In this blog, we will be going through switching over to Active Directory over LDAP on a vCenter currently configured to authenticate via Integrated Windows Authentication(IWA) which is the default option used by several vCenter admins. Whilst Active Directory will still be supported for authentication, starting with vSphere 7.0, federated Identity is the strong authentication and encryption type supported for all authentication use cases with AD FS thus it is recommended to use AD over LDAP or Identity Federation with AD FS for authentication for vCenter.In our setup, we will aim to set up encrypted LDAP( ldaps://) on our vCenter configuration
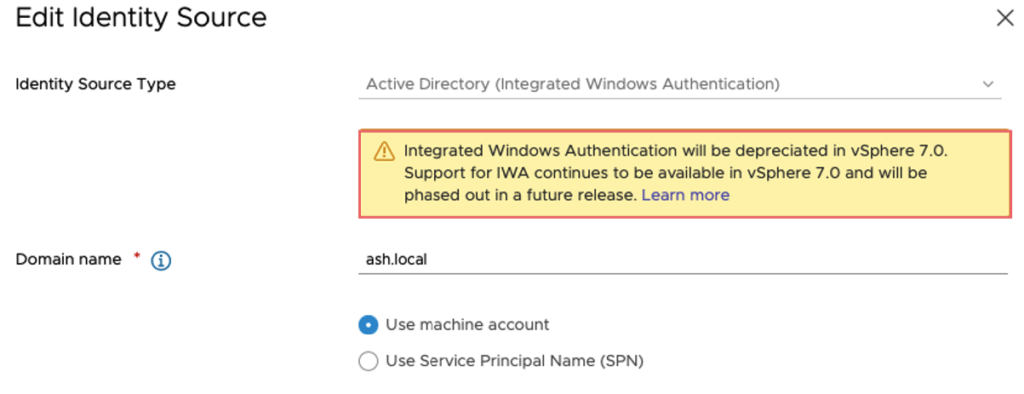
If we check the existing AD IWA we can see the warning message that the feature is going to be depreciated in future releases as per the VMware KB
We will need to confirm that our current AD domain is set up to use LDAPS. On the terminal window, on the domain controller run ldp.

Under the connection tab, Click connect give in our domain or server name, set the port to 636 and SSL option.

If the configuration returns an output, LDAPS is working on our AD Setup.

Login to our vCenter to confirm the current identity source is set to IWA.
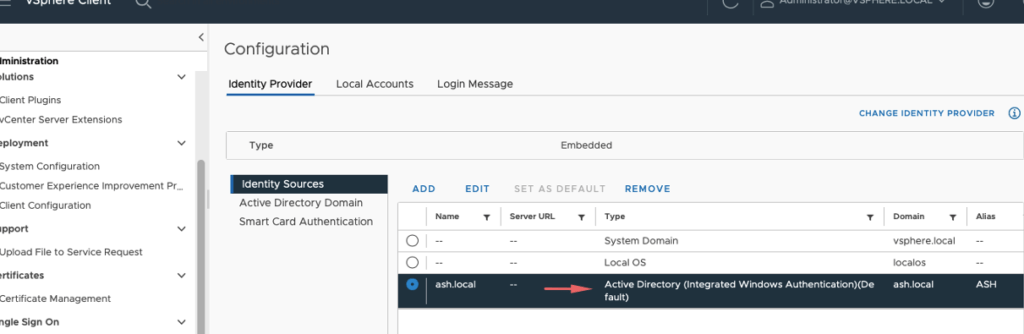
Validate if vCenter is joined to the domain.

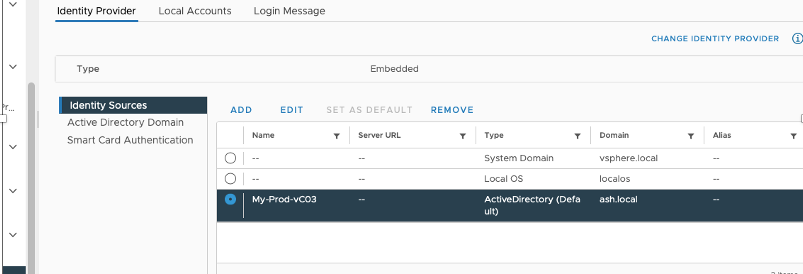
To add the new LDAPS source, we will go to the Identity Provider tab > Identity Sources > Select the IWA and choose Remove Identity Source.

Once removed, again under the Identity Provider tab > Identity Sources > Choose to add a new identity source and choose Active Directory over LDAP.
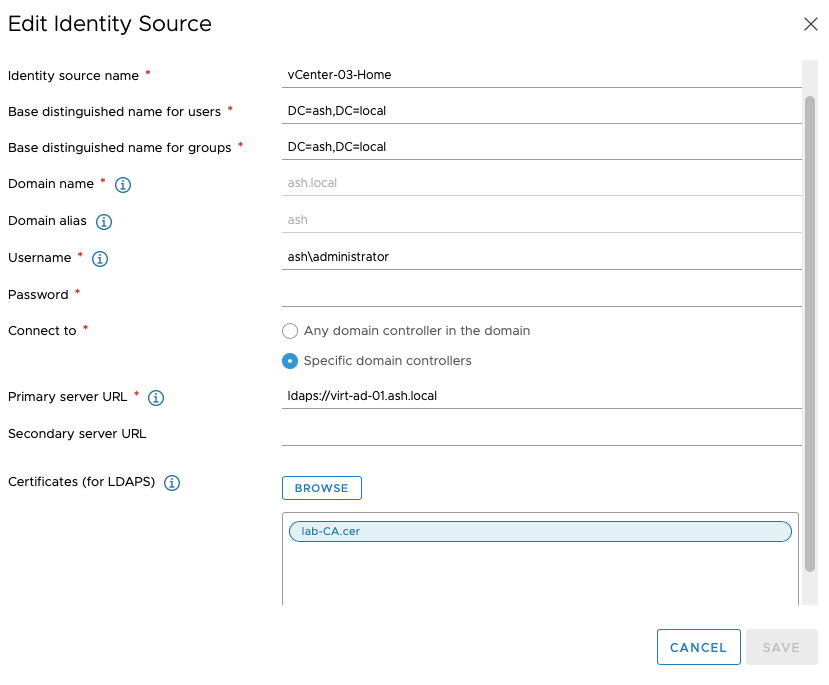
Provide all these details and click Add to complete the wizard.
- Identity name of source – Just add a friendly name
- Base DN: This is the level container at which search in AD will start searching for users or groups all AD or we can choose to select sub OU to limit the AD searches.
- Domain Name: Our domain FQDN
- Domain Alias: Netbios Name
- Under the domain controller tab, choose the primary server URL as ldaps://virt-ad-01.ash.local or choose the option to leave it connected to any domain controller in the forest.
- Certificates for LDAPS – Add the CA cert for LDAPS as this should trust any cert issued by the CA on my domain controllers
Choose the option to set the Identity Provider as our default authentication mechanism.
Login in via a user with access to vCenter
The users are authenticated and the certificate is being verified as seen in the websso.log file

You can also run below PowerShell command below to check the reporting date and time from the active directory domain controller
Get-ADComputer -Identity sfo-m01-vc03 -Properties *
