Micro-segmentation allows NSX-V to build fine-grained traffic filtering without having to create complex routing rules. The ultimate aim of micro-segmentation is to create application-centric workloads that are easier to manage using software-based security rules and security tags.
Blog Series
- Installing NSX-V 6.4
- Configure Controller Nodes and enable CDO mode in NSX-V 6.4
- One Page View of all NSX-V commands
- Configure VXLAN and Prepare ESX hosts for VXLAN traffic
- Configure the Transport Zone and Logical Switches
- Configure Distributed Logical Router
- Configure Edge Services Router (ESG)
- Verifying VXLAN Connectivity
- Regenerate Self-signed Certificate on NSX-V
- DLR VM SSH Access
- Backup NSX-V Manager
- Dynamic routing with OSPF in DLR
- Dynamic routing with OSPF in ESG
- VMware NSX Edge Load Balancer
- VMware NSX Edge Load Balancer SSL Offloading
- NSX-V Firewall & Microsegmentation
- NSX-V Firewall Service Composer
Service Composer
Allows us to select multiple objects in our vCenter at once and apply firewall rules, endpoint protection rules and network introspection using Security Groups and Security Policies.
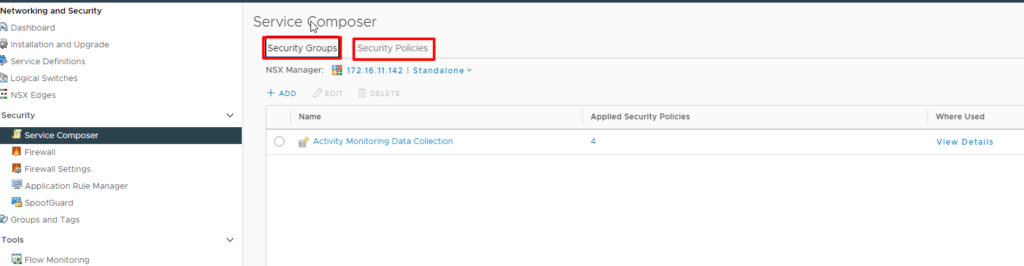
Security Groups
SG’s allows administrators select VM’s based on its properties
eg : Web Security Group, App Security Group
Security Policy
Security Policy determines how security groups are going to be protected and these are typically set of rules.
| Rule ID | Name | Type | Source | Destination | Service / Protocol | Applied to |
| 1 | Rule1 | User | Internet | SG_Web | Https Http | Any |
| 2 | Rule2 | User | SG_Web | SG_App | Moodle App | Any |
| 3 | Rule3 | User | SG_App | SG_DB | mySQL | Any |
| 4 | Default rule | Default | Any | Any | Any | Any |
Security Profile
You can contain firewall rules as well contain network and guest introspection rule within a security profile such as which Antivirus to use and how to apply
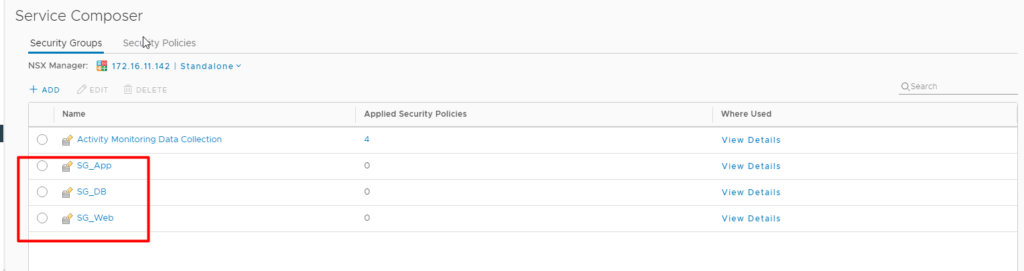
Define Security Group
Before we apply or define security groups, we will need to block the “Default rule”. This needs to done on ESG and DLR

In this we are going to deny SSH traffic on our Web Server and allow Https traffic to our web server

If we wish to create dynamic membership, such as VM name, you can define it here

Under objects to Include add Web-Servers Logical Switch

Skip the objects to exclude if any

Review and click finish to complete

We will have a similar view as shown below.

