In this blog, we will explore the identity management section of Azure AD.
Licensing
| The minimum required for password resets | Minimum required for password resets |
| Azure AD Premium P2 | Azure P1 + Security Features |
Subscriptions
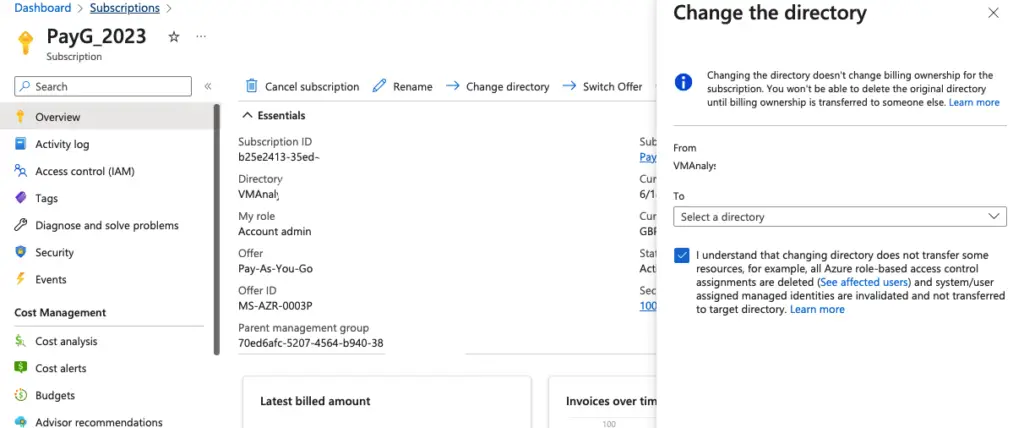
- There is a trust relationship between Azure AD and the subscription.
- Each subscription can only trust a single Azure AD directory.
- Multiple subscriptions can trust the same Azure AD directory.
Create Dynamic AD Groups
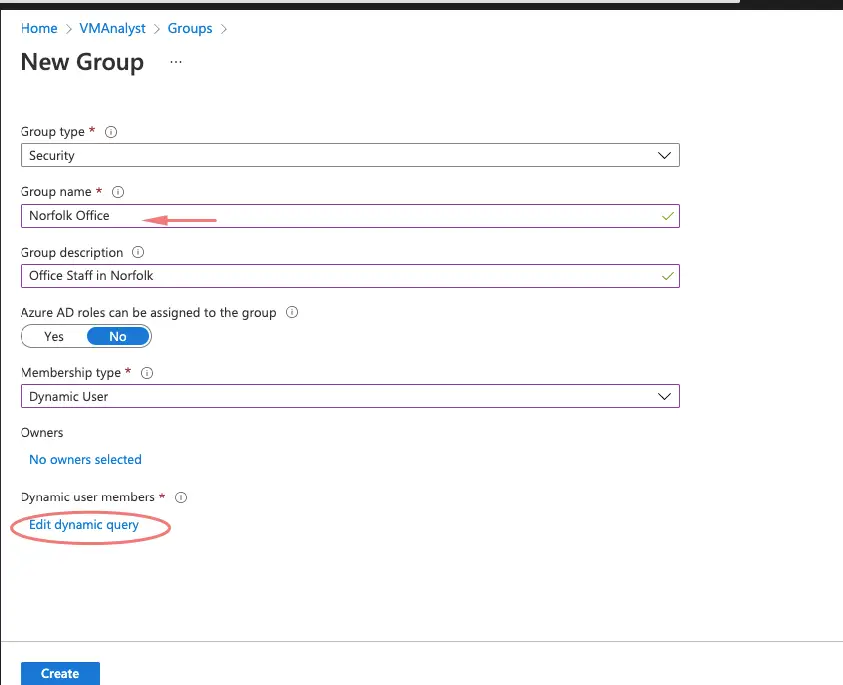
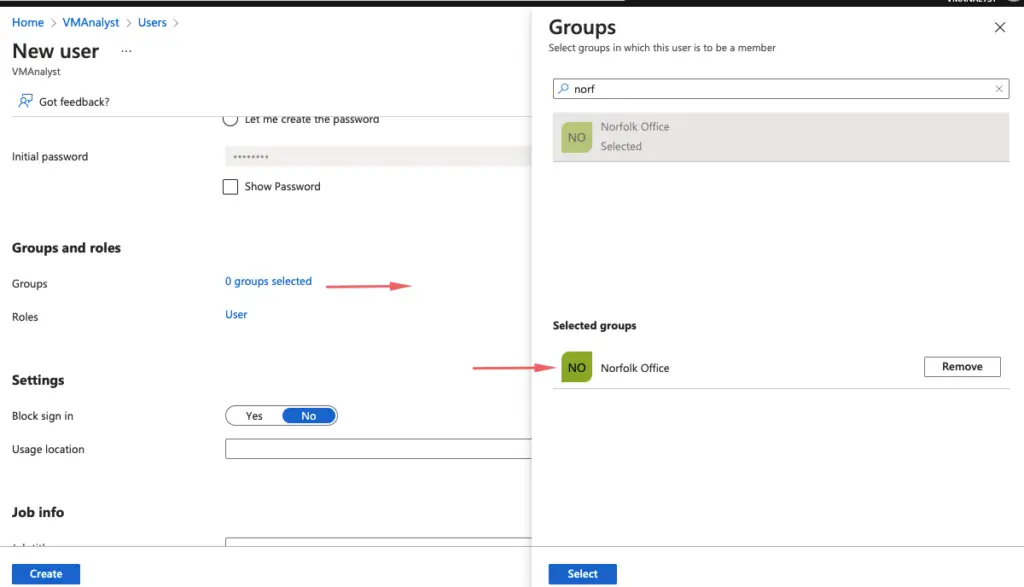
Let’s begin by creating a group in Azure for our Norfolk Office based on a condition or property eg: City.
