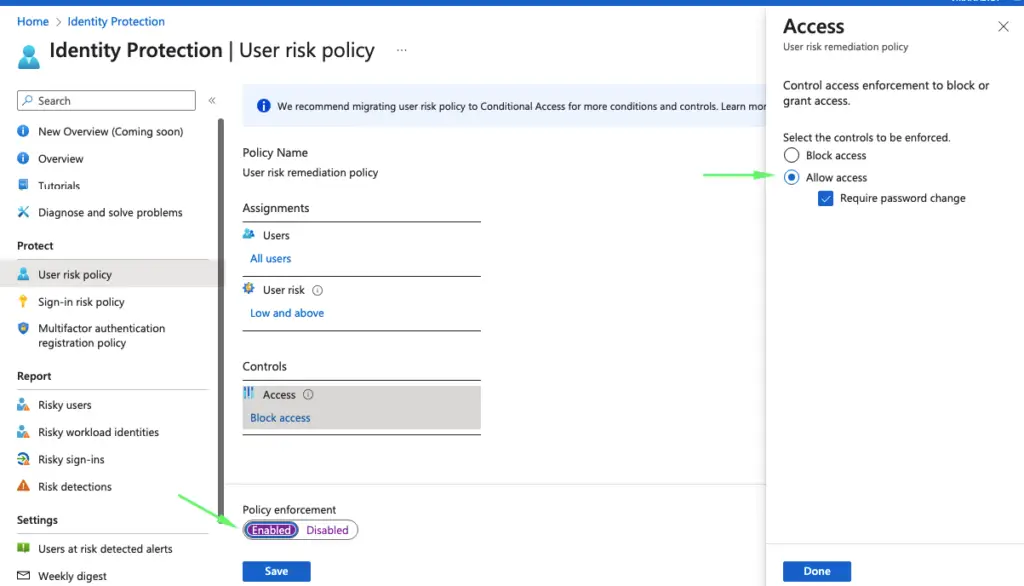
Sign-risk policy, as this is based on sign-leak it will enforce MFA
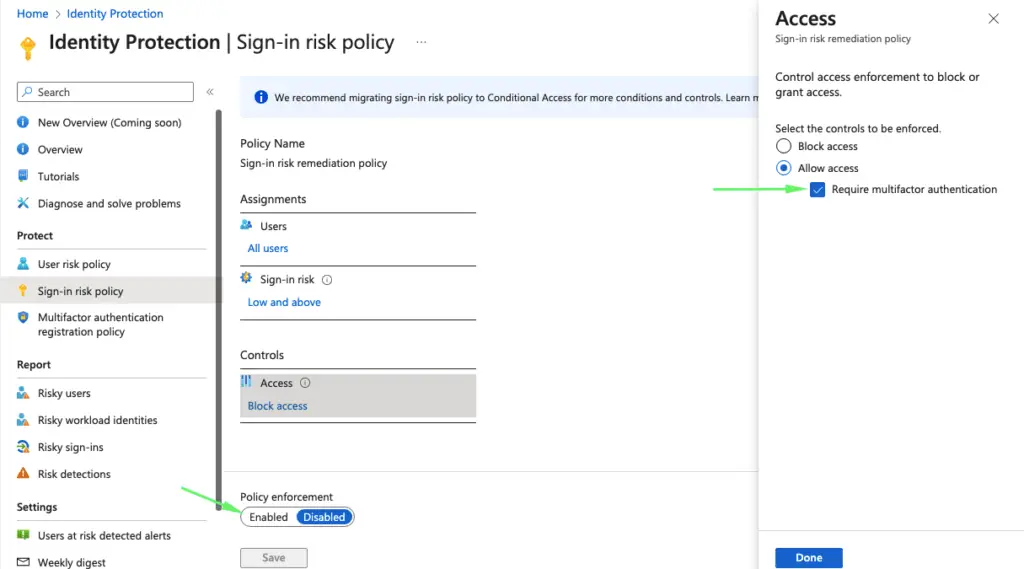
Finally, verify if the MFA registration policy is enabled.
