The default encryption attribute of our Active directory domain is set to use only RC4.
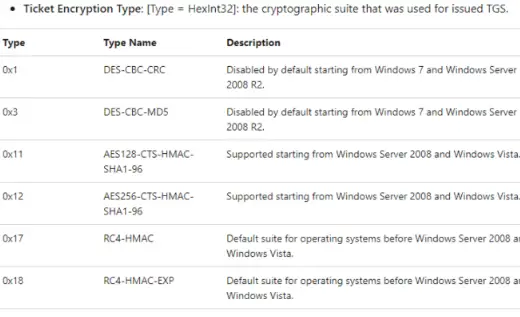
vCenters/Appliances will fail to log in to a domain where RC4 is disabled following the rollout of the November 2023 KB article – KB5021131. This KB will set AES as the default encryption type and will force applications to use a much more secure AES algorithm for Kerberos encryption than using the RC4.
This is the default behaviour prior to the KB being applied.
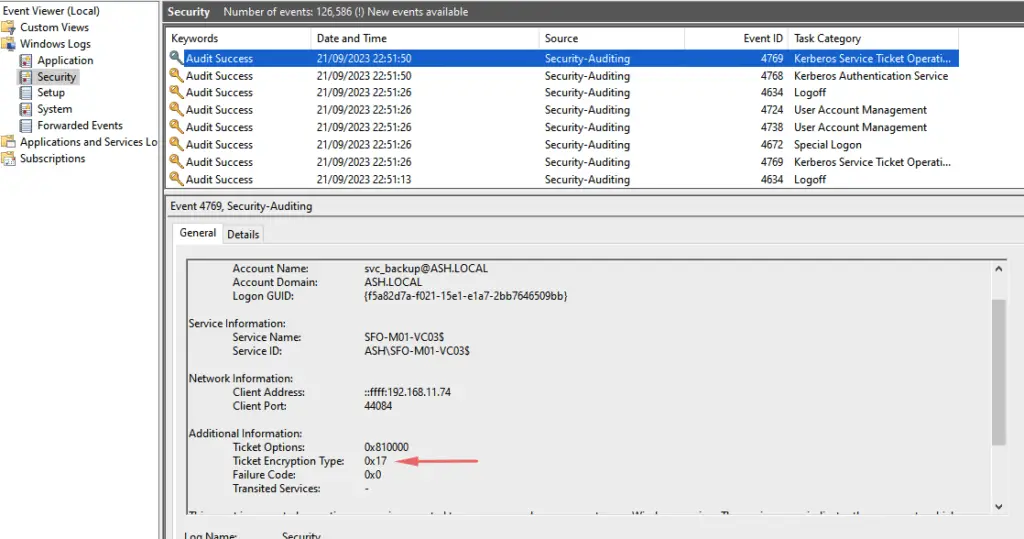
PS C:\Users\Administrator> get-ADComputer -Identity sfo-m01-vc03 -properties *
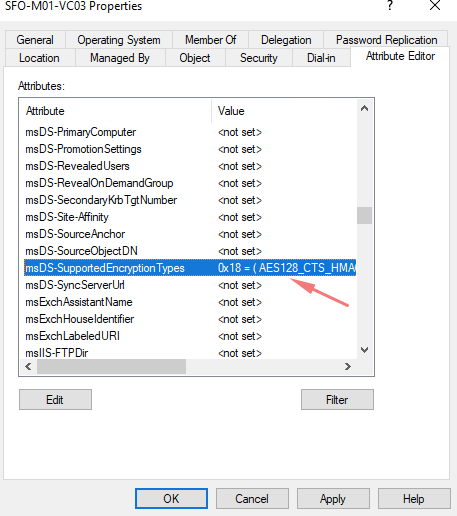