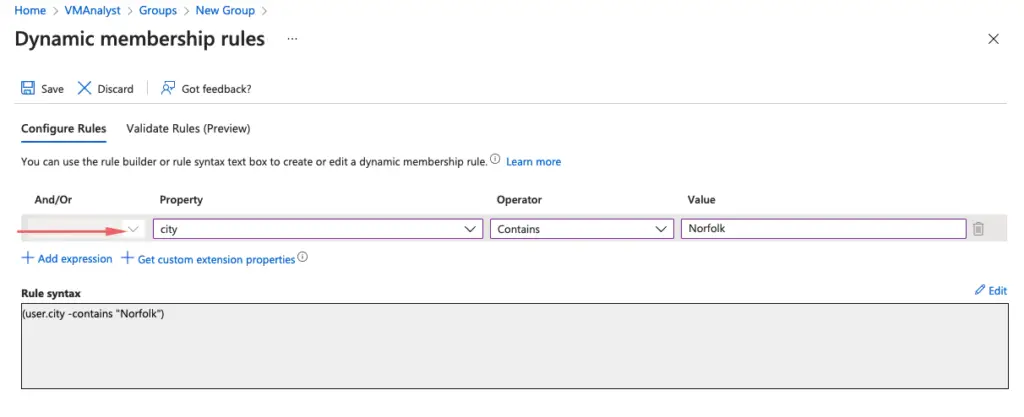
We will choose Dynamic Group as we will want to group users later based on the office location they work
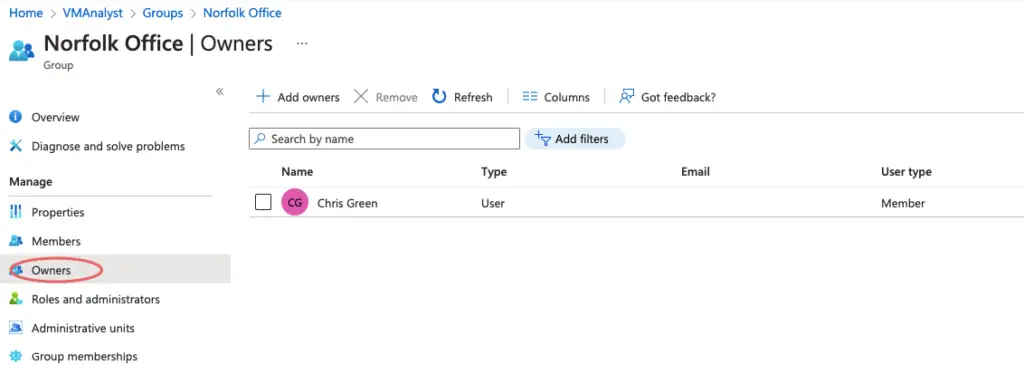
Every group should have a group owner so we’ve added one here.
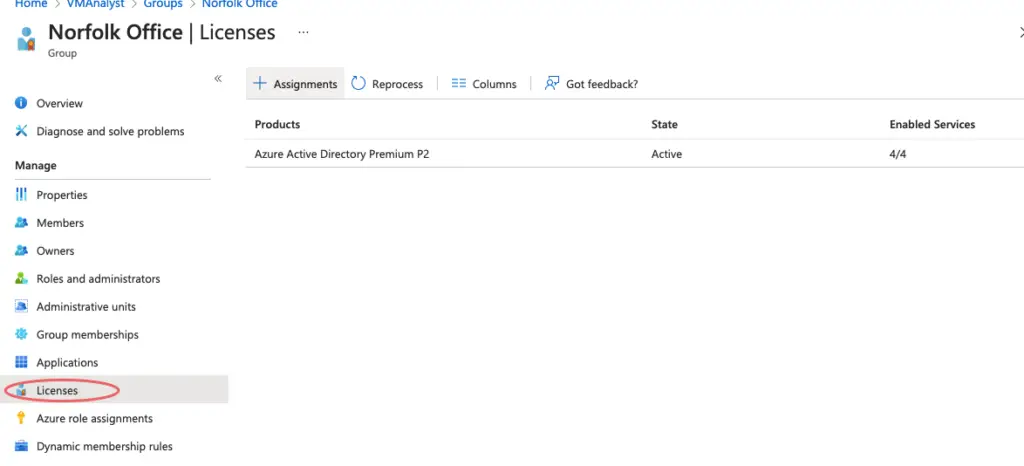
Assigning Licenses to Groups
Rather than assigning licenses at an individual user level, it’s much faster to do the assignment at the group level and this happens under the licenses tab at the Group level
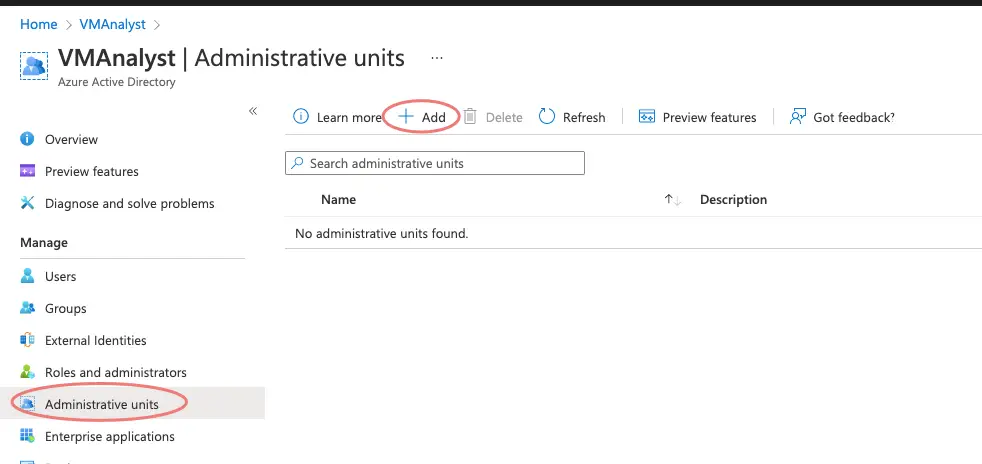
