In this blog, we will be focussing on enrolling our Windows 10/11 devices to our Intune by creating the necessary compliance policies for our company standards.
Prerequisites for enrolling devices to Intune
There are a few prerequisites which are required to enrol the devices.
- Once the Intune setup is done, MDM authority should be set to Microsoft Intune. This can be verified by logging on to the Intune Portal and navigating to Tenant Administration> Tenant details
- Microsoft Intune subscription should be assigned to the user or group.
- The following operating systems are supported for Intune:
- Android
- iOS
- Linux
- macOS
- Windows
Configure Azure Active Directory Automatic Enrollment
Follow the below steps to configure Automatic MDM enrollment from the Azure portal.
Access the Intune portal and navigate to Devices > Enroll Devices > Windows Enrollment to customize the MDM user scope for a specific set of AD groups or for all users. For MDM, choose the “All” option, while for MAM, select “None” as the setting.
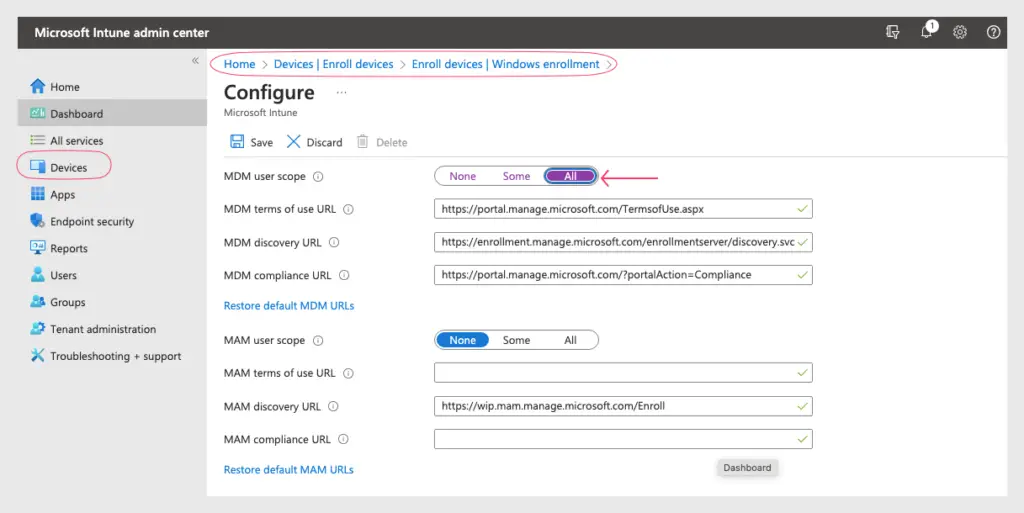
Another way to configure the settings is via the Azure Portal > Azure AAD >Mobility (MDM and MAM) > Microsoft Intune
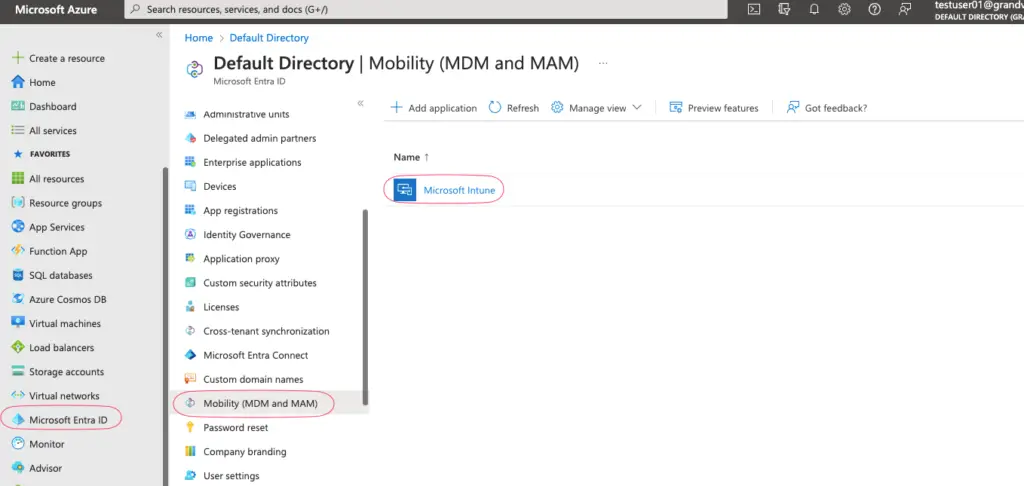
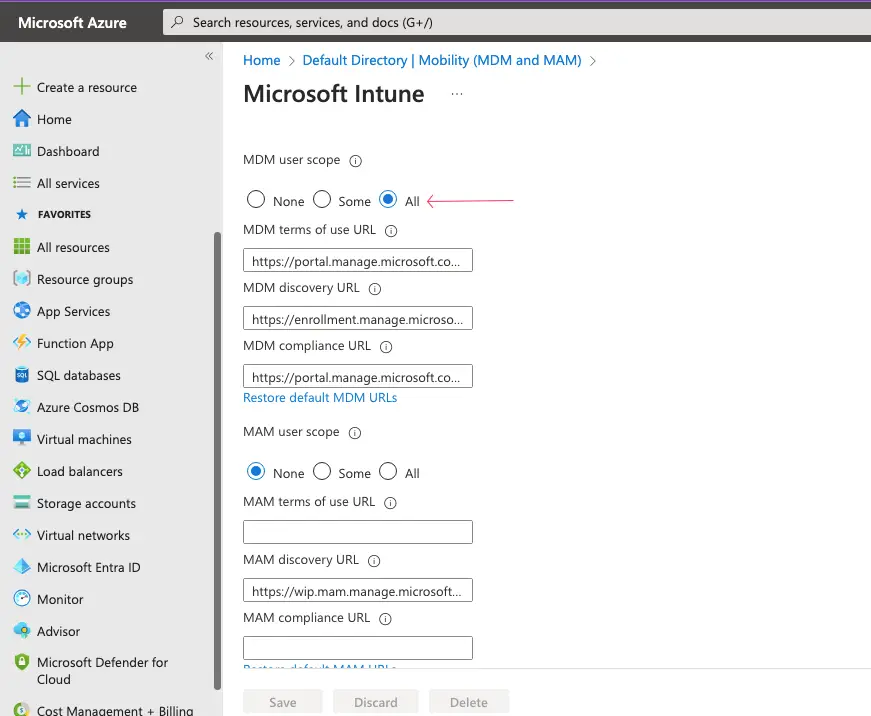
Configure MDM user scope to a few AD groups or All users. In this example, we will select All.
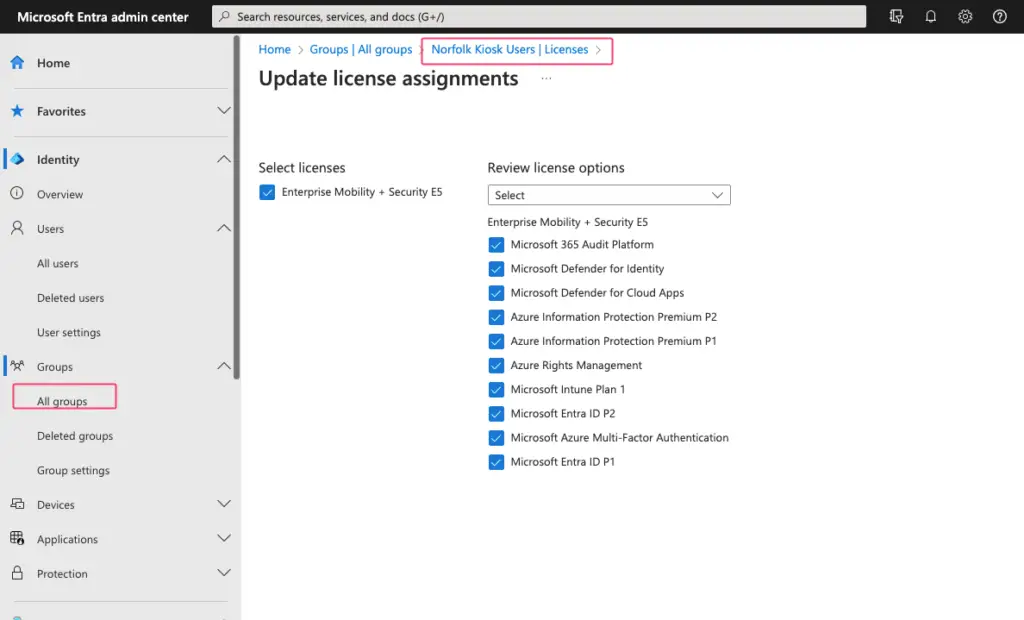
Then go to Azure Active Directory | Users. Then go to the user or group you going to use for the enrollment and verify our Intune license is assigned.