Similarly we can add Security Groups for our App and DB servers
Go to Security Policies

Add a Name as “Allow Web Traffic”

We are going to skip Guest Introspection Services

We will need to define firewall rules here and attach our Security Groups to Security Policy

Add Firewall rule and Name it as Allow WebServer Traffic
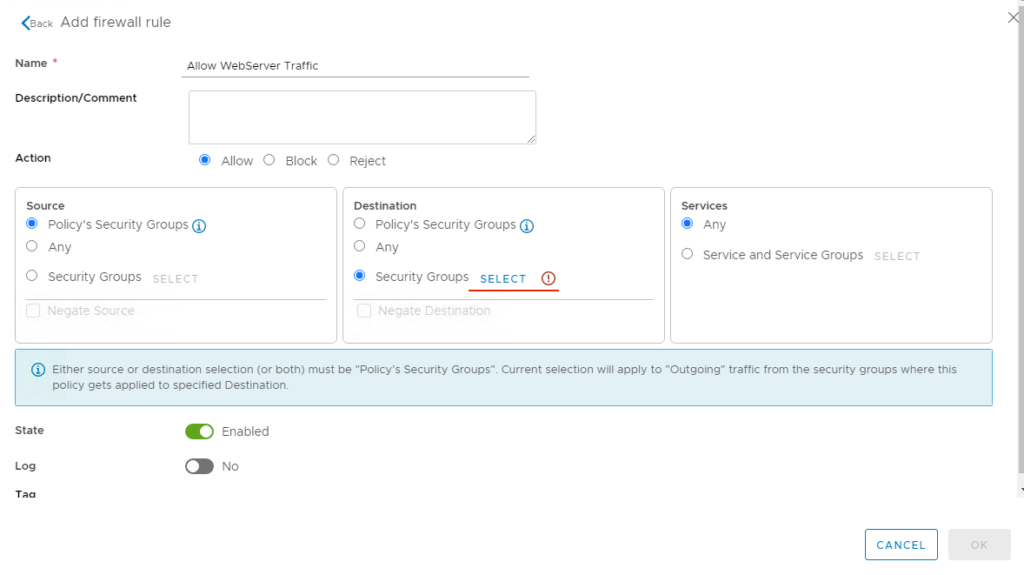
Go to destination tab and our web security group SG_Web
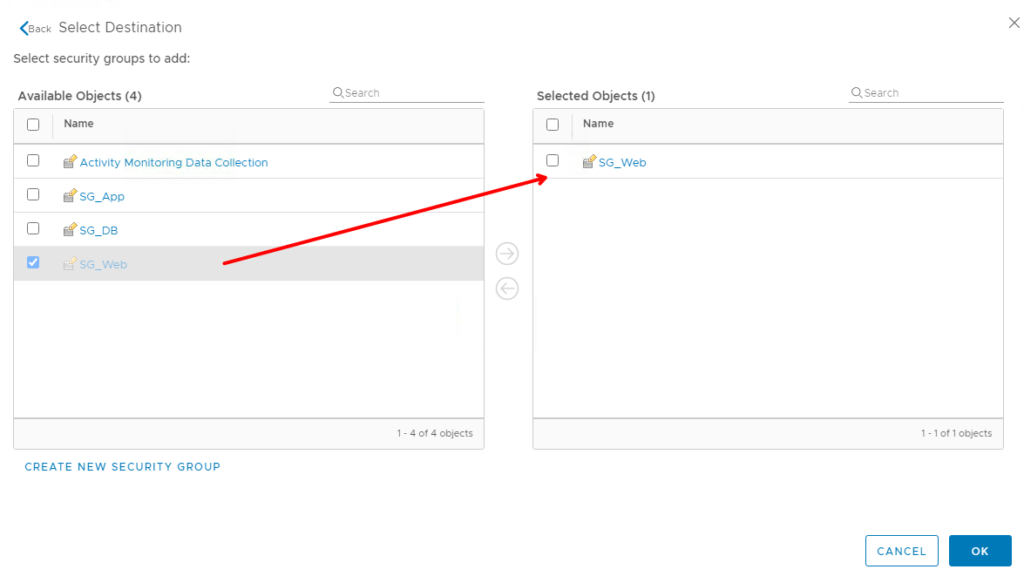
Under Services tab – Define https and http services
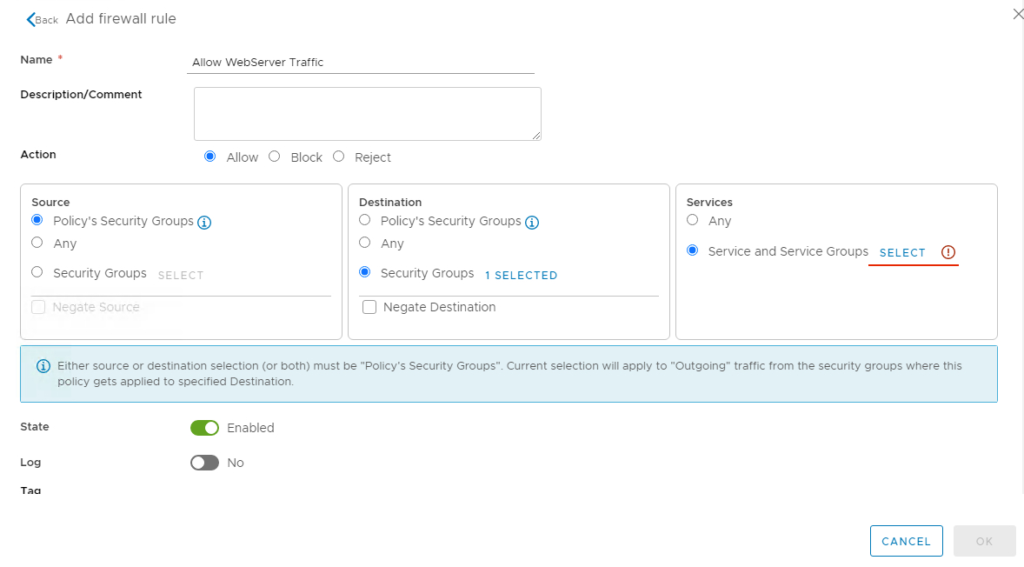
Add http and https service