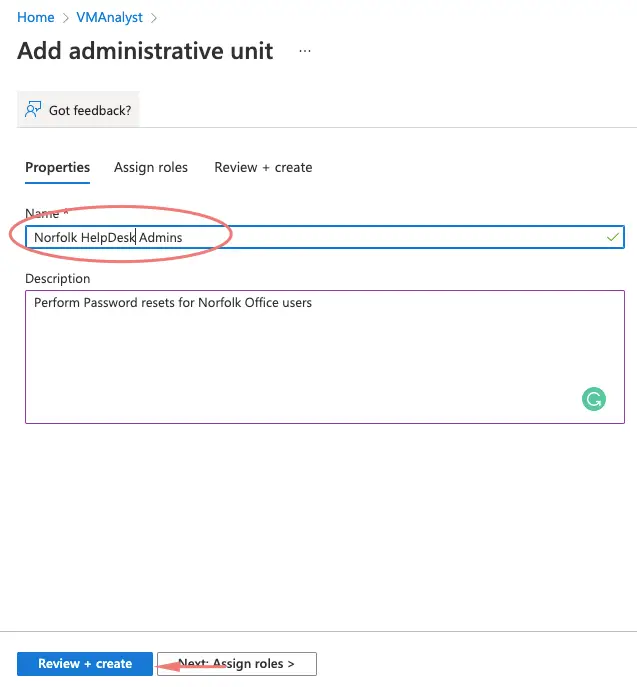
Creating Administrative Units
AU in short will give a few users some privileged access in our Norfolk office so they can reset passwords, assign licenses etc.
Click on the Helpdesk Administrator or User Administrator
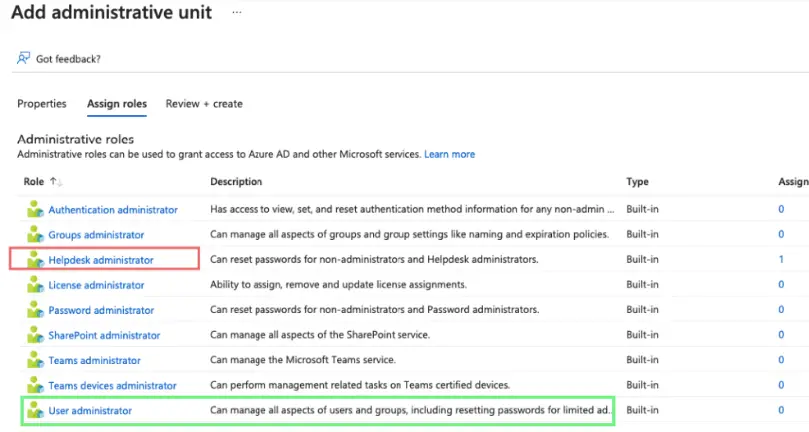
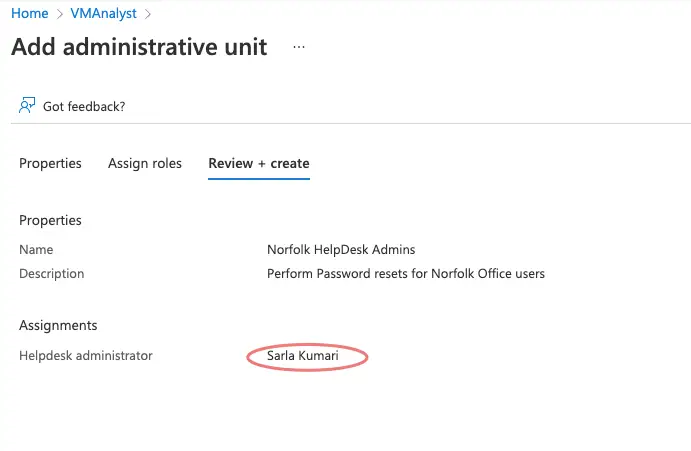
Add Sarla as our Helpdesk admin for Norfolk Site
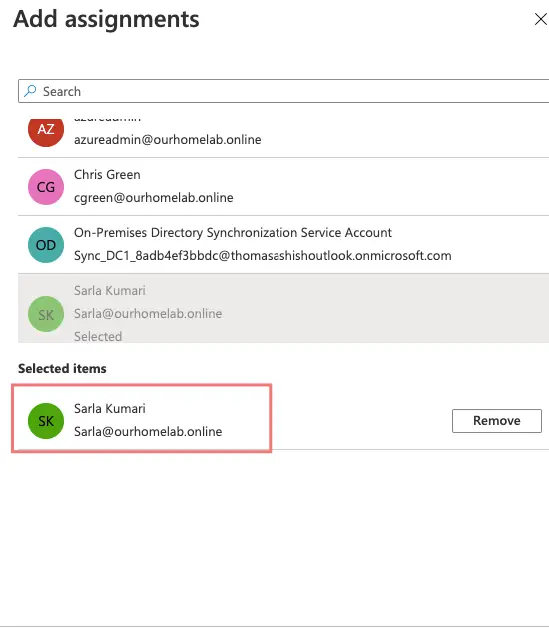
Click Review and Create
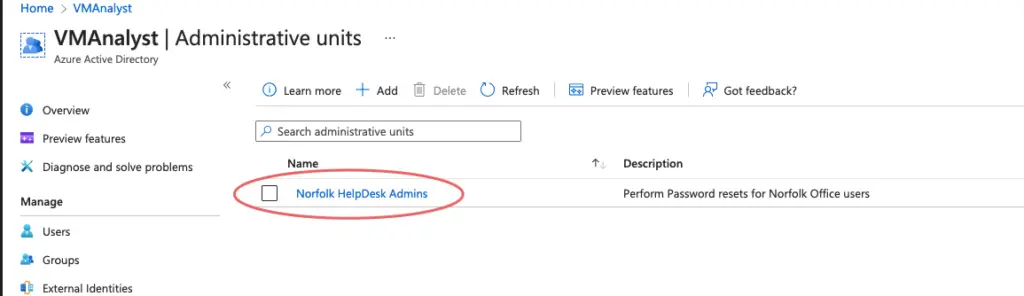
Our Administrative Unit Norfolk HelpDesk Admins is now ready.