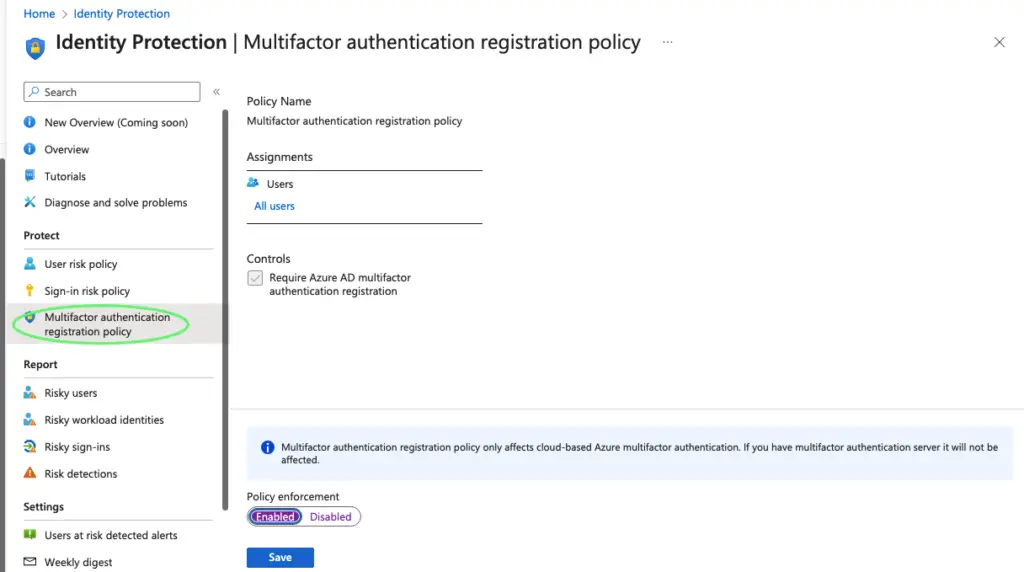
This will ensure sign-in and user-related risks are captured successfully.
Performing Access Reviews of AD Groups and Users
Access reviews are useful when a user leaves a department and moves on to a new role wherein he no longers needs the super admin elevated permissions.
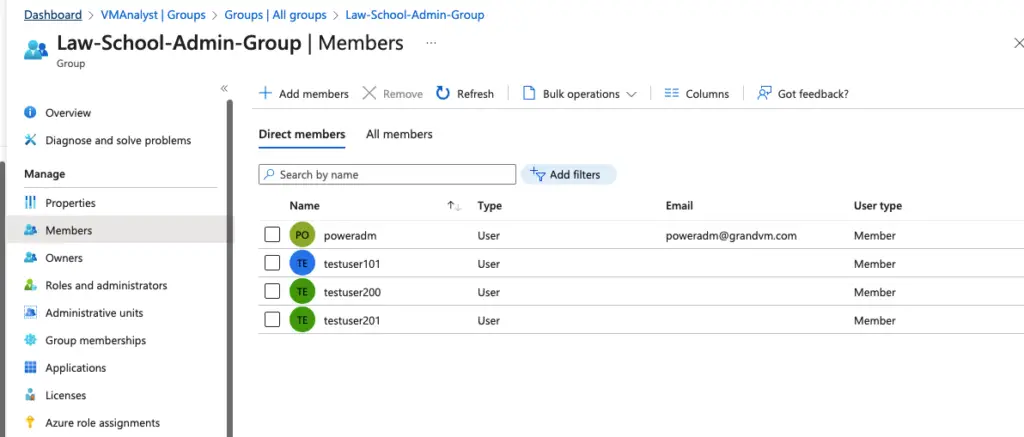
In this short demo, the following members are part of my law school admins group and we will attempt to one member from this group who has recently left the department.
