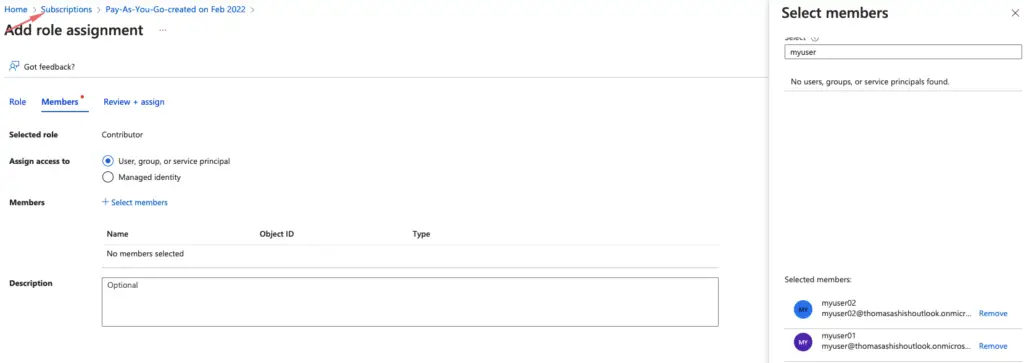
Azure has several built-on roles we can use to configure and manage identities to control and manage access to Azure resources
https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles
The four built-in roles are as below
| Contributor | Grants full access to manage all resources, but does not allow you to assign roles in Azure RBAC, manage assignments in Azure Blueprints, or share image galleries. |
| Owner ( Admin ) | Grants full access to manage all resources, including the ability to assign roles in Azure RBAC. |
| Reader | Read-only Account |
| User Access Administrator | Ability to manage user access to Azure resources. eg : grant permissions for another user |