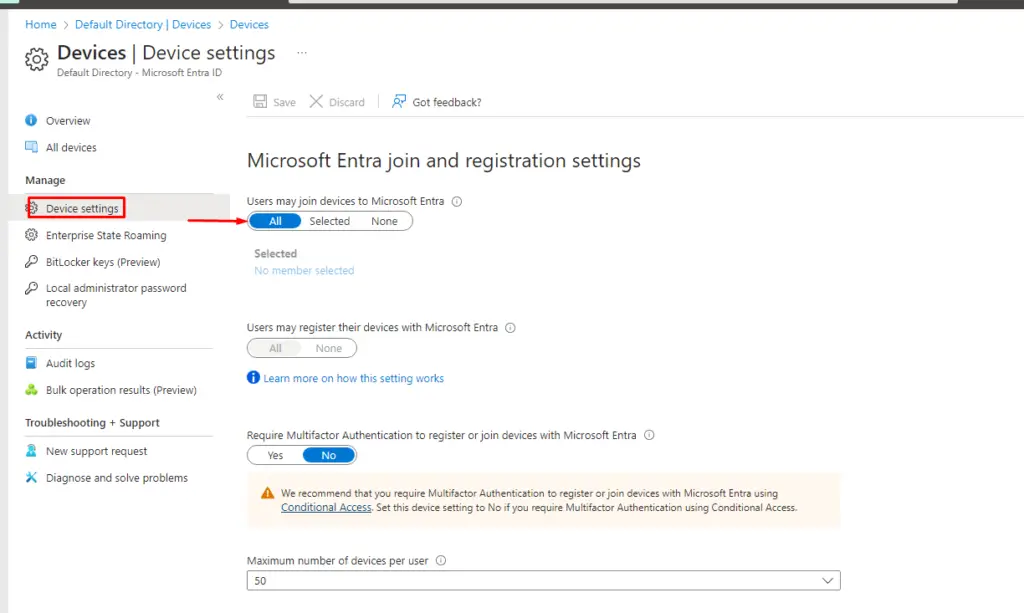
Then go to Azure Active Directory | Device Settings. Select the option to allow all users to join devices to AAD.
Creating Compliance Policy for Windows Devices
Compliance Policy for Windows 10 helps us to protect company data, the organization needs to make sure that the devices used to access company apps and data comply with certain rules and standards.