Creating Users
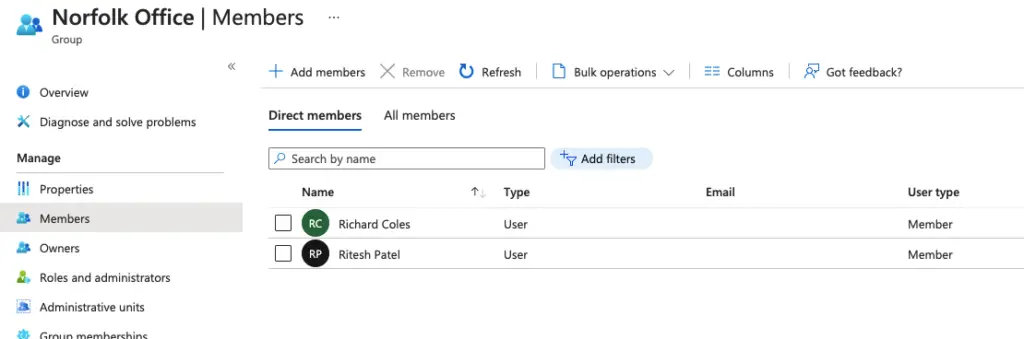
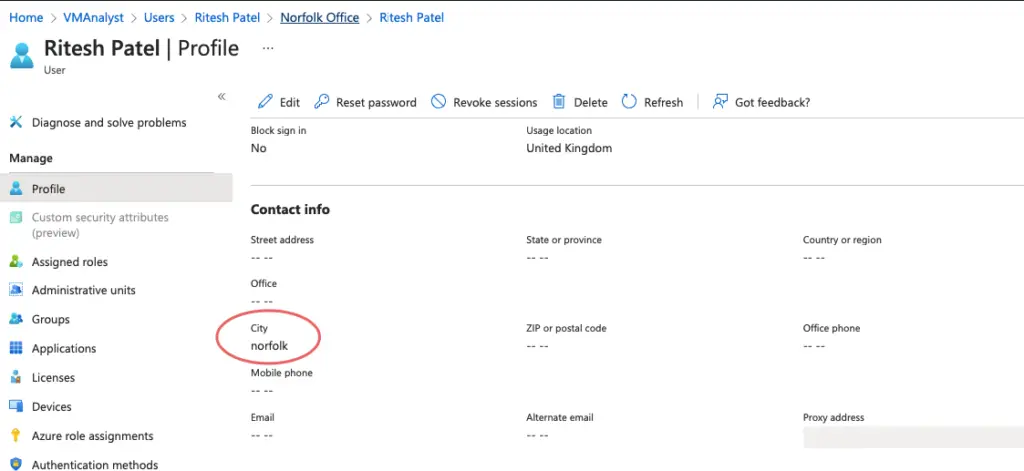
Since we choose to add users dynamically via their office location, our users will be automatically added to the group when the office location is set to Norfolk. Users get the name plus the default domain name as their email account.
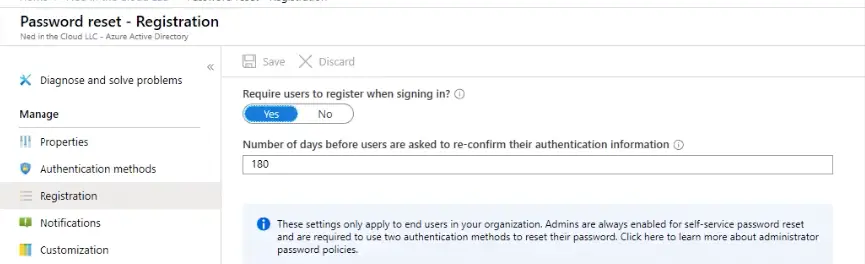
Password Reset Registration
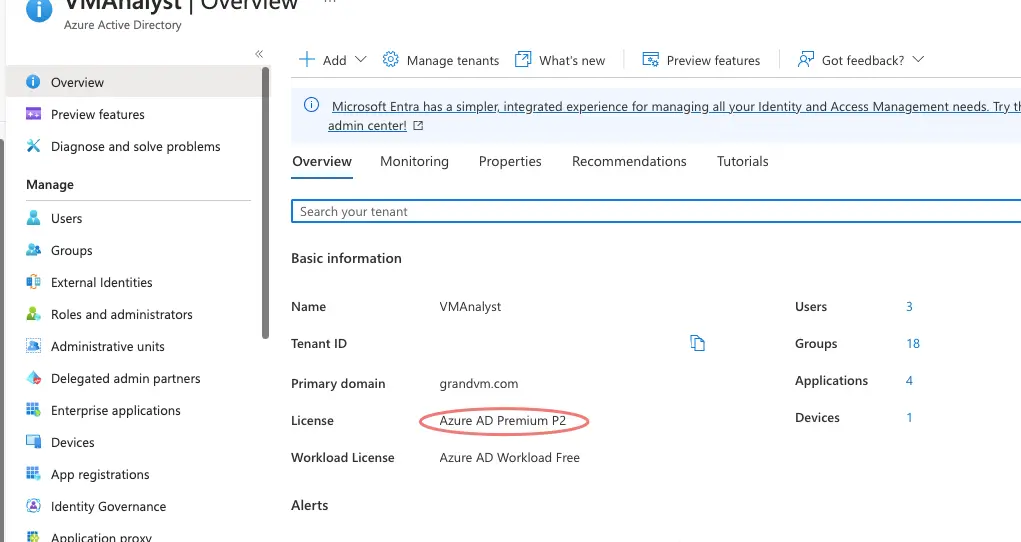
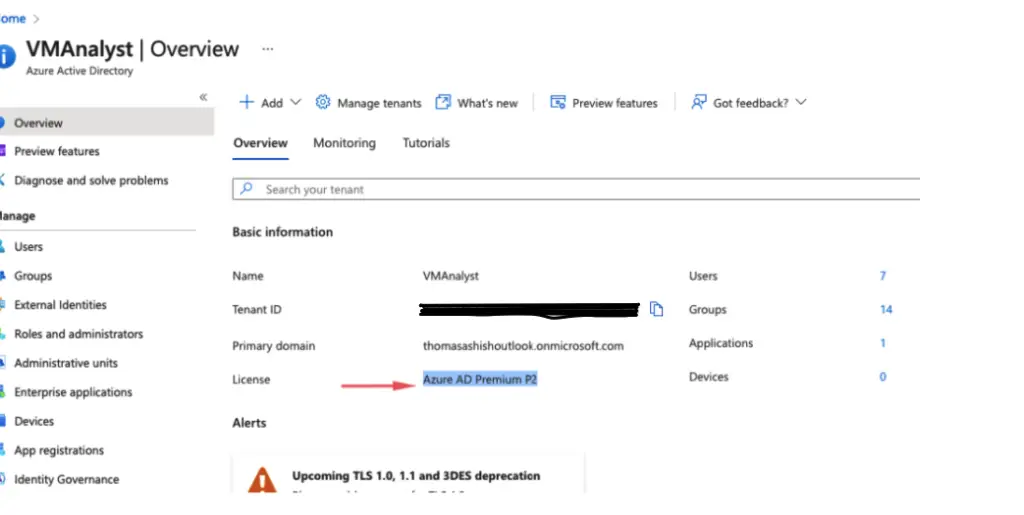
In order for us to do password reset registration, we need to have at least an Azure AD Premium P1 or Azure AD Premium P2 license.
