Azure networks are isolated networks in the cloud and by default a vNET member cant commute to members in another vNET.
This is the same as AWS VPC Peer.
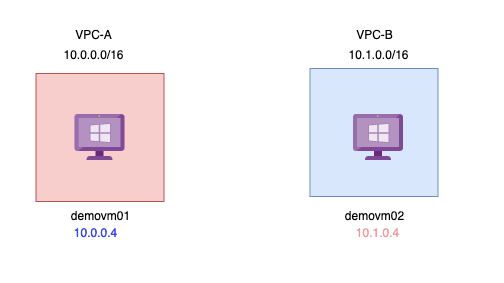
- Azure supports connecting two virtual networks located in the same region or networks located across regions.
- Once you enable virtual network peering between two virtual networks, the virtual machines can then communicate via their private IP addresses across the peering connection.
- You can also peer virtual networks that are located across different subscriptions.
- The virtual networks can’t have overlapping CIDR blocks
1- Create a virtual network as VPC_B
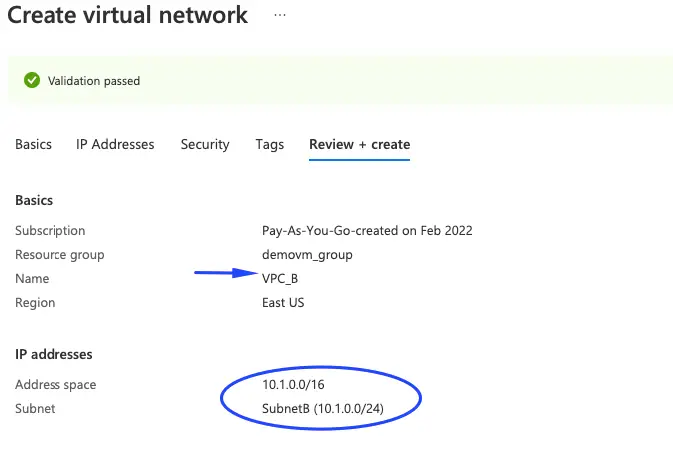
2- Create a second virtual network as VPC_A

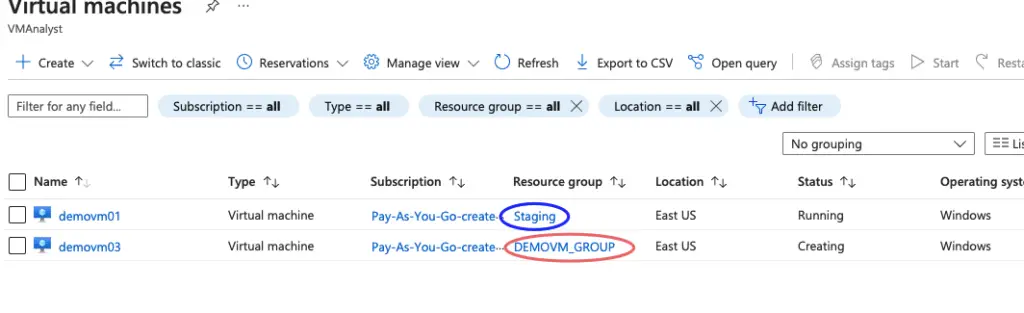
3- Create two VM’s in each vNET
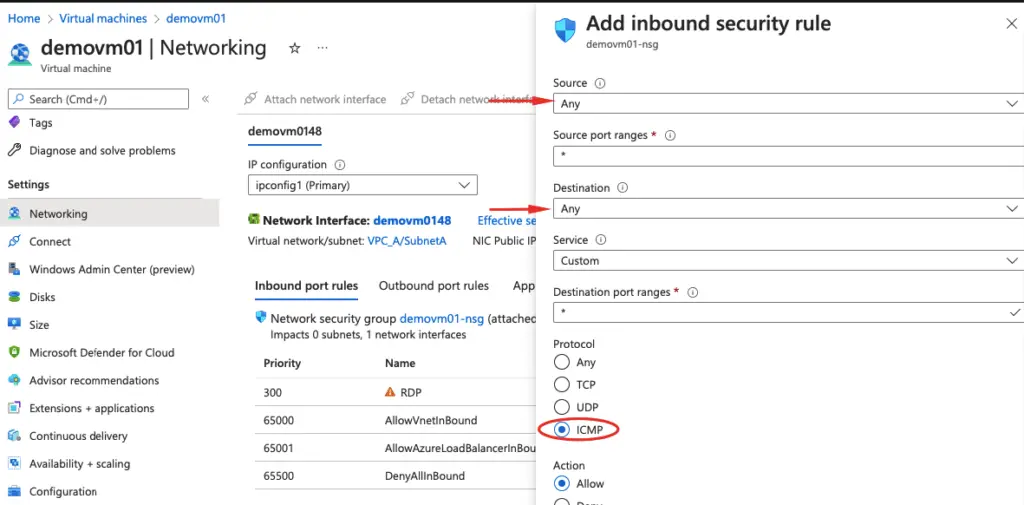
4- Configure Network Security Group (NSG) to allow ICMP traffic
5- Set up the operating system to answer to Ping/ICMP echo request
# For IPv4 netsh advfirewall firewall add rule name="ICMP Allow incoming V4 echo request" protocol="icmpv4:8,any" dir=in action=allow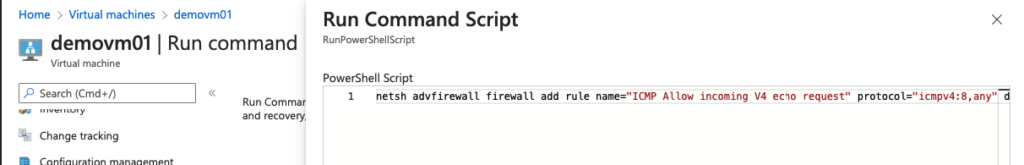
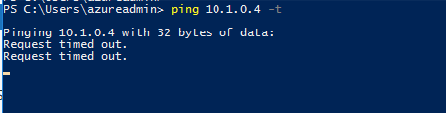