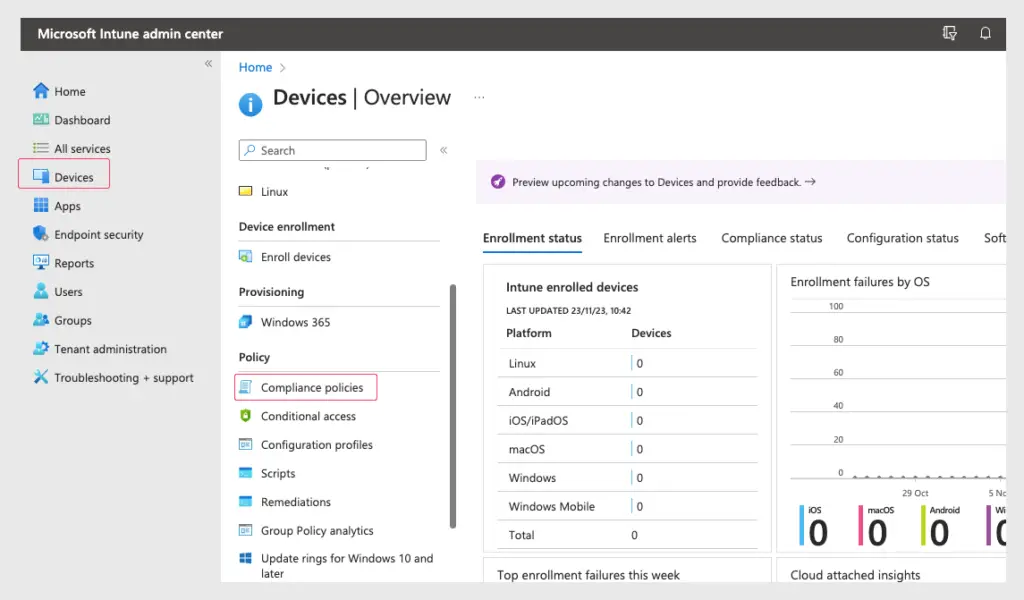
Navigate via Endpoint Security – Compliance Policies.
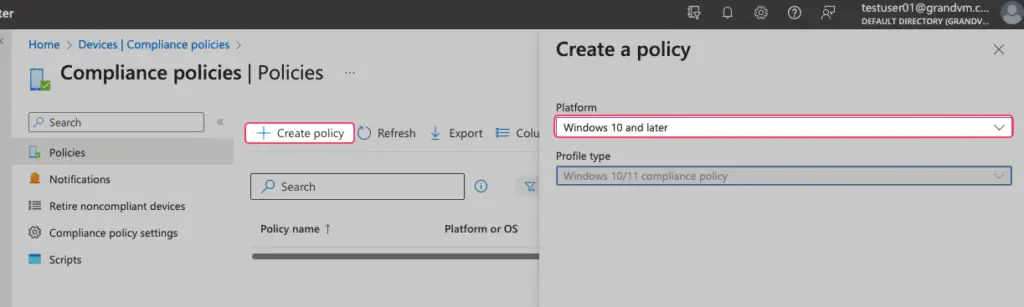
Click on the Create Policy button to start the Intune compliance policy creation process and choose the profile type to be Windows 10/11 compliance policy.
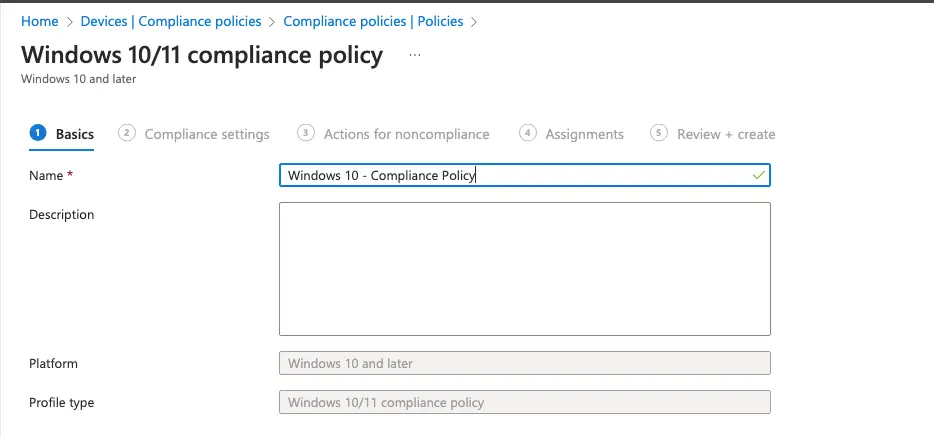
Give a name and description of the compliance policy.
