Micro-segmentation allows NSX-V to build fine-grained traffic filtering without having to create complex routing rules. The ultimate aim of micro-segmentation is to create application-centric workloads that are easier to manage using software-based security rules and security tags.
Blog Series
- Installing NSX-V 6.4
- Configure Controller Nodes and enable CDO mode in NSX-V 6.4
- One Page View of all NSX-V commands
- Configure VXLAN and Prepare ESX hosts for VXLAN traffic
- Configure the Transport Zone and Logical Switches
- Configure Distributed Logical Router
- Configure Edge Services Router (ESG)
- Verifying VXLAN Connectivity
- Regenerate Self-signed Certificate on NSX-V
- DLR VM SSH Access
- Backup NSX-V Manager
- Dynamic routing with OSPF in DLR
- Dynamic routing with OSPF in ESG
- VMware NSX Edge Load Balancer
- VMware NSX Edge Load Balancer SSL Offloading
- NSX-V Firewall & Microsegmentation
- NSX-V Firewall Service Composer
Provisioning firewalls on the NSX takes the load off the physical routers which otherwise is just participating in sending packets back and forth.
Firewall rules can be applied directly on ESG or DLR
Layers of Firewall Protection in NSX
There are number of components you can add a firewall rule in NSX such as
- Virtual Machine
- VM folders
- ESX / Clusters
- Security Groups
- Logical Switches
Service Composer
Allows us to select multiple objects in our vCenter at once and apply firewall rules, endpoint protection rules and network introspection to this group
Security Groups
SG’s allows administrators select VM’s based on its properties
eg : Web Security Group, App Security Groups
Security Policy
Security Policy determines how security groups are going to be protected and these are typically set of rules.
| Rule ID | Name | Type | Source | Destination | Service / Protocol | Applied to |
| 1 | Rule1 | User | Internet | SG_Web | Https Http | Any |
| 2 | Rule2 | User | SG_Web | SG_App | Moodle App | Any |
| 3 | Rule3 | User | SG_App | SG_DB | mySQL | Any |
| 4 | Default rule | Default | Any | Any | Any | Any |
Security Profile
You can contain firewall rules as well contain network and guest introspection rule within a security profile such as which Antivirus to use and how to apply
Enable Firewall Services
This process walks through the installation of firewall services on ESG router.
Our default firewall rules allows traffic from everywhere so we are going to configure firewall so we need to disable that first

Change the Default Rule to Deny and Click Publish

Our Webservers will have no traffic at this given point as our services are all denied by the Default rule