Ensure State is enabled and Click OK to proceed
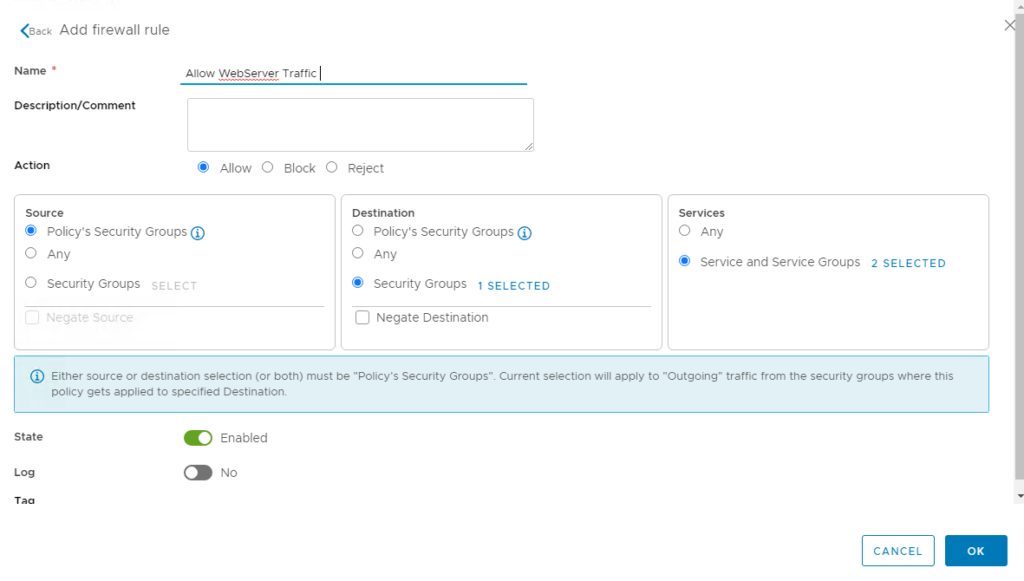
Review and click Finish
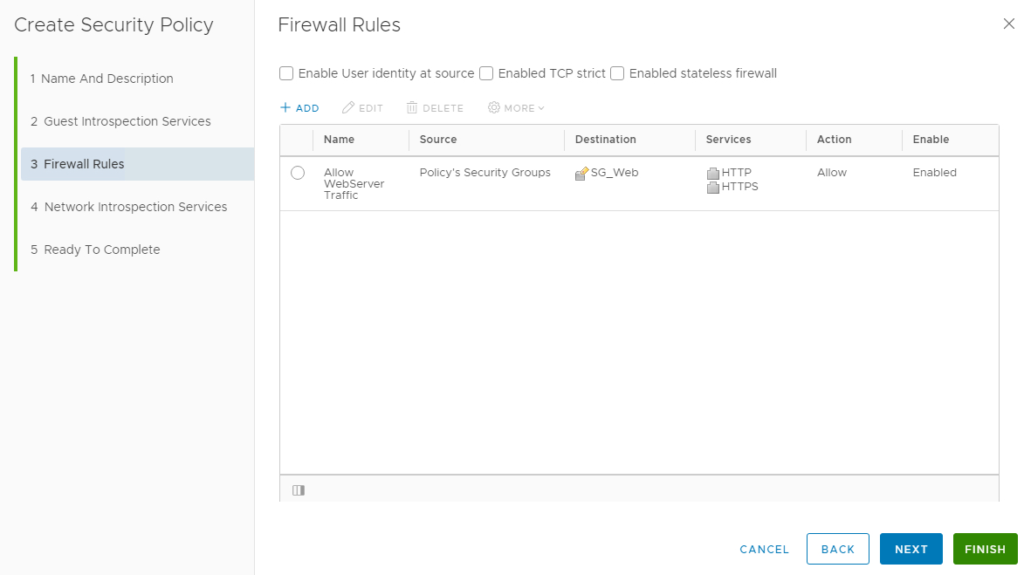
Skip Network Introspection Services