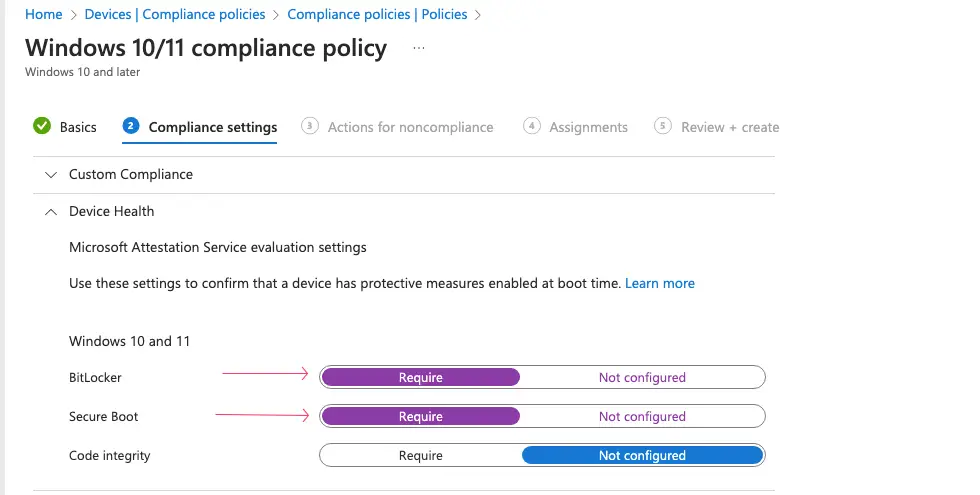
Intune Compliance Policy – Device Health Checks
Under the compliance settings, we can now set policies as per our security standards. From the Device Health check category, I’ve checked BitLocker and Secure Boot to be enabled on the device
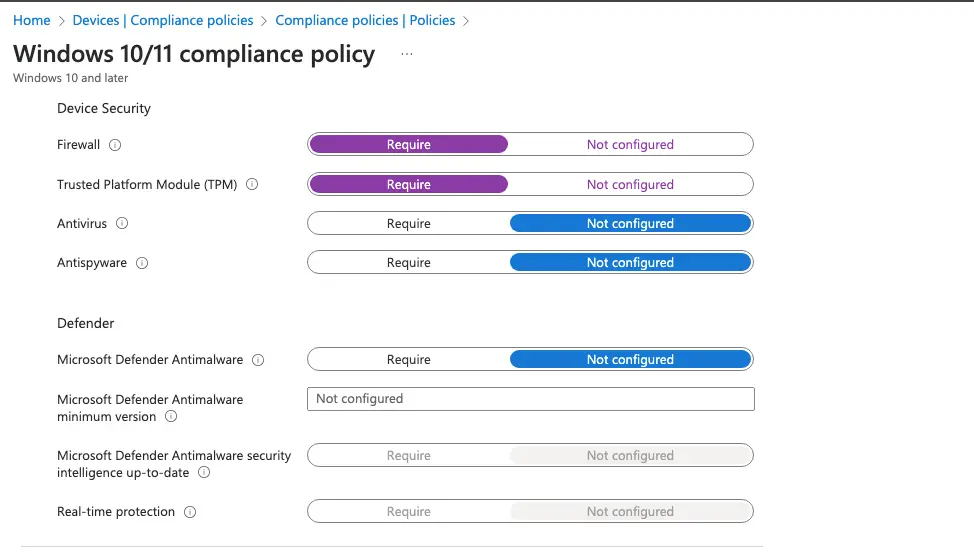
From the Device Security category, I’ve checked the device needs firewall and TPM to be enabled on the device
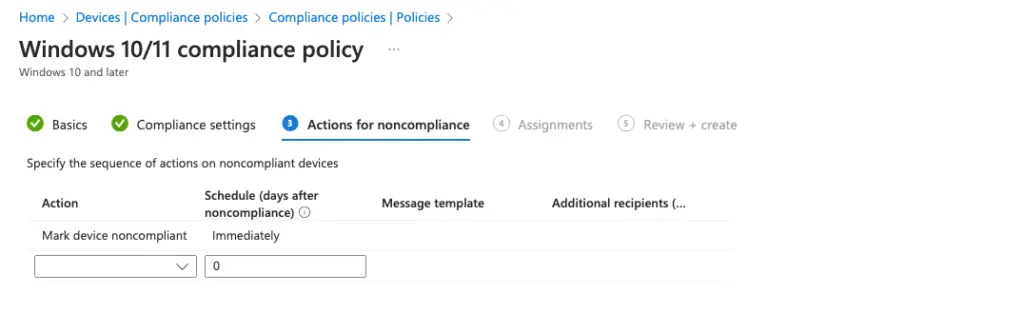
Select the maximum allowed days the device can stay noncompliant.