Self-service password resets can be done via the below tab
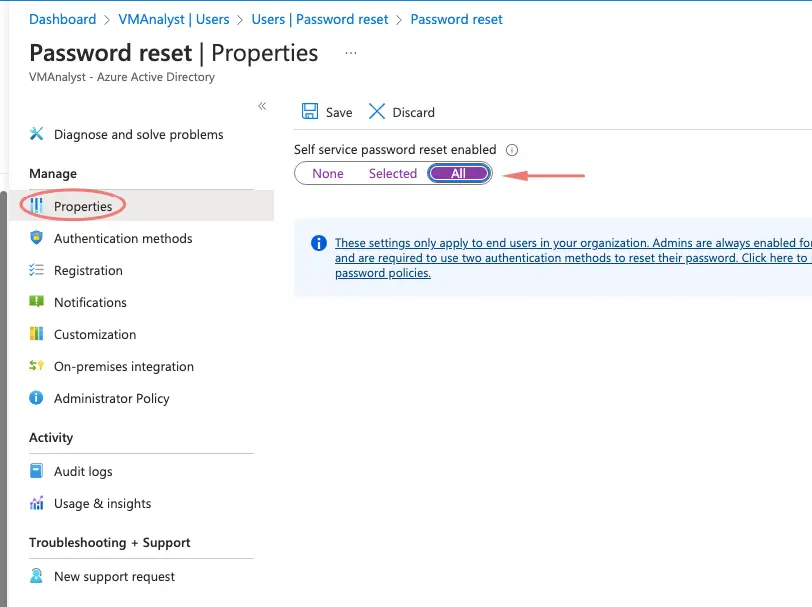
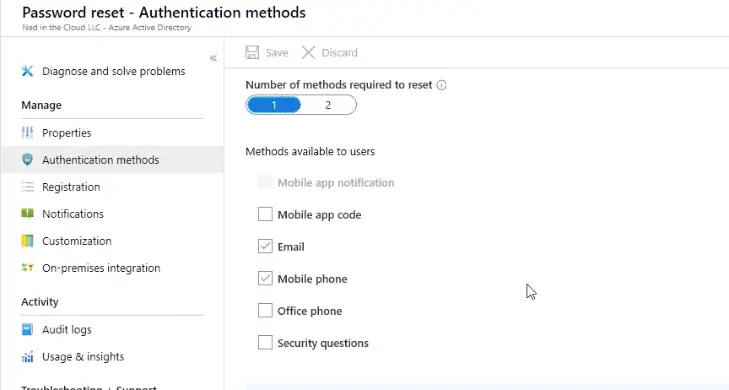
We will add email/phone authentication
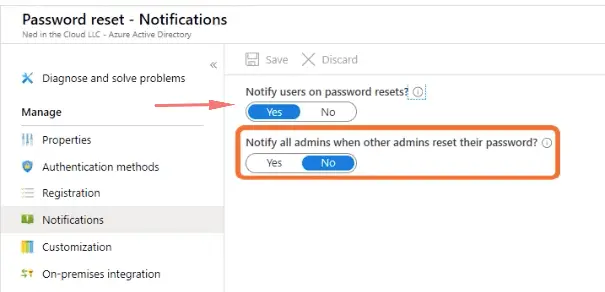
Notify users about events on password resets
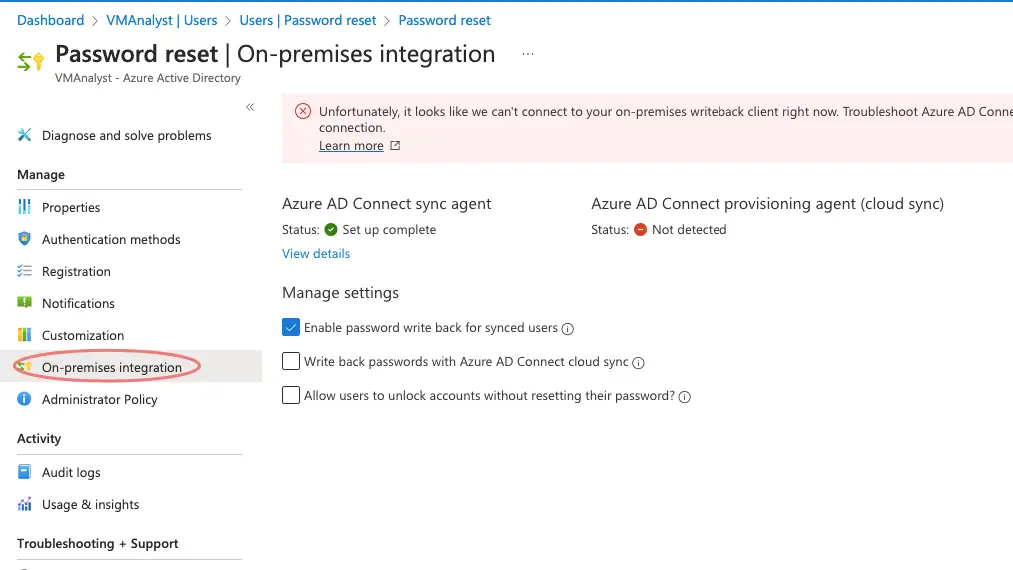
Synchronization with on-prem AD is available under the integration tab
Setting up Users and Applications for Hybrid Identity
In this section, we will get some apps from Azure Marketplace and provision them to our users.
