In this section, we will go through the configuration of the ISCSI target server on a RHEL host. ISCSI is an Internet Protocol that allows multiple servers and users to access network drives remotely over a TCP/IP network by setting up a shared storage network.
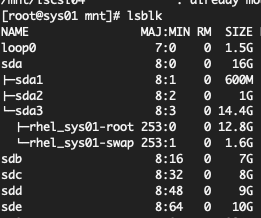
As part of this assignment, I’ve connected 4 disks (/dev/sdb-sde) to my ISCSI target server as shown and we will attach these disks to our servers sys01 and sys02 which will form a Veritas Storage Foundation cluster in subsequent chapters.
Installing iSCSI Target
Open the terminal and use the yum command to search for the package name “targetcli” to add, monitor, and remove iSCSI storage interconnects.
Install the targetcli tool
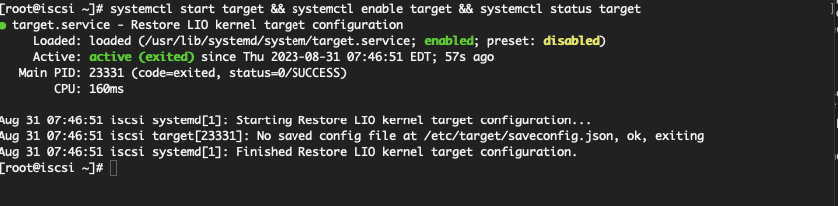
Start and enable the target service on boot time.
Open port 3260 in the firewall and reload the firewall configuration

View the targetcli layout using the below command

List using the following command

Workflow for creating an iSCSI target
To configure an iSCSI target, we will need the following details
- iSCSI target with a unique iQN.
- iSCSI Backstore – is a storage object that defines the resources that the backstore uses.
- Create iSCSI Portal.
- Set up iSCSI LUN.
- Creating an iSCSI ACL
- Setup CHAP Authentication if required/
Navigate to the iSCSI directory and run the create command to create an IQN
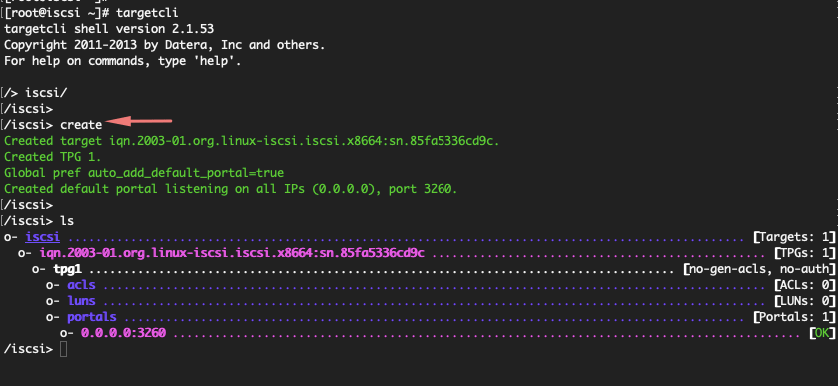
Create a block storage object
Block devices include physical devices like HDDs etc from where we can create LVM or RAID volumes. Navigate to the block of the backstores directory

Create an iSCSI LUN of each of our block devices attached

Creating an iSCSI portal
By default, the iSCSI portal is set to listen to all IP addresses with the default port number which is: 0.0.0.0:3260. Navigate to /tpg1/portals to delete the default portal
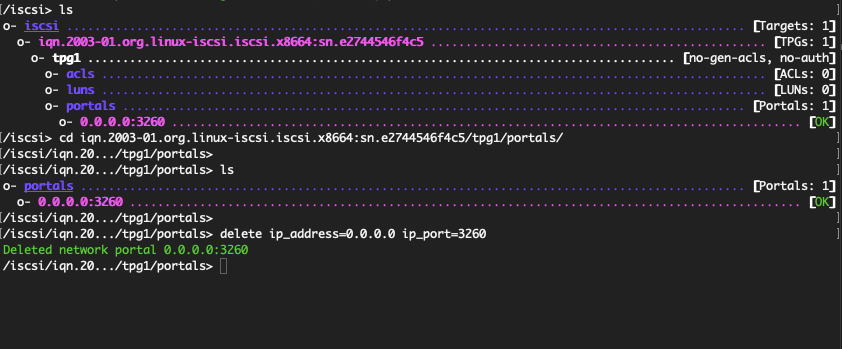
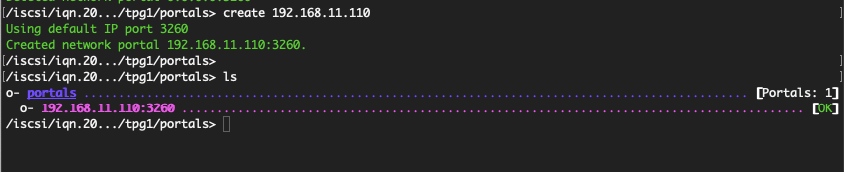
Then create the new portal and specify the IP address to enable the target.
Configure iSCSI Initiator on RHEL 9
ISCSI Initiator is installed on the client machine to send data to the target. The below package is required to install the ISCSI initiator.
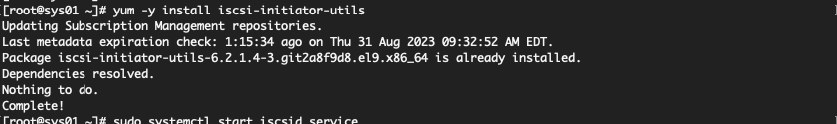
Start and enable the target service on boot time. We will need this info to be added to our ISCSI target server.

