This blog covers the overview of Multi-Factor Authentication, Azure AD MFA setup that acts as an additional authentication method for successful authentication of your Azure Account.
Azure AD MFA is a cloud-based identity and access management (IAM) and part of the Azure AD premium offering that provides capabilities such as conditional access policies and integration with third-party authentication providers.
Before we start, check that you have Azure AD Premium plan 1 or 2. AD Premium is needed for conditional access but for per-user MFA the free AD version will work just fine.
Enable MFA for Admins Per User level
AD Premium is not needed needed for per-user MFA, the free AD version will work just fine. Under Azure Portal go to Active Directory > Users > Click on Per-user Multi-Factor Authentication
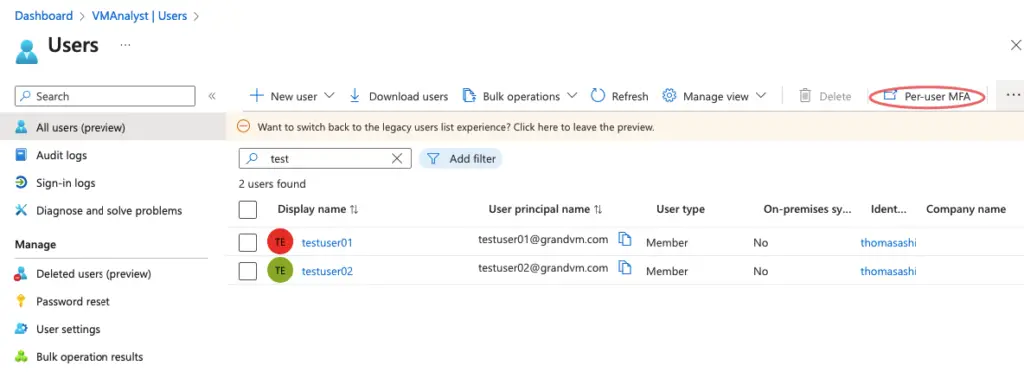
When you click on MFA, it will show you the option to select the user and Enable MFA.
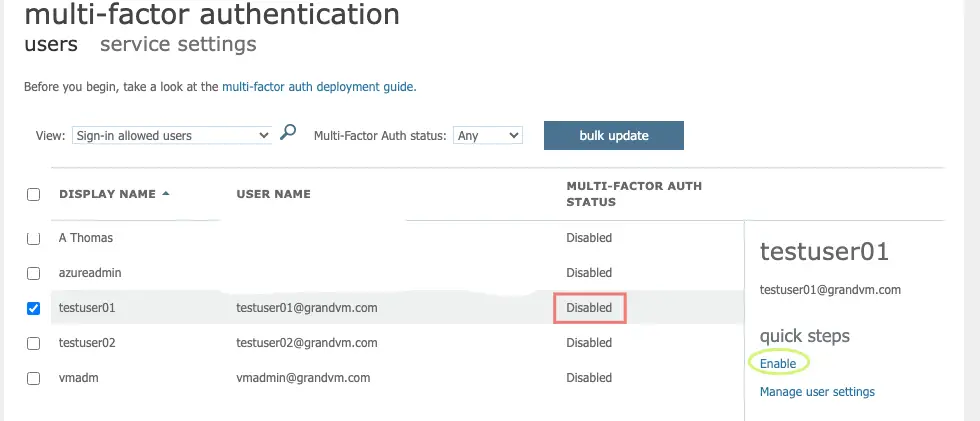
Click on Enable Multifactor Authentication.
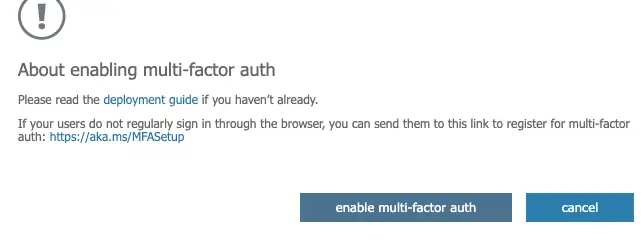
Multi-Factor Auth has been successfully enabled.