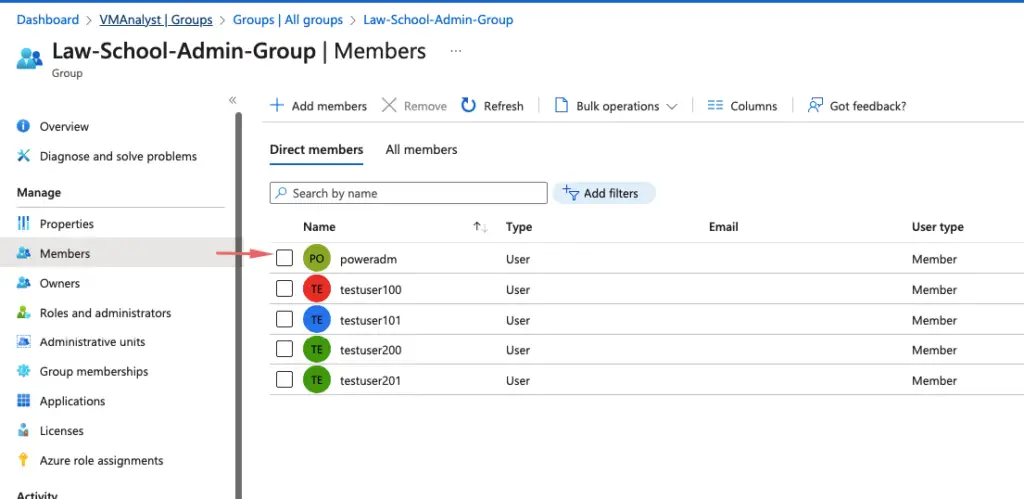
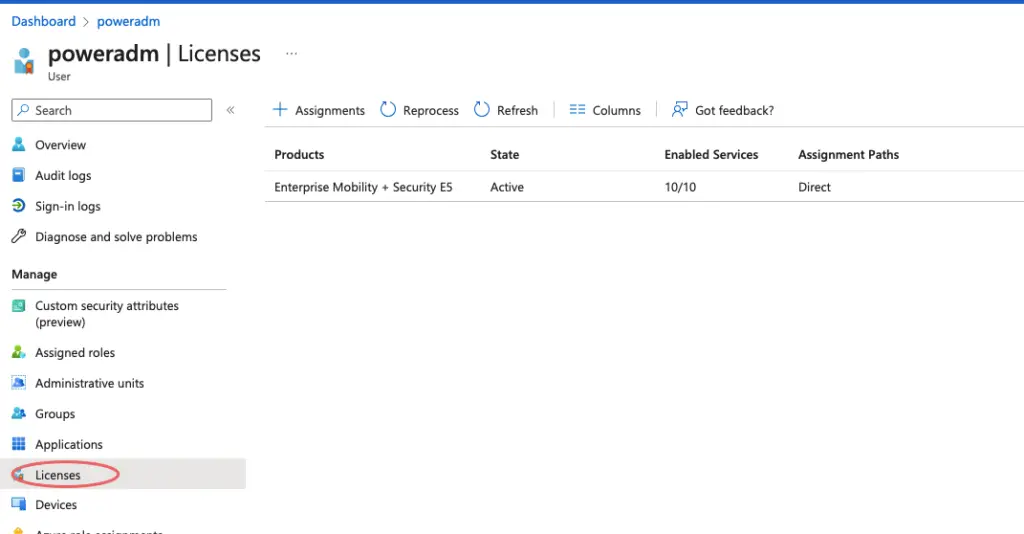
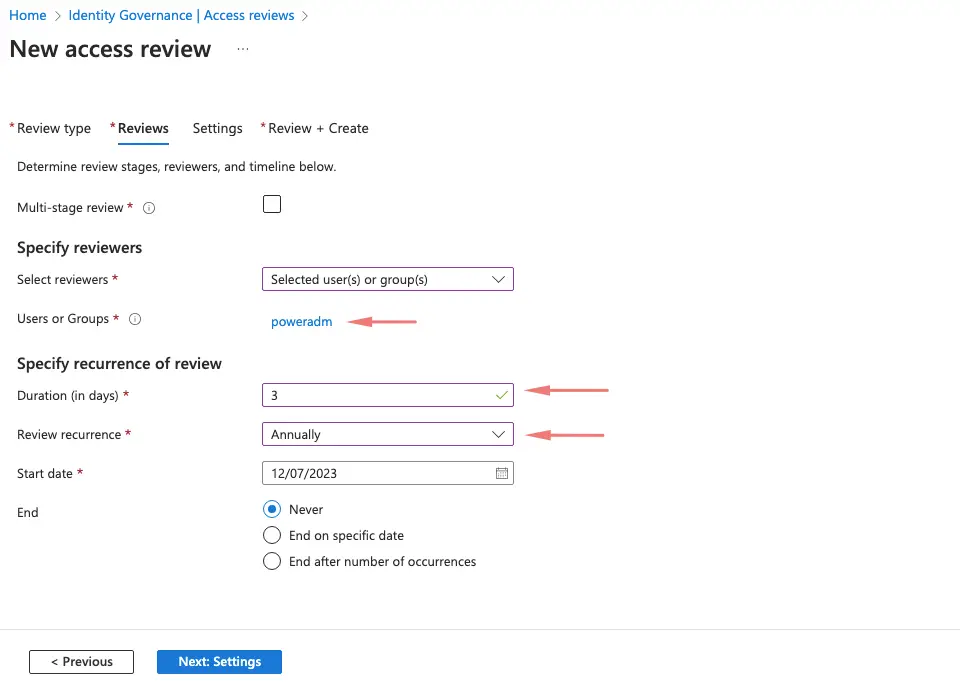
We will need an Azure AD P2 license to configure Acces reviews so we will assign this to an administrator user poweradm