Right Click vCenter Computer Object Properties > Attribute Editor and set ms-DS-SupportedEncryptionType to 24 or via PowerShell using
Set-ADComputer -Identity sfo-m01-vc03 -KerberosEncryptionType RC4, AES128, AES256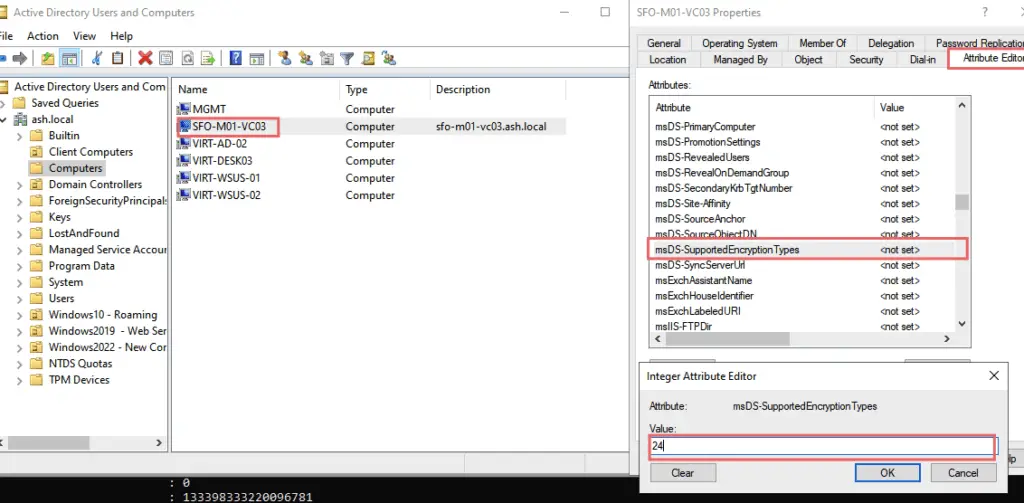
Our Supported Encryption Type is set to AES 128
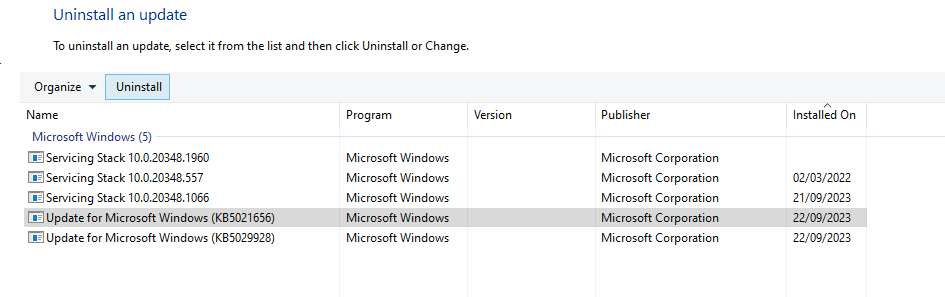
Patch the domain controller with the above KB
Log off from the vCenter and log back in.
Under the security section of AD logs, search for event IDs 4769 and 4768 and as expected our vCenter shows Ticket
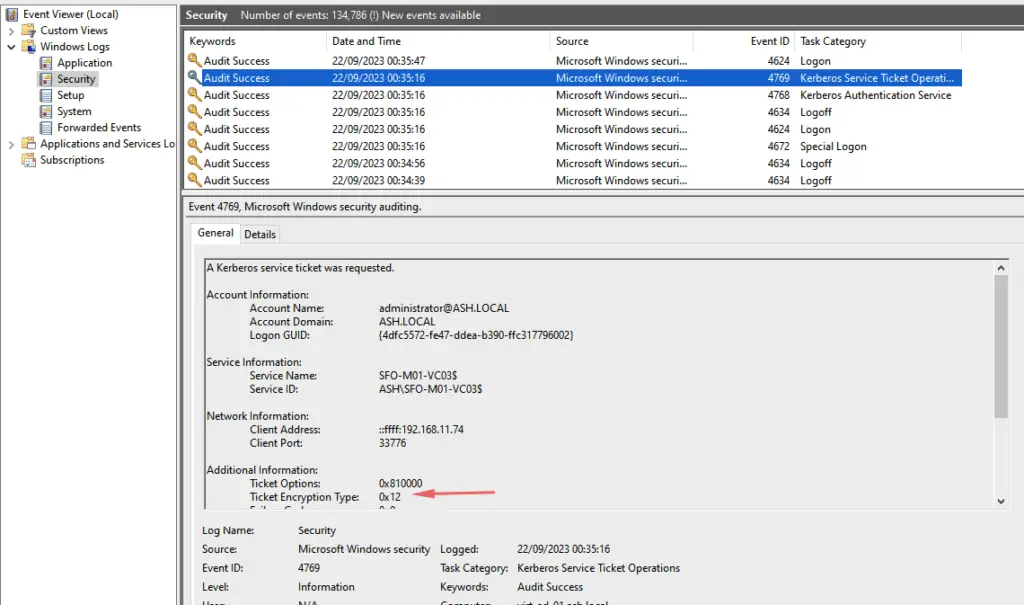
We can see 0x12 in security event 4769 which confirms the switch to AES.
References
KB5021131: How to manage the Kerberos protocol changes related to CVE-2022-37966