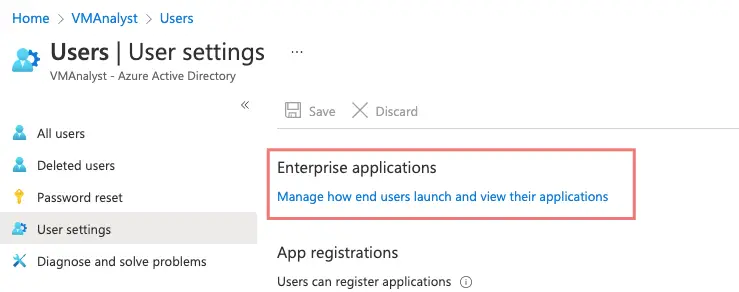
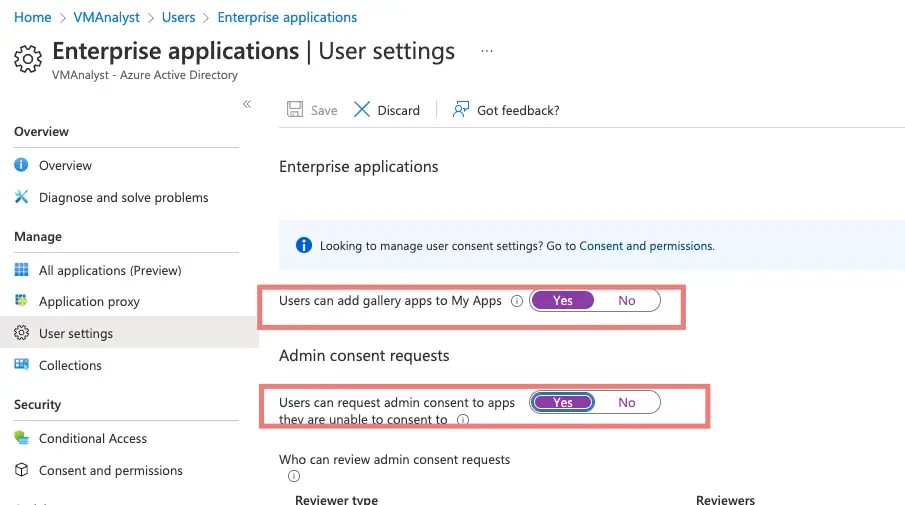
Go to the Enterprise Application section
Enable Users can add gallery apps
Test User Access
Login as the new user we created using one of the links
https://myapplications.microsoft.com/
https://account.activedirectory.windowsazure.com/
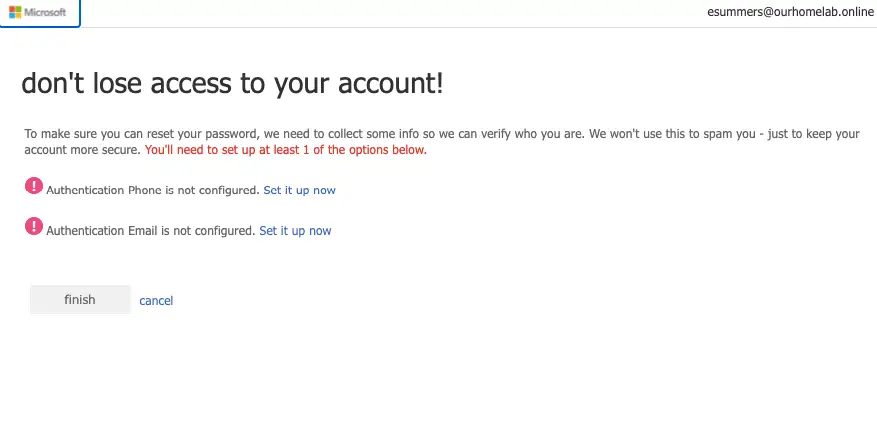
We’ve secured our access using phone/email
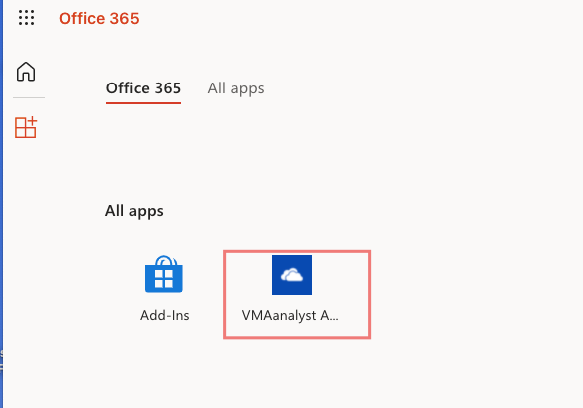
Once logged in, I should be able to see the apps I provisioned to the user.