Under the Azure portal, search for Identity Governance
Select Acess Reviews > Create New Access Review
Select the group we created
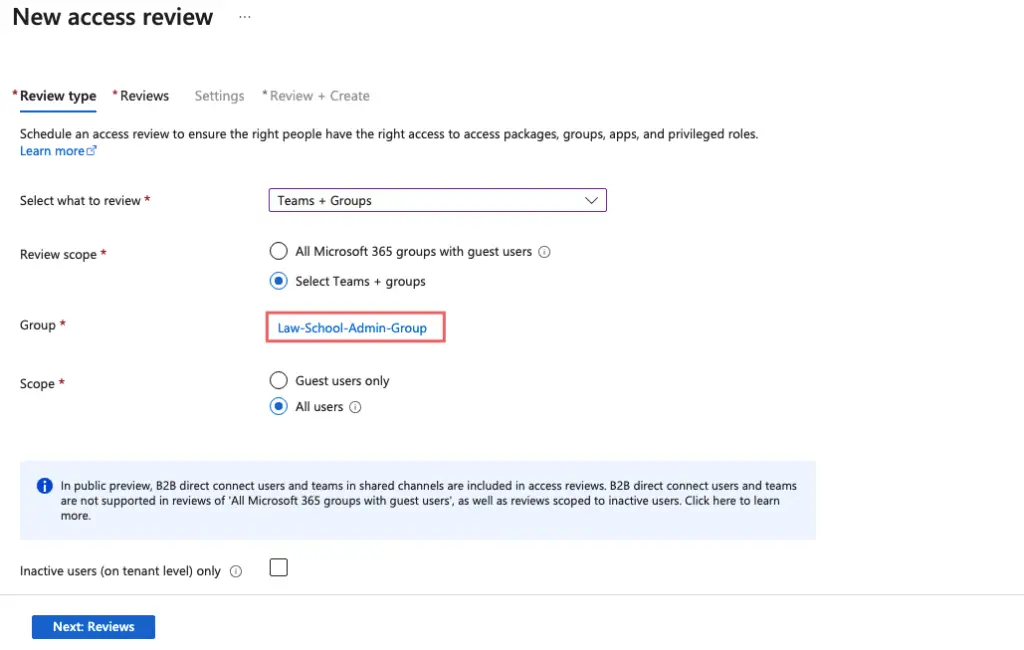
Under the reviewers tab, we will now select the poweradm user that has the Azure P2 license
Click on Review and Create.