Firewalls in the past on NSX was directly enabled on ESG or DLR but the new approach is to use Service Composer and a global Firewall approach to create rules.
For Old method – Navigate to ESG – Firewall Section – Add rule
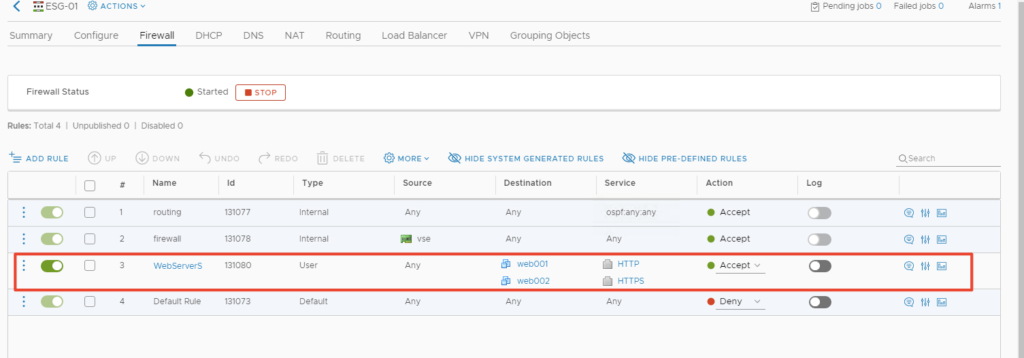
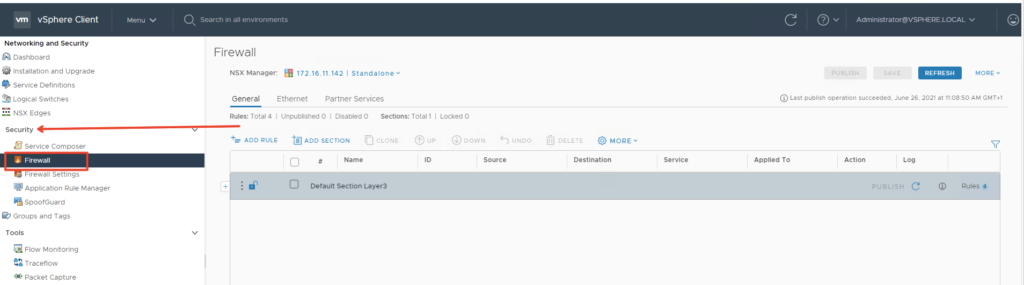
For new method – Go to Security > Firewall as shown below
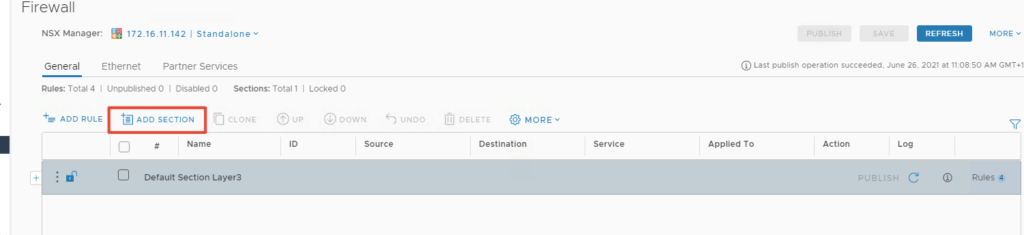
Add Section – This just helps us to group firewall rules under the container
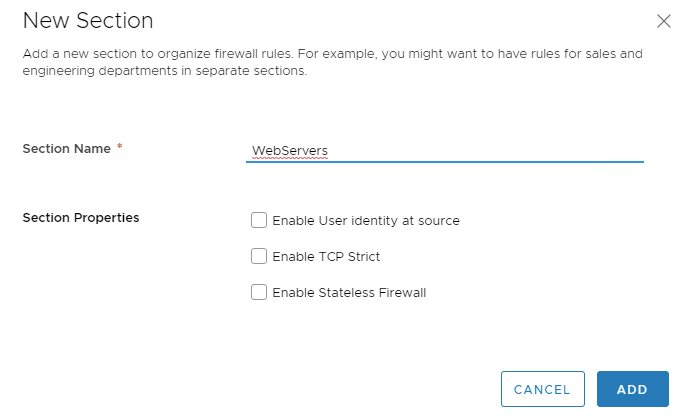
Give the Section a Name
Once created we will have a view similar view as shown


Add rule as Web-App-Rule
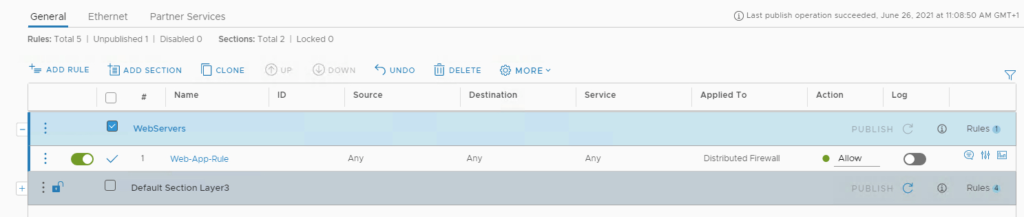
Click on the Destination button and add web01 and web02 and Save
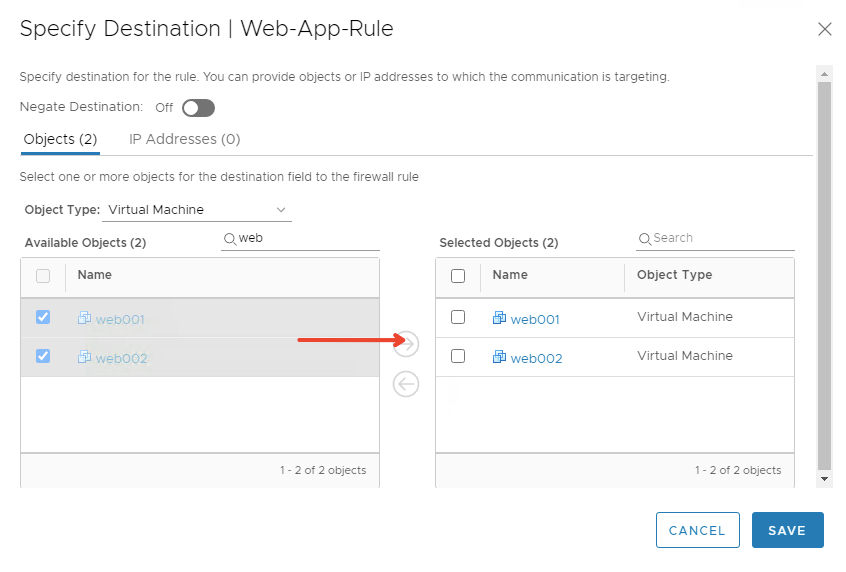
Now Click on Service and choose our Service object as https and http