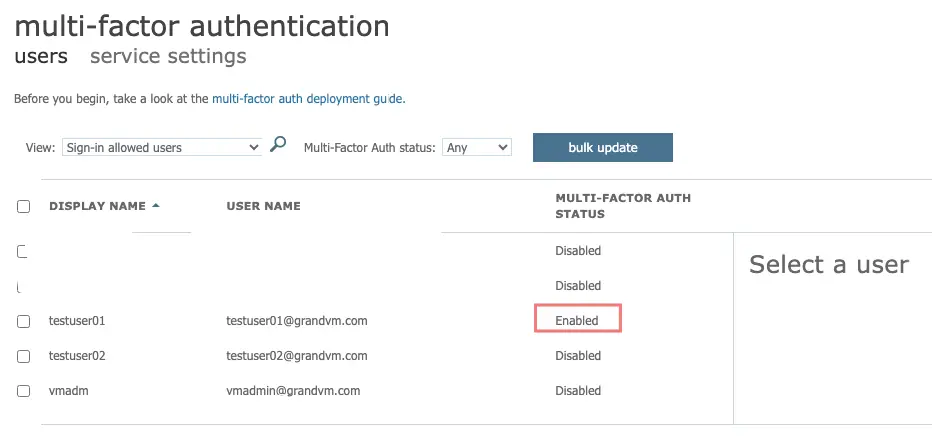
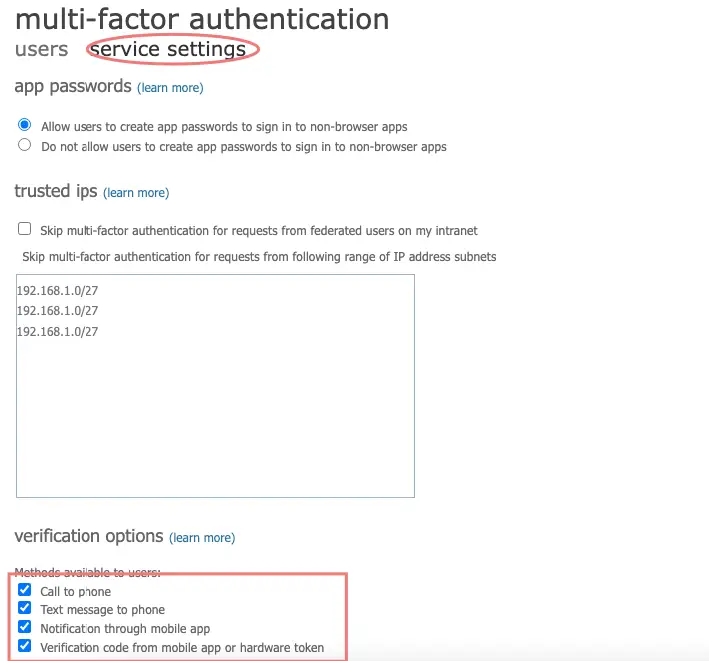
There are multiple ways Azure MFA can verify a user’s identity which is set under Service Settings
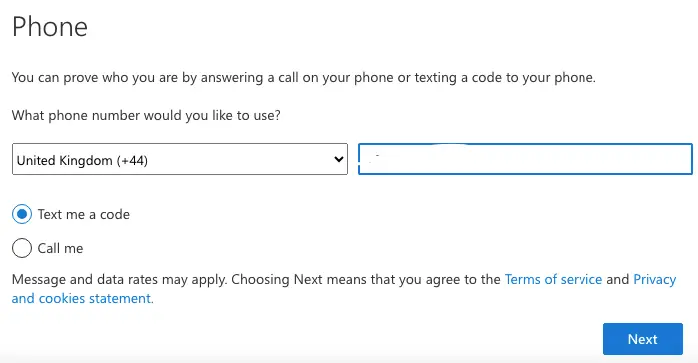
- Phone call
- Text Message
- Microsoft Azure Authenticator App
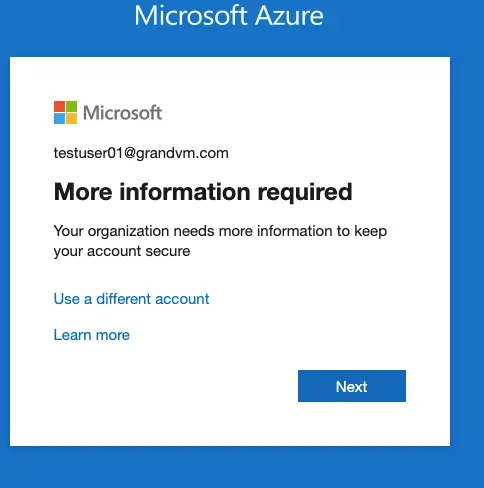
Log in to your Azure Account and click on next to Sign in.