Managing Devices in Azure Hybrid Identity
In this section, we will add a new Virtual machine and join Azure AD. If this option is chosen, this VM will be auto-joined to Azure Ad
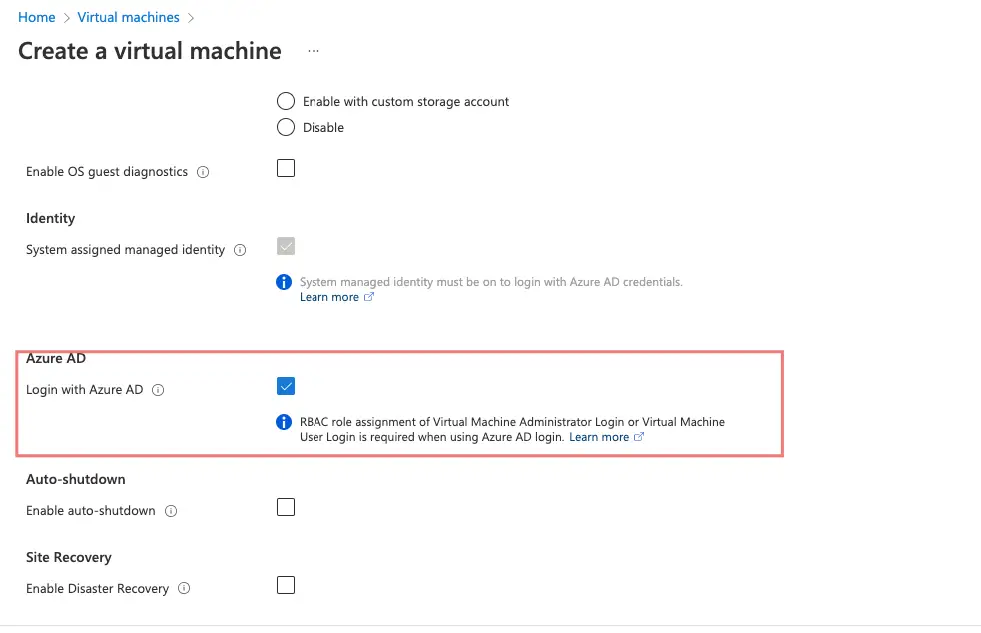
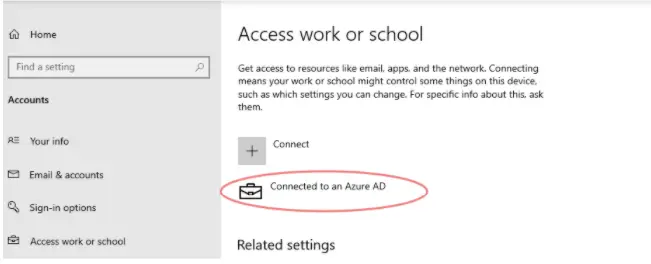
Alternatively, on our Windows 10 PC, let’s just connect to Azure AD manually as shown
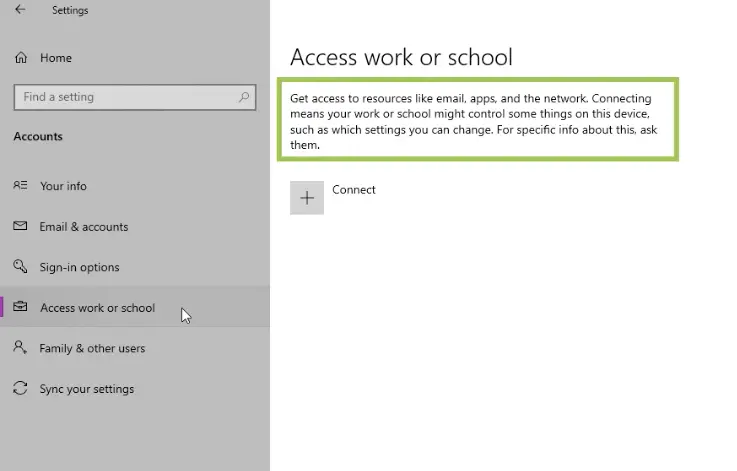