Give the review a name as Law-School-Admins
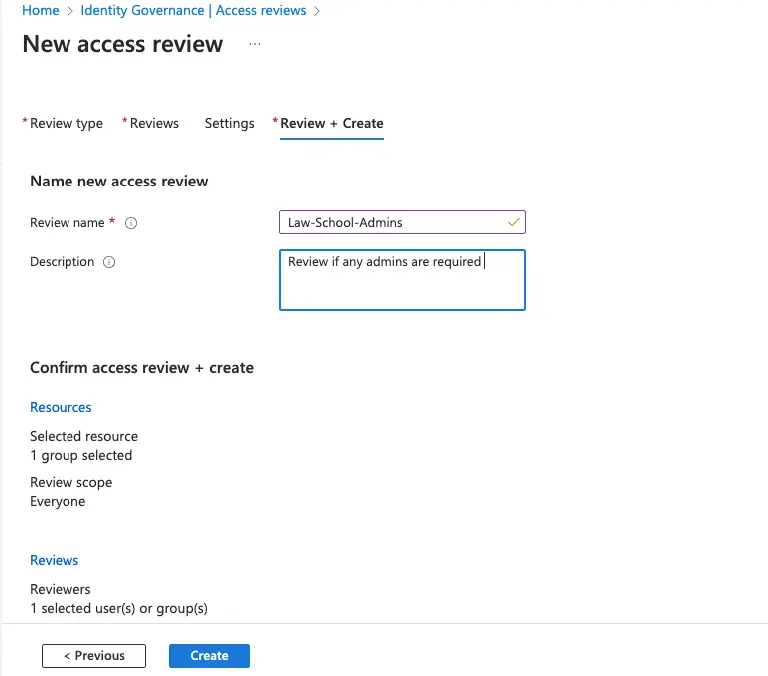
Our access review is now ready.
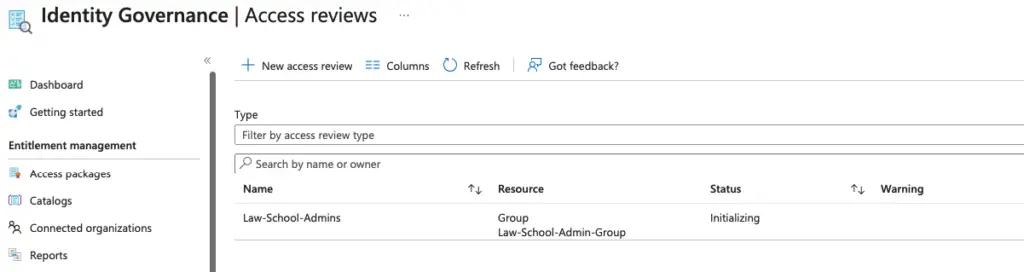
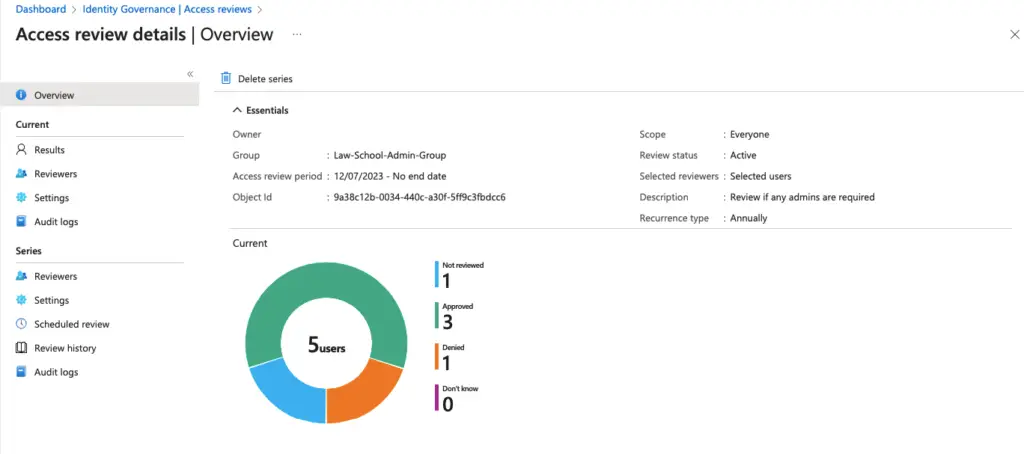
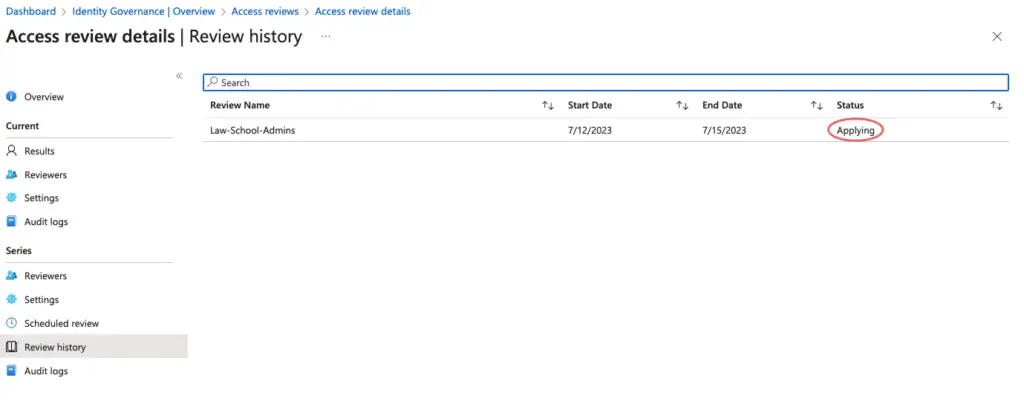
Under the Identity Governance, we can see the status of our access review.