Assigning roles to Subscriptions and Resources in Azure.
Permissions can be applied at the subscription level, resource level or individual resource level. Role-based permissions can be granted at different levels as shown.
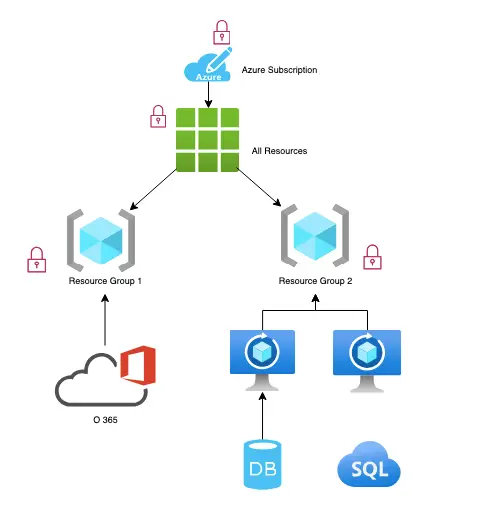
Role-based assignments – Reader Role
The below write-up grants a user reader-only IAM role to a virtual machine
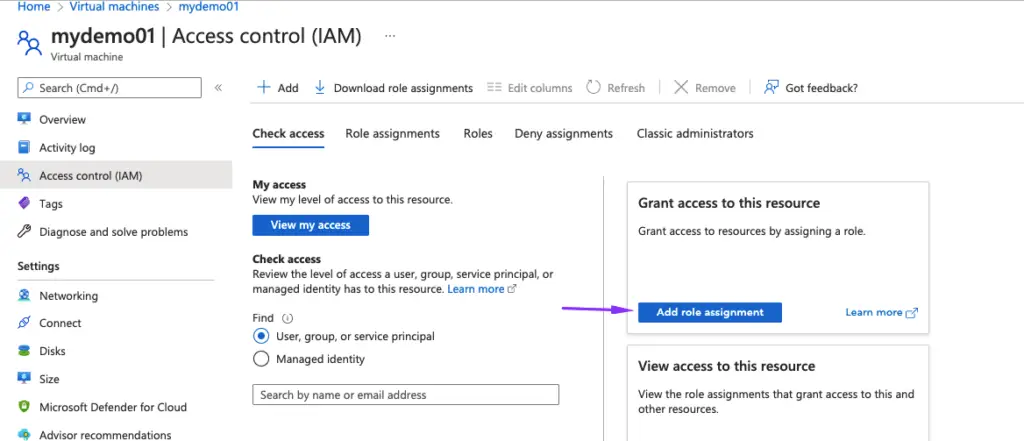
Choose the Role Group Reader
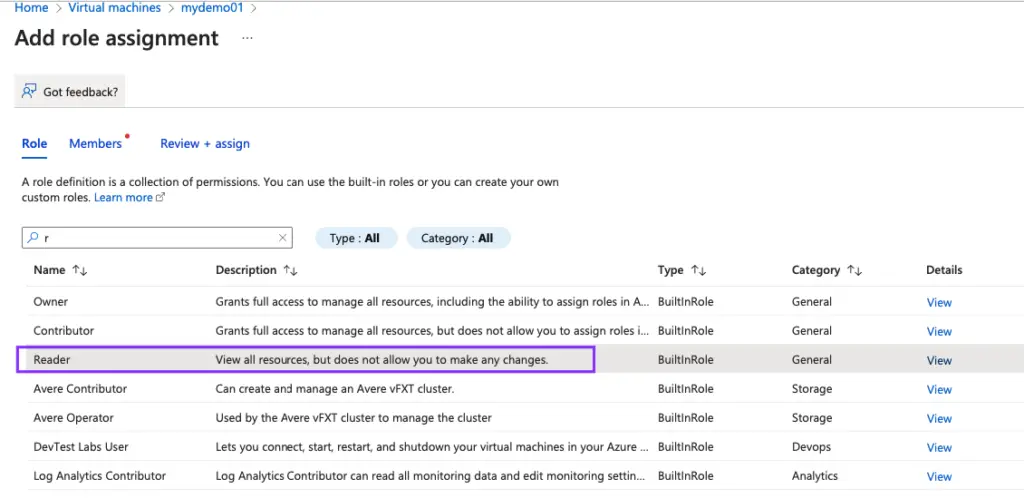
Assign the user
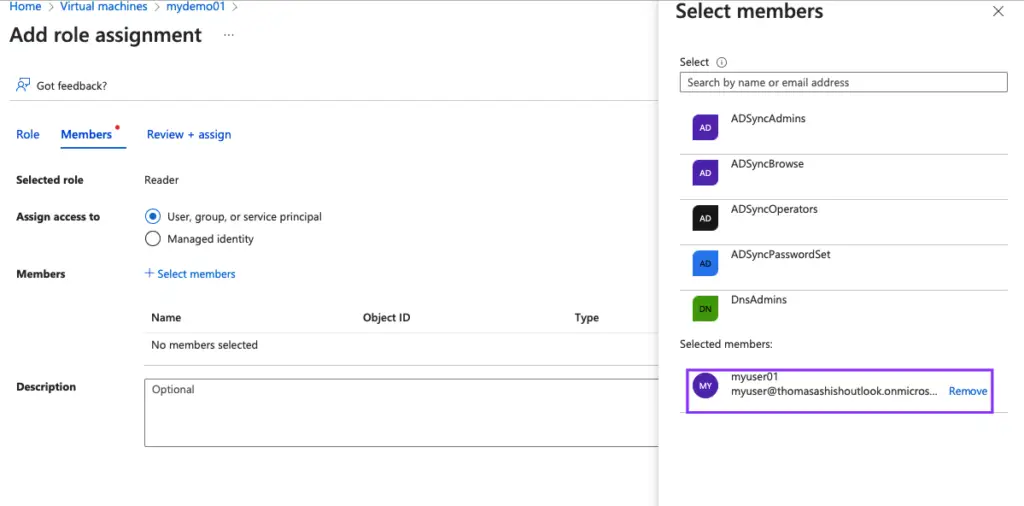
The below user has been granted reader-only permissions onto the Virtual machine.