Drag the service object and click Save
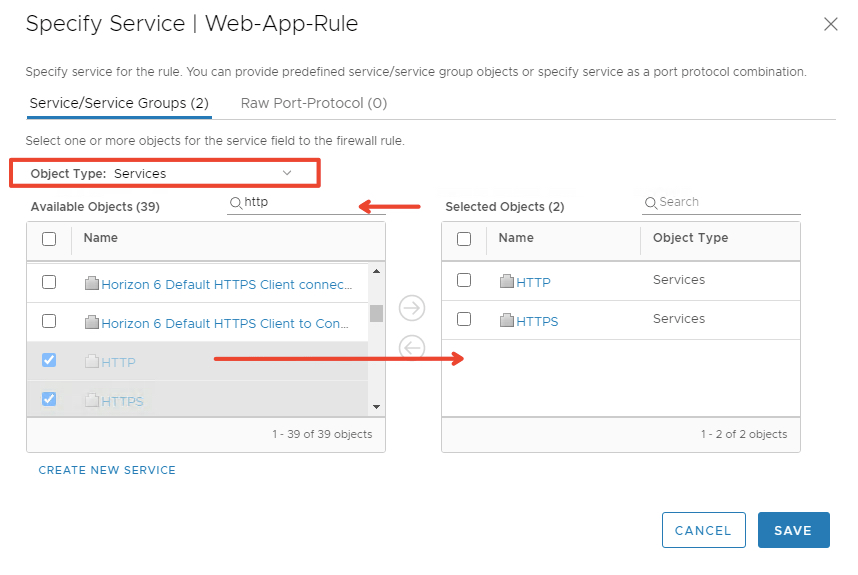
We should now have something similar as shown

As we see our settings are now applied to Distributed Firewall or DLR only and for us to apply to ESG we need to edit the button “Applied to”

Choose the option to apply the rule on all ESG and click Save

Click Publish to apply the change
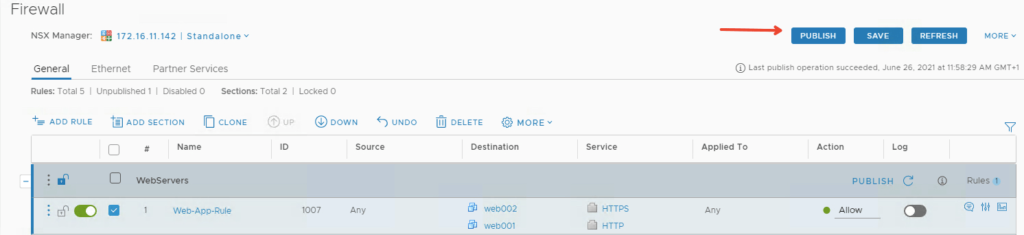
Verify if our web-servers are reachable

All our firewall configs are saved under the firewall settings and should you wish to save or preserve the config you can select the Autosaved config > Edit > Choose Preserve Configs

Conclusion
In this next series, we wil look into enabling firewall rules via service composer.