Login to https://myacccess.microsoft.com as poweradm user and we can see review waiting under Acces reviews
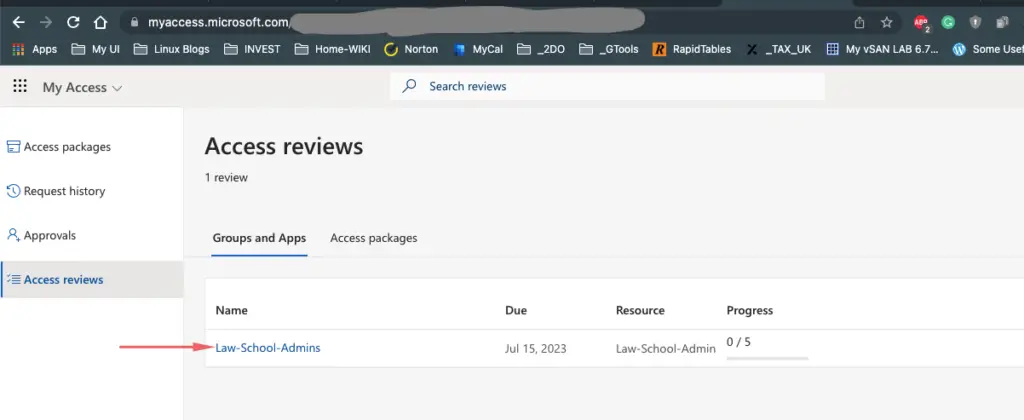
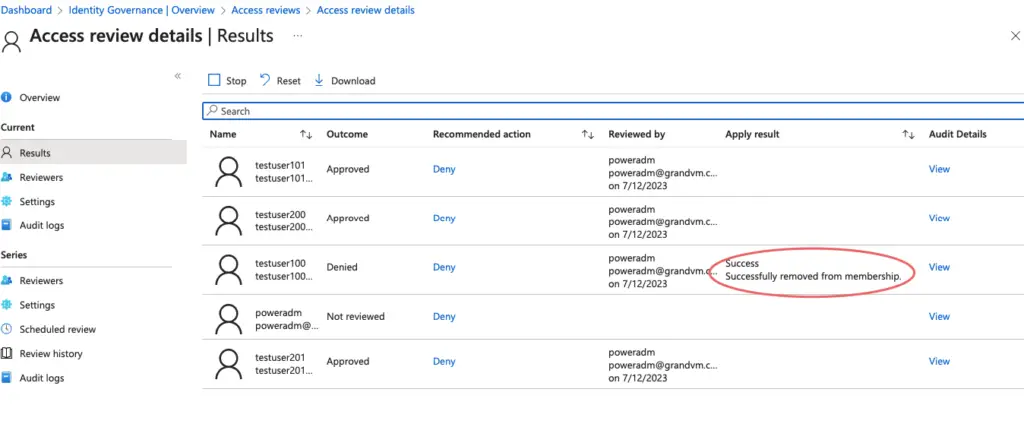
Our entire list of users is listed so we will pick the user that needs to be kept in the group and revoke access to users who no longer need to be part of the group.