Apply the deployment of compliance policy to the Azure AD dynamic device group we created for our Norfolk Eye Hospital.
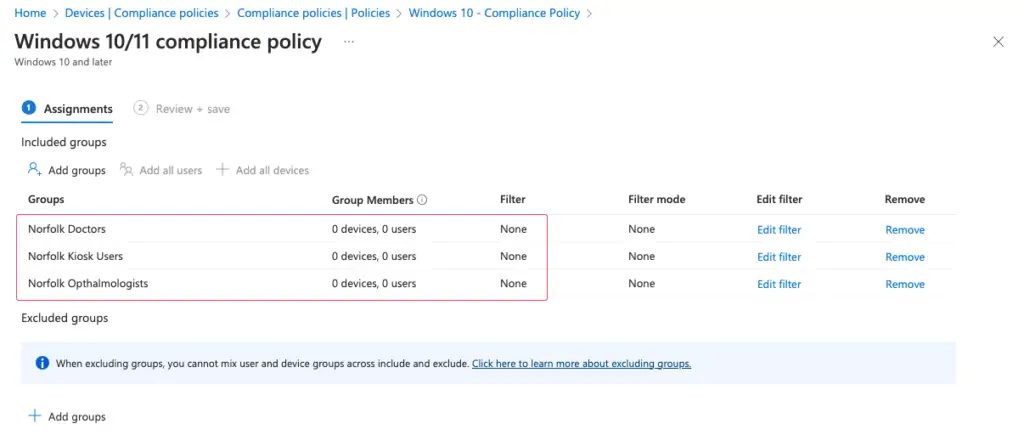
Likewise, if we wish to, we can as well apply the policy to All Users as well. In this example, we will still will stick with Dynamic Groups.