Give the Azure AD account
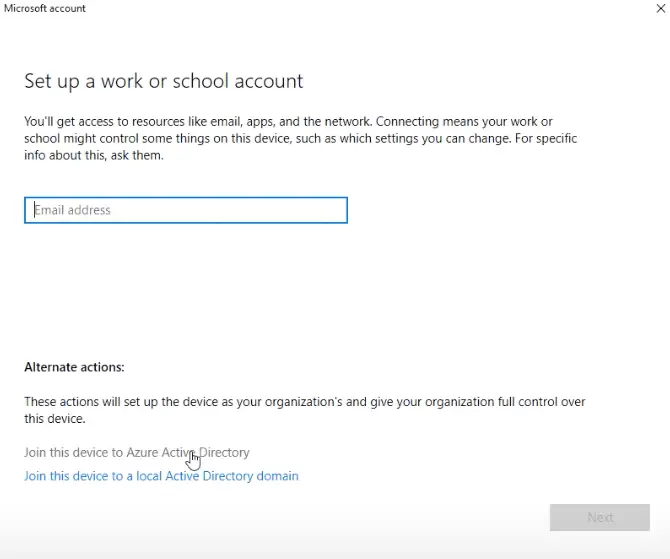
Join Phone
Configure MFA
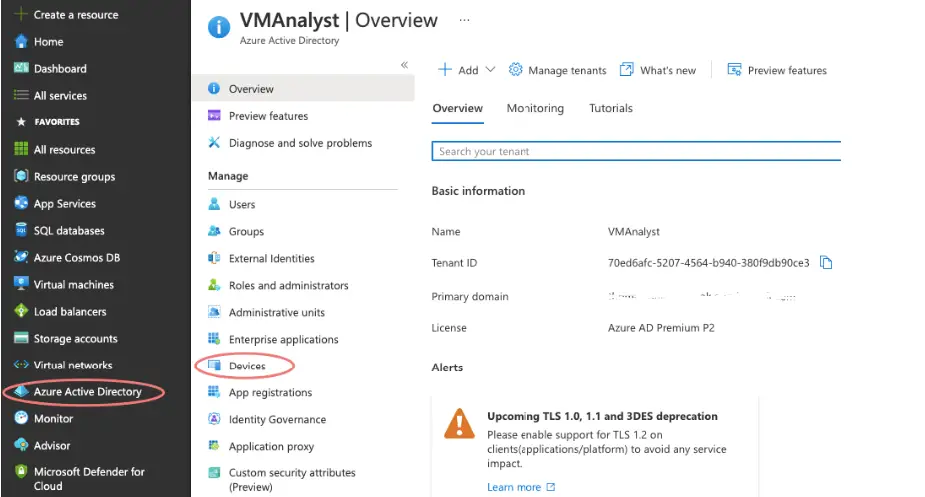
To view devices, joined to Azure AD go to the below tab
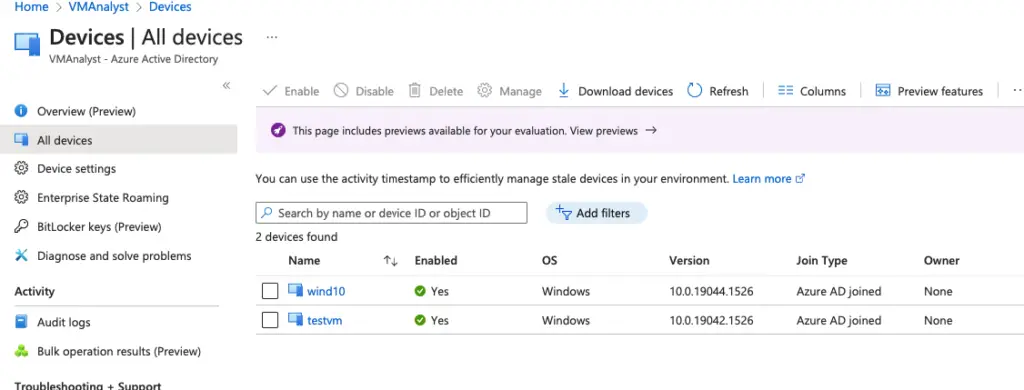
All our Azure AD joined devices appear here.
Configure MFA
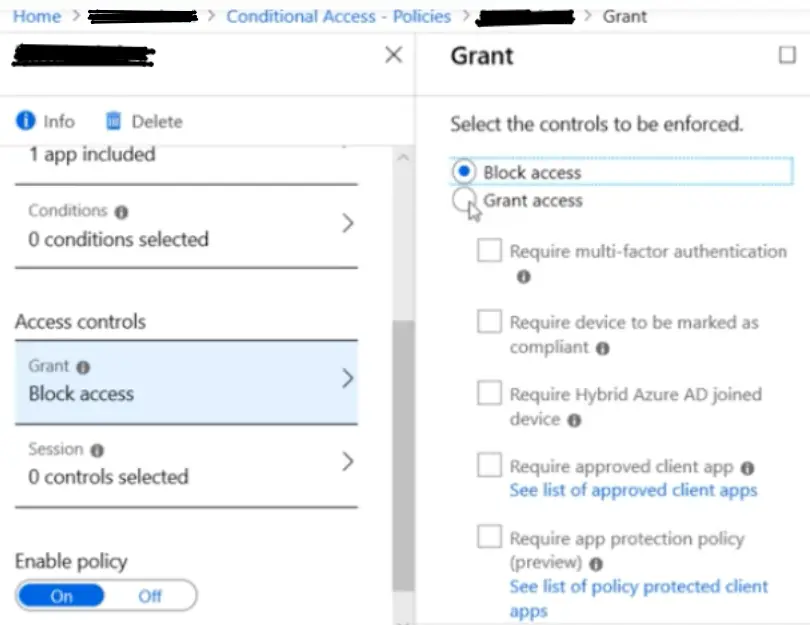
Per user, MFA is free of charge but conditional access needs P1/P2 license.