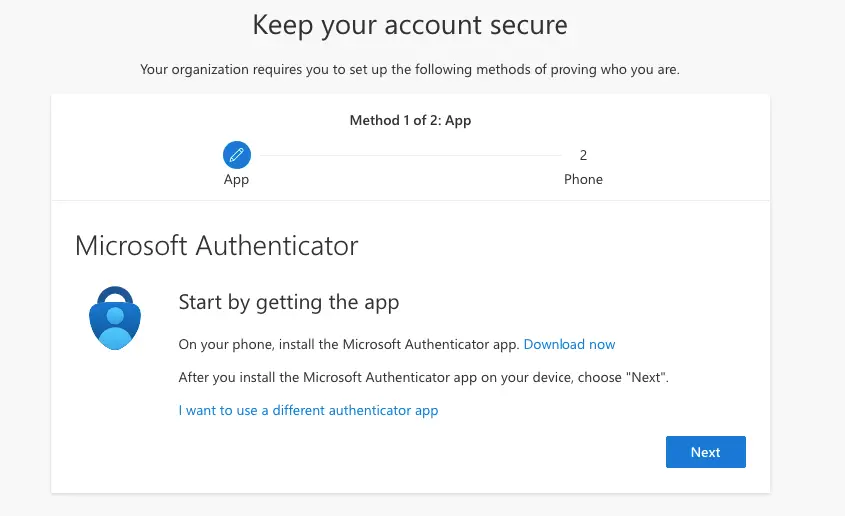
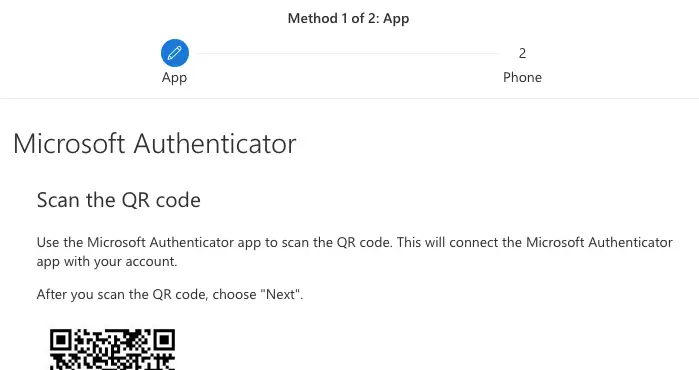
Click on next to continue and a QR code will appear on the Microsoft Authenticator app
Scan the QR shown via your phone
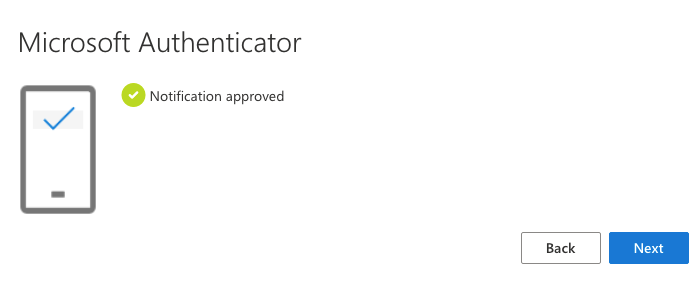
Approve the Sign in on your phone
Enter the MFA pin
Click on Next
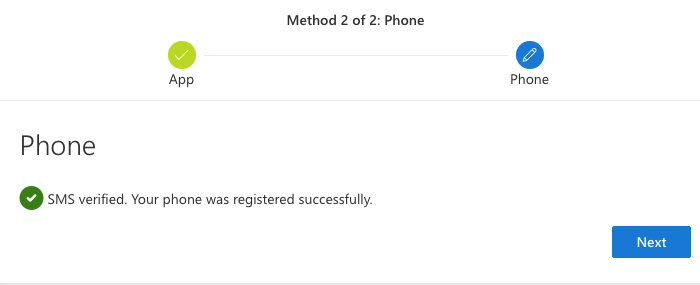
You can log in to your account.
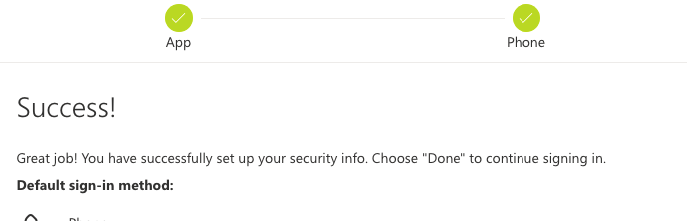
Login to your account.
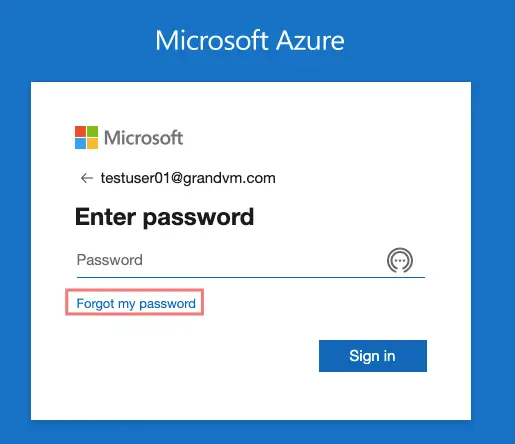
A notification will be sent to the Authenticator App and you will be able to log in using Azure Multi-Factor Authentication.