6- We won’t be able to ping our Azure Virtual Machine (VM) on the other vPC now
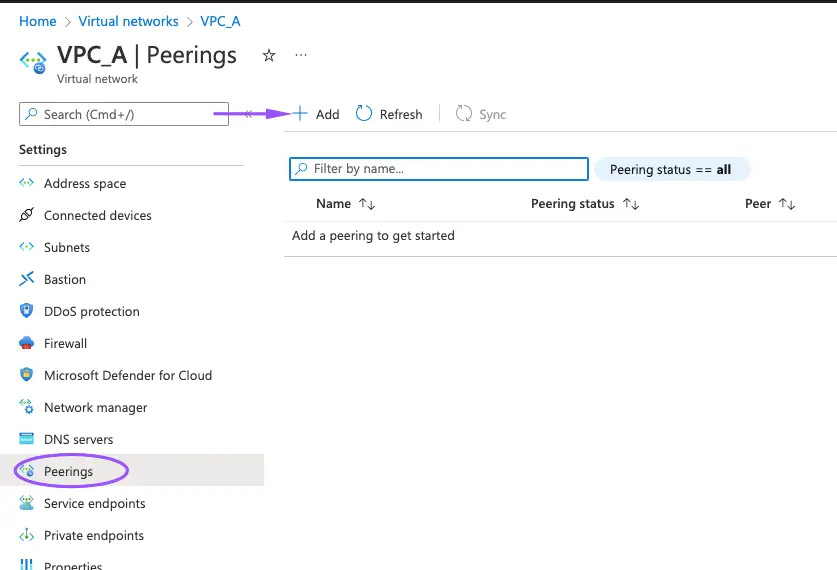
7- Create a vpc peer by going to the peering section of any VPC
8- Give the peering connection a name
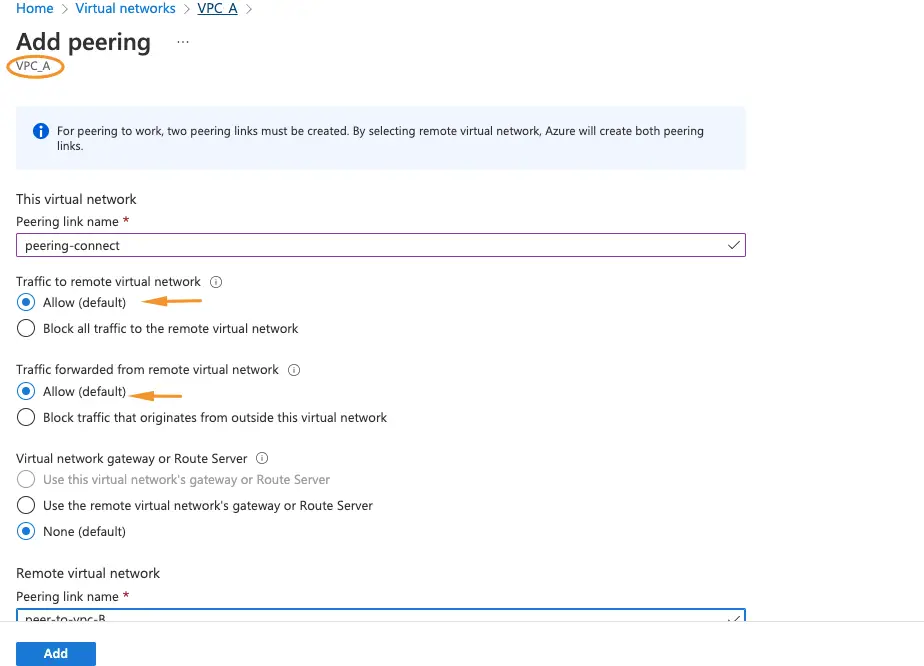
9- Choose the peer vPC to link
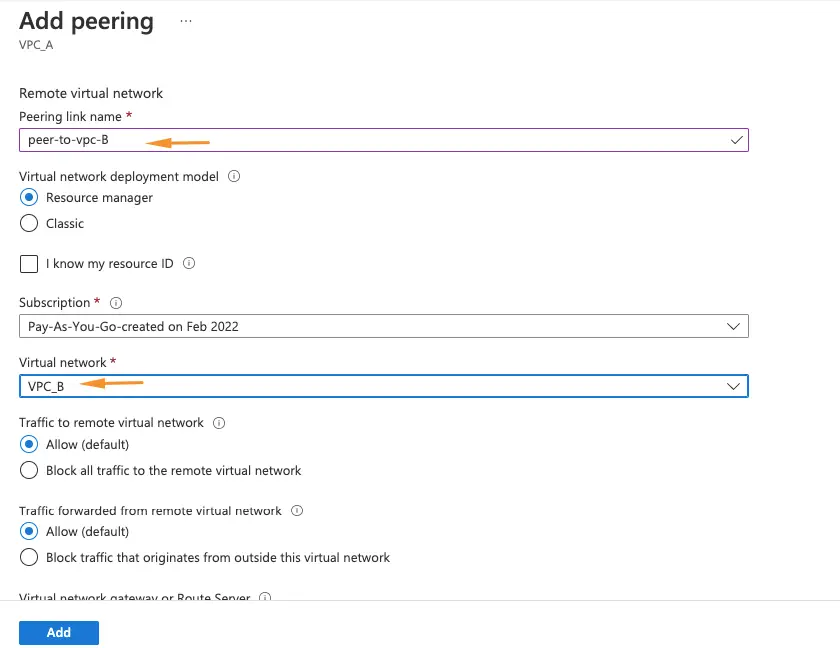
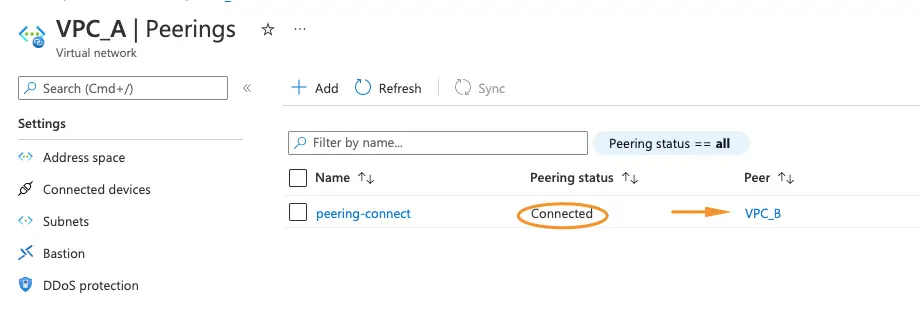
10- Our link between VPC-A and VPC-B is now established
11– login to demovm01 and validate if we are able to ping demovm2
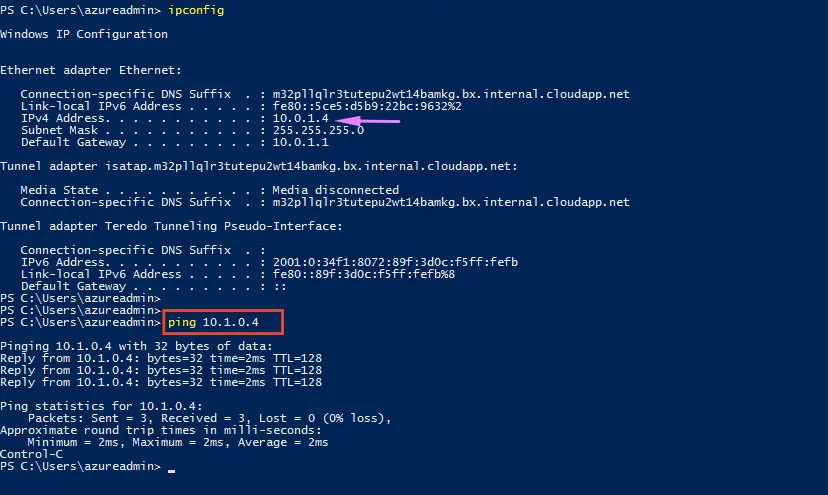
That proves our vNET peering is working as desired.

