In this series, we are going to replace the self signed certificate with an enterprise CA cert.
Blog Series
- Installing NSX-V 6.4
- Configure Controller Nodes and enable CDO mode in NSX-V 6.4
- One Page View of all NSX-V commands
- Configure VXLAN and Prepare ESX hosts for VXLAN traffic
- Configure the Transport Zone and Logical Switches
- Configure Distributed Logical Router
- Configure Edge Services Router (ESG)
- Verifying VXLAN Connectivity
- Regenerate Self-signed Certificate on NSX-V
- DLR VM SSH Access
- Backup NSX-V Manager
- Dynamic routing with OSPF in DLR
- Dynamic routing with OSPF in ESG
- VMware NSX Edge Load Balancer
- VMware NSX Edge Load Balancer SSL Offloading
- NSX-V Firewall & Microsegmentation
- NSX-V Firewall Service Composer
This post assumes you have an Active directory CA installed and web enrollment working as we will need it to complete the exercise
Installing the Certificate on NSX-V
Go to NSX Edge – Configure – Certificates tab – CSR Actions to generate a certificate
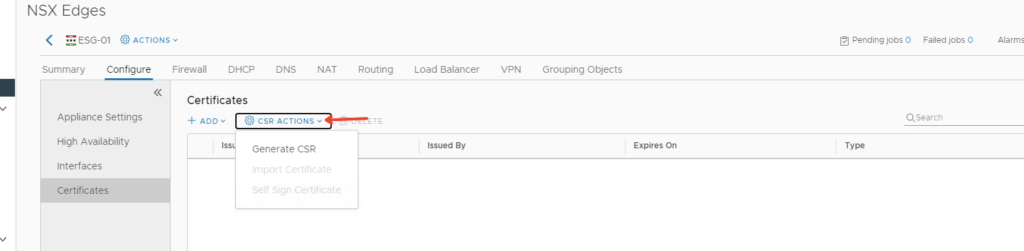
Generate CSR

Double click the EGS-01 cert we generated
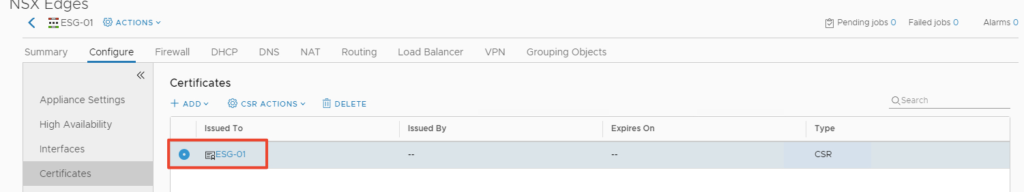
Copy the Cert request

Generating a certificate from Central CA dc.ash.local
Go to chrome browser and browse to your web enrollment page as shown
http://localhost/certsrv/
Click Request certificate

Copy the Cert Request entry we generated earlier and paste here and submit an advanced certificate request.

Click Download Certificate

Open the .cer file in notepad

Copy all the contents

Click Import Certificate on CSR Actions

Copy everything from our notepad in here and click OK
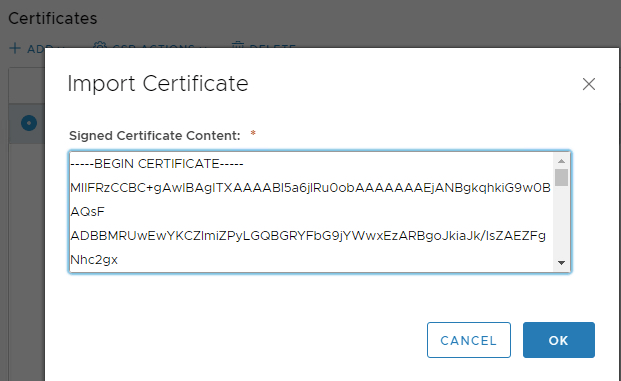
We have succesfully changed our certificate to our enterprise CA