Click Finish to complete

Once the Security Policies are created we will have an entry as below
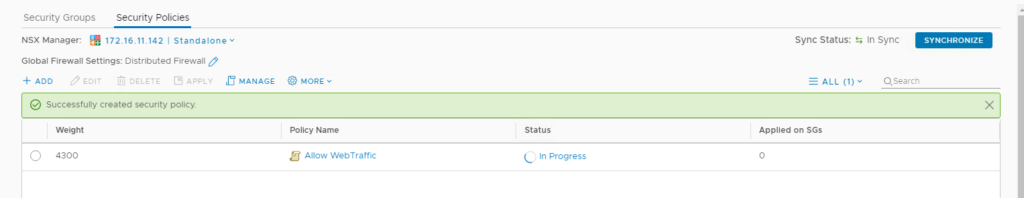
We have more step to do here, Click on the Security Policy and Click Apply button as shown
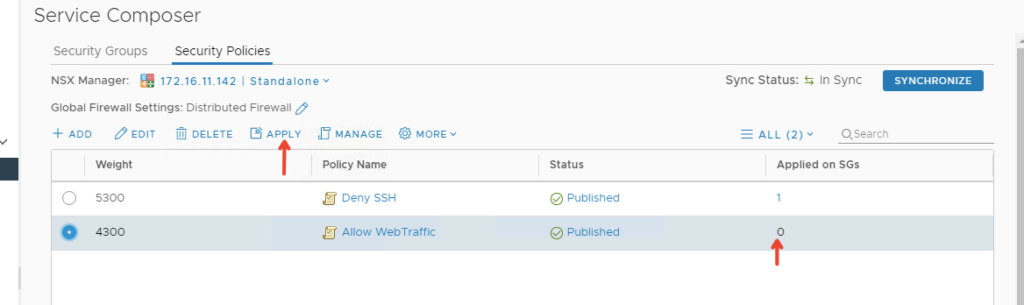
Apply the policy to our Security Group SG_Web

Once its applied under the VM properties we will see our Security membership applied
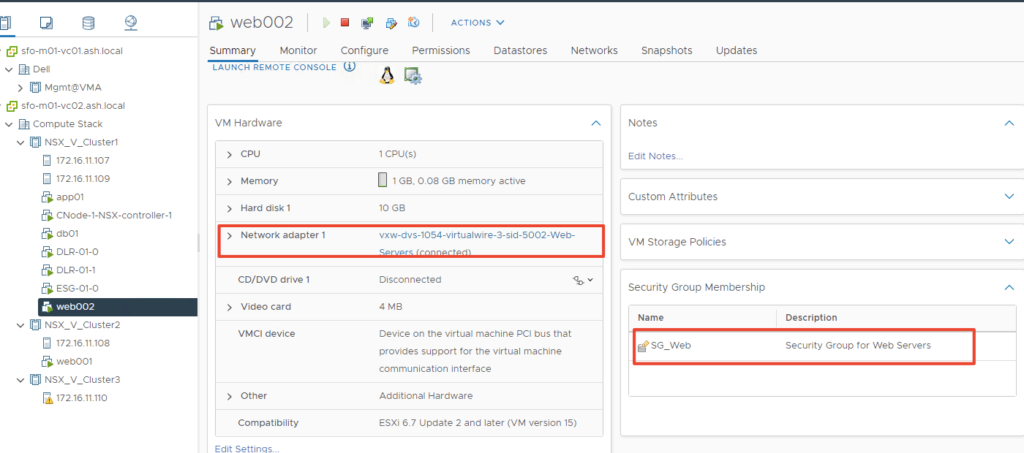
I’ve also added a rule to block ssh traffic so our entire firewall configuration will look as shown below.

Conclusion
In this next series, we wil look into enabling guest introspection services on NSX-V