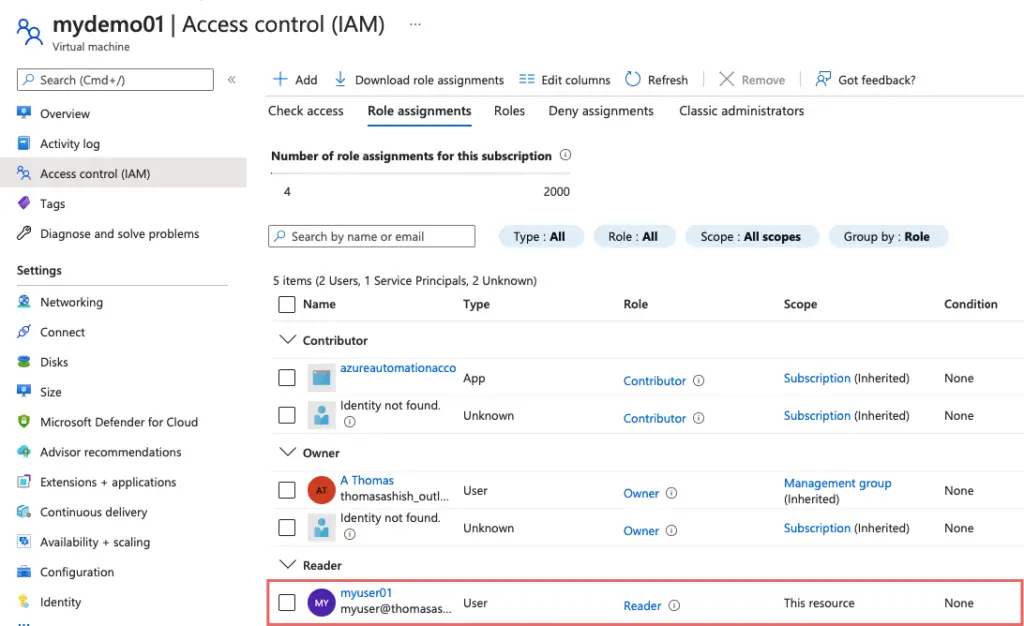
As permissions are applied just to the virtual machine which is a resource, we are not able to see the IP address on it. For us to see that info, we will need to assign permissions at the individual resource level such as networking, disk etc.
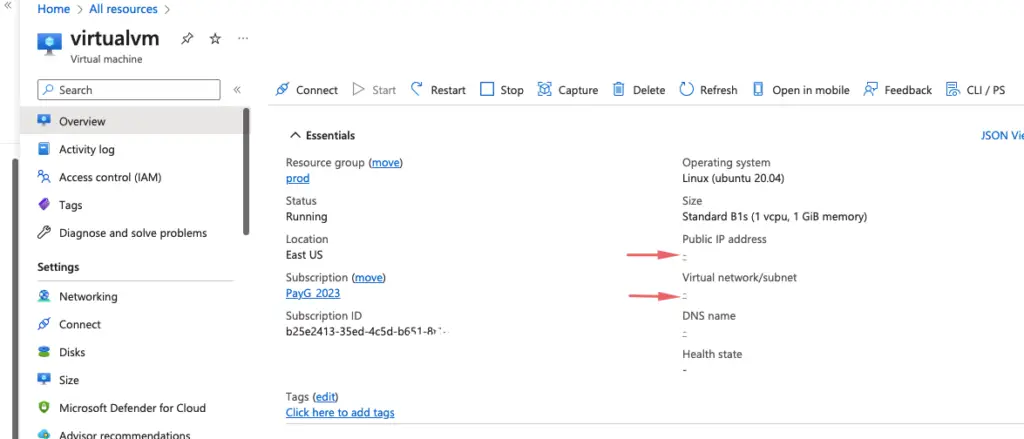
Role-based assignments – Resource group level
Access can be granted to a user at the resource group level.
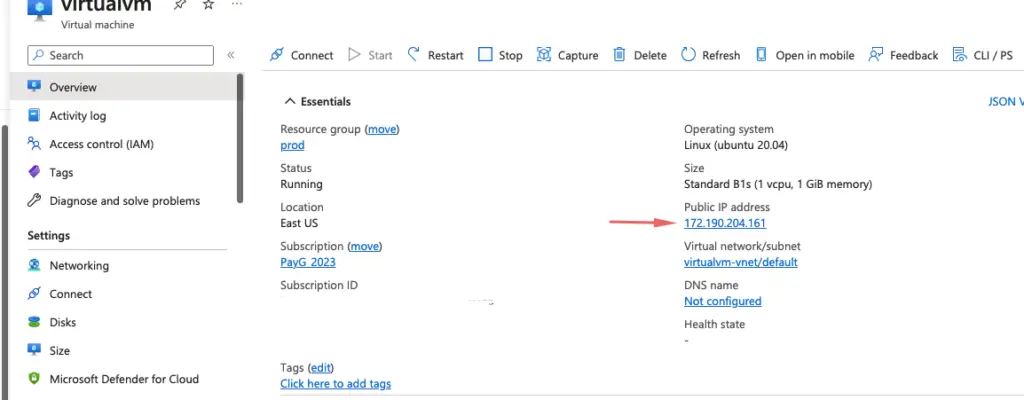
As permissions are applied to the resource group, we are now able to see the IP address of the VM.
Role-based assignments – Subscription level
Access can be granted to a user at the subscription group level too. When we do this, the user will get access to all resources under the subscription account.