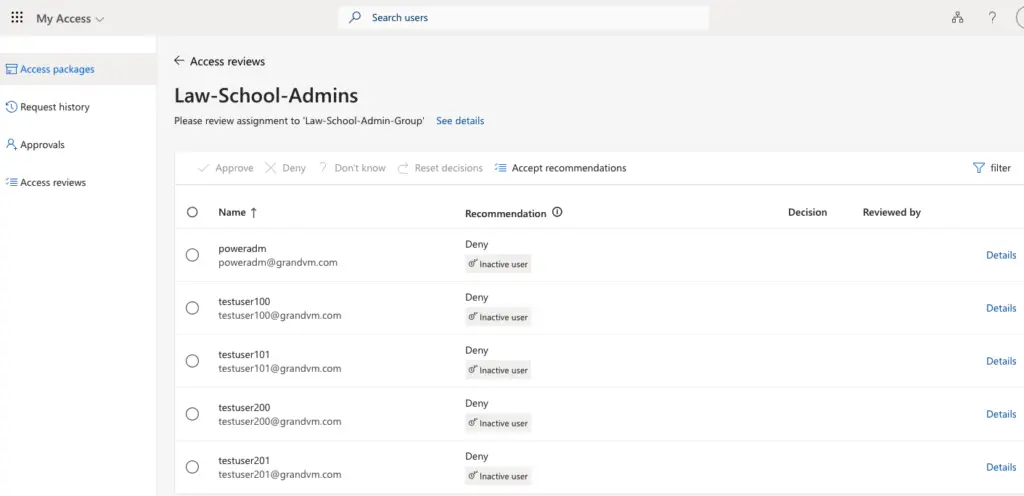
We will revoke access to “testuser100” as shown by clicking the Deny button.
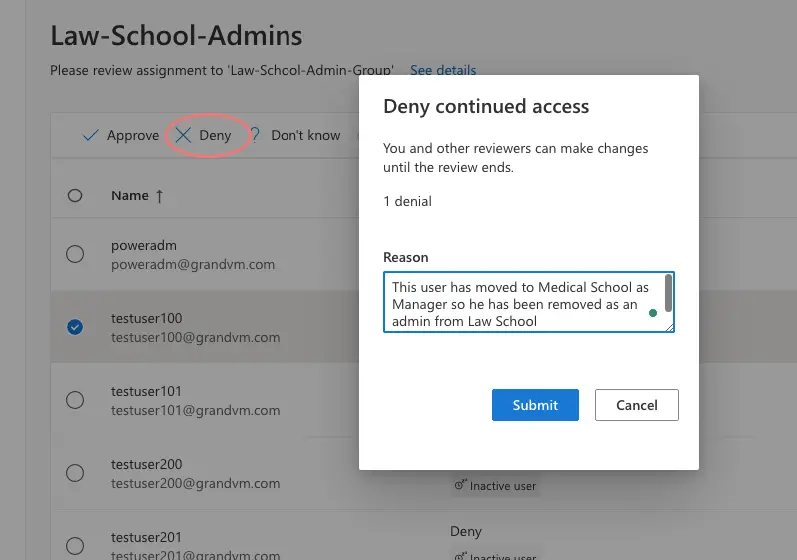
All other users are valid admins so we will just click on Approve button.
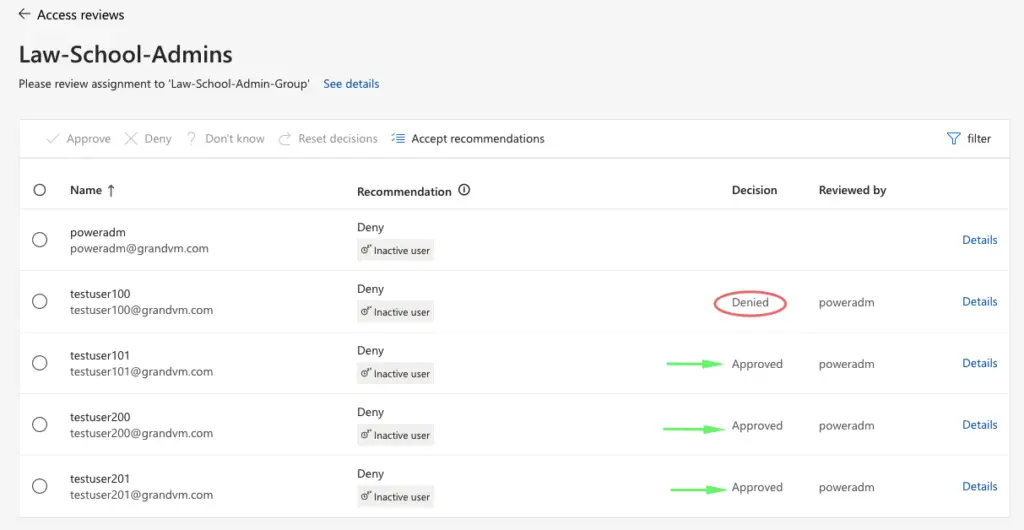
Finally back in the governance, we can see the current status.