Access Control Lists are used to configure access rules that each initiator has access to LUNs. Navigate to our iSCSI target and then to the ACL directory and create an ACL using the initiator name we found in /etc/iscsi/initiatorname.iscsi

Discover the target by using the target’s IP address using the below command we should get a response from our target ISCSI and we can see all our devices attached.
[root@lnx01 ~]# iscsiadm -m discovery -t st -p 192.168.0.17
192.168.0.17:3260,1 iqn.2003-01.org.linux-iscsi.satellite.x8664:sn.02e62e692903Log in to the ISCSI target
Show disks attached
sudo grep "Attached SCSI" /var/log/messages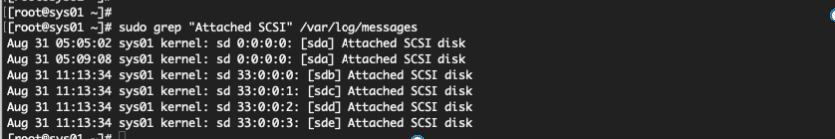
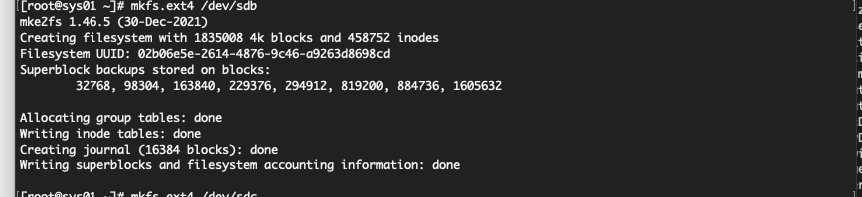
Create a filesystem on our disks attached.
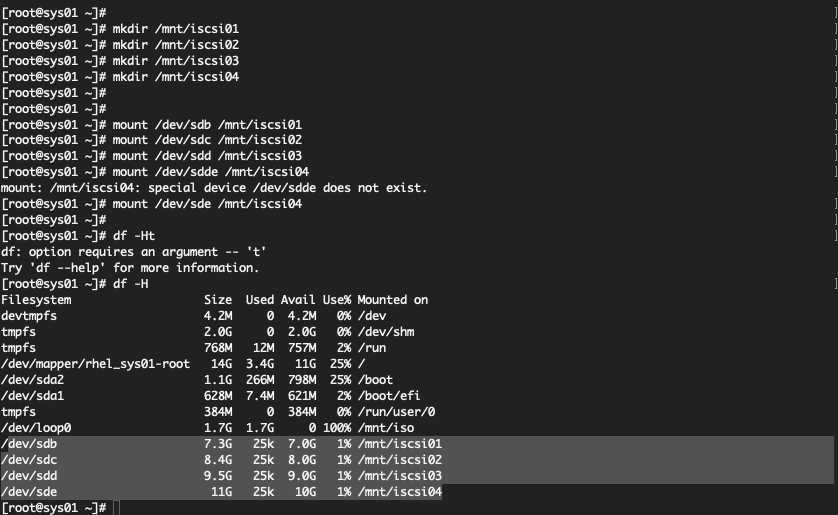
Mount the file system
To make the file persistent on boot add an entry to fstab file

Verify the disk has been mounted.

That’s about it to configure a simple ISCSI target server for our lab.