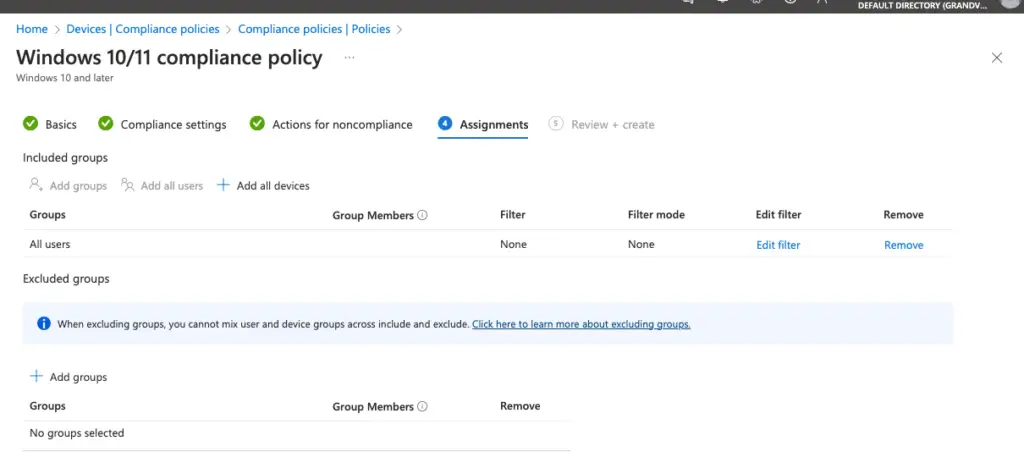
Finally, Click Review and Create
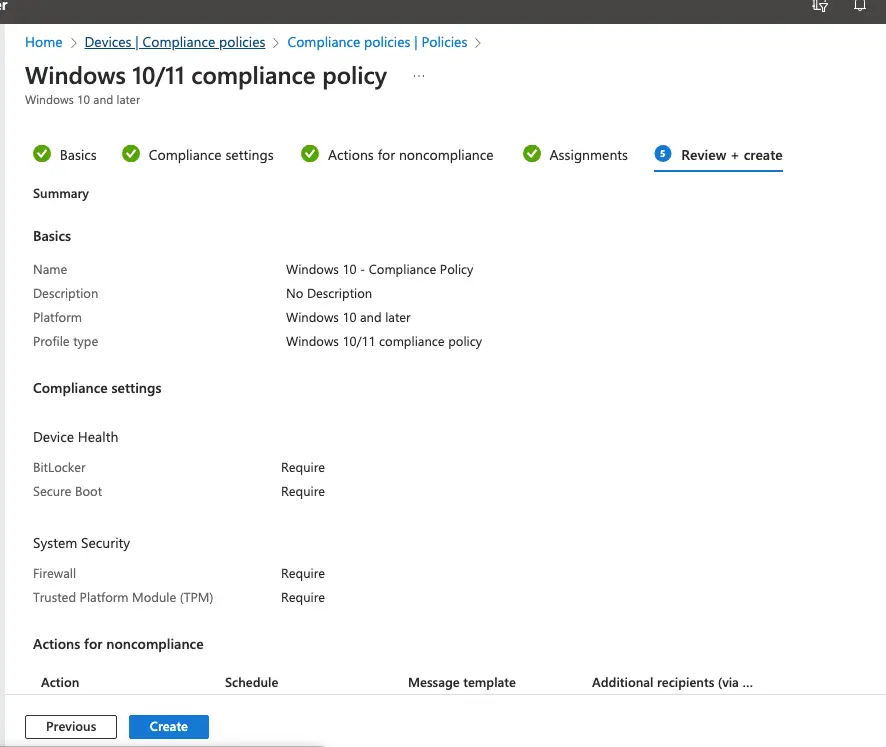
Our compliance policy is now ready.
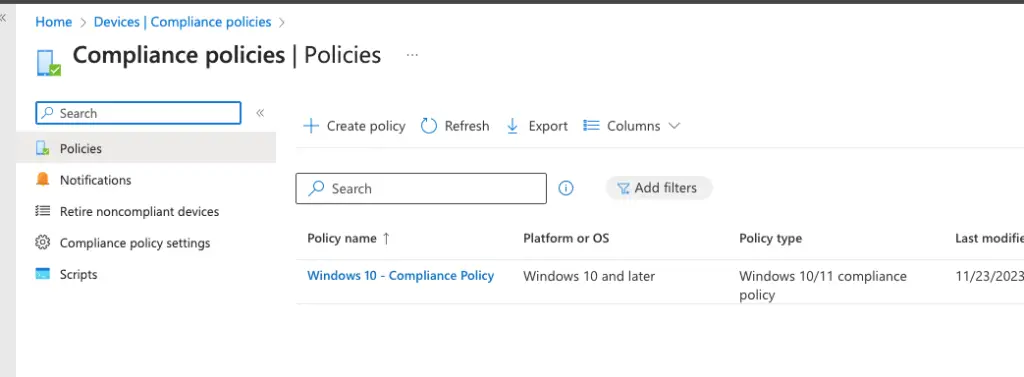
In the next blog, we will enroll our Windows 10/11 device to Intune.