Under Access review settings, we will now auto-apply results to resources to ensure the denied users are removed automatically
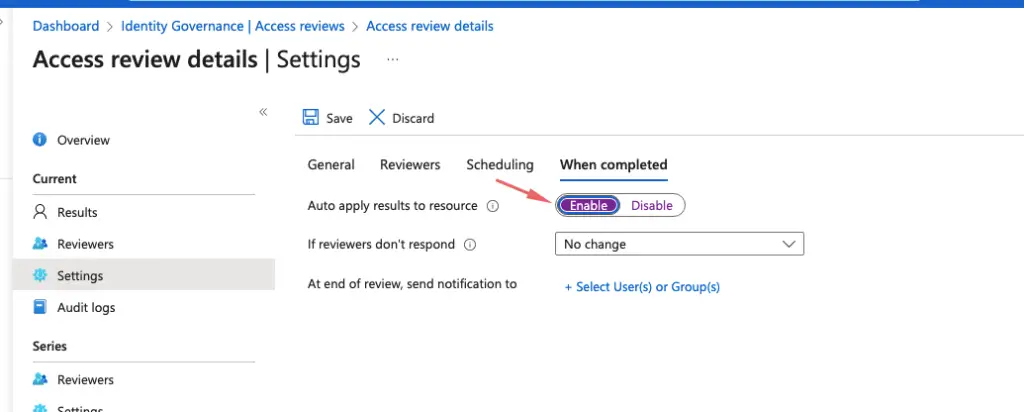
The access review policy is applied
Our testuser102 user is finally removed from our Groups.
The results pane will show the status of the removal.
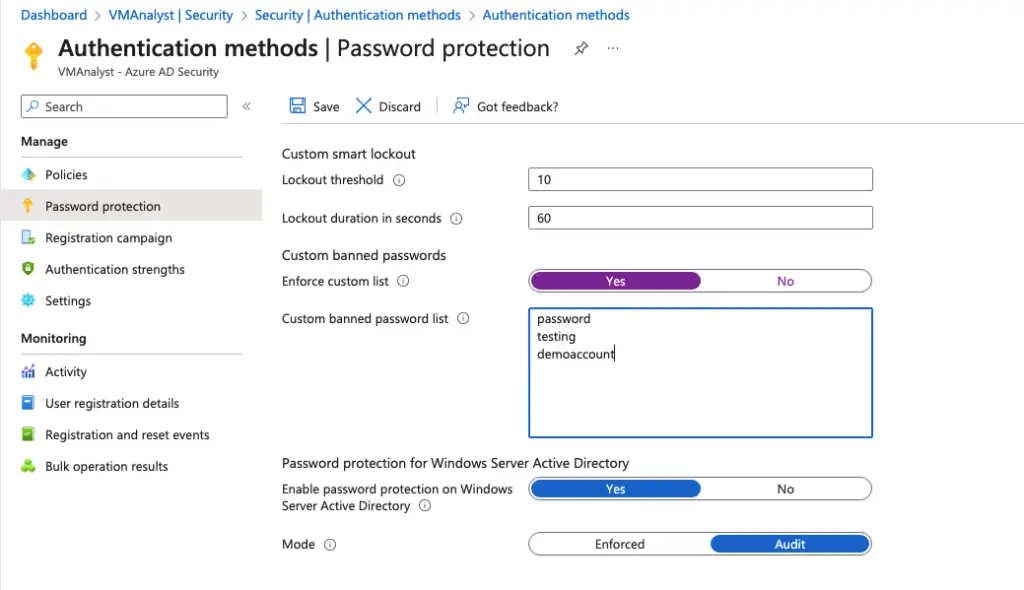
Azure AD password protection
Another useful feature we can turn on that will prevent users from using common passwords out there.