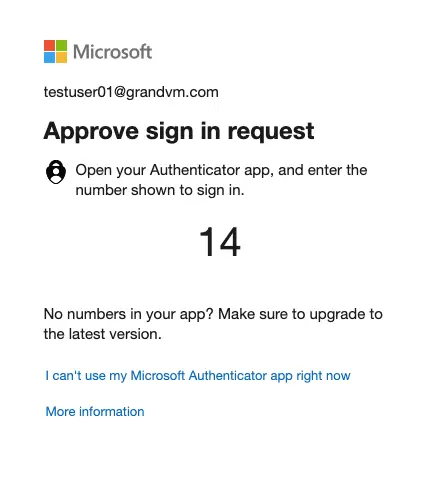
Reset a Forgotten Password
Once MFA is enabled, to reset a forgotten password, click on the login screen click on Forgot password
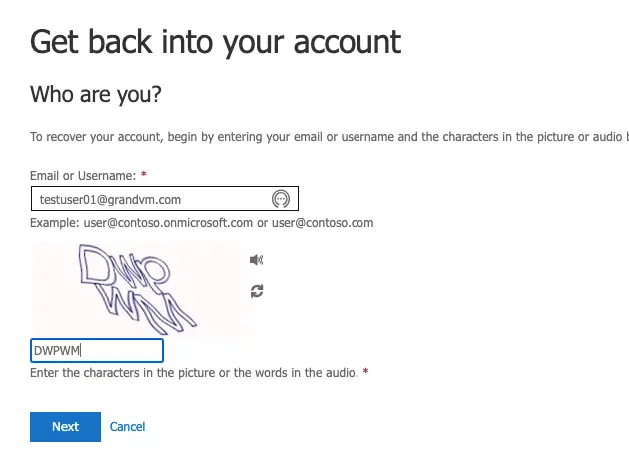
Enter the code you got on the phone
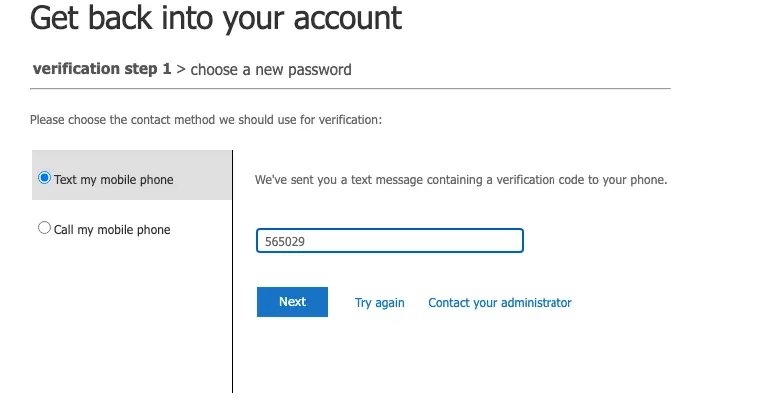
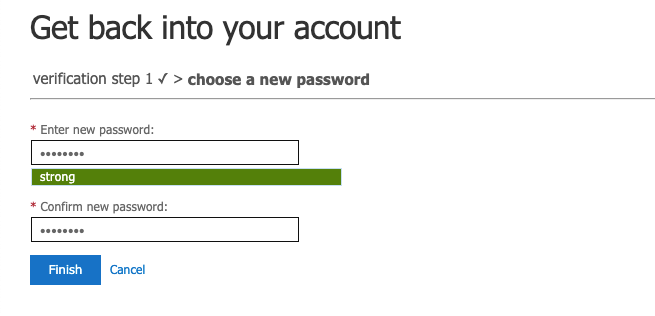
Give a password
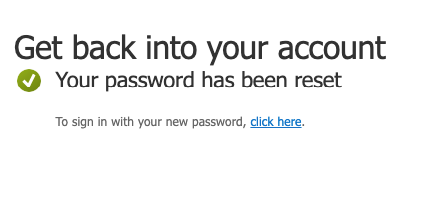
Our password has been reset
Test if we are able to login
Enable MFA for Admins using Azure AD Conditional Access
Enabling MFA Azure AD Conditional Access will need Azure AD Premium plan 1 or 2 licenses. When you have a lot of users in an organization enabling MFA at a user level is not practical so conditional access is set based on some conditions. Security defaults must be disabled to enable the Conditional Access policy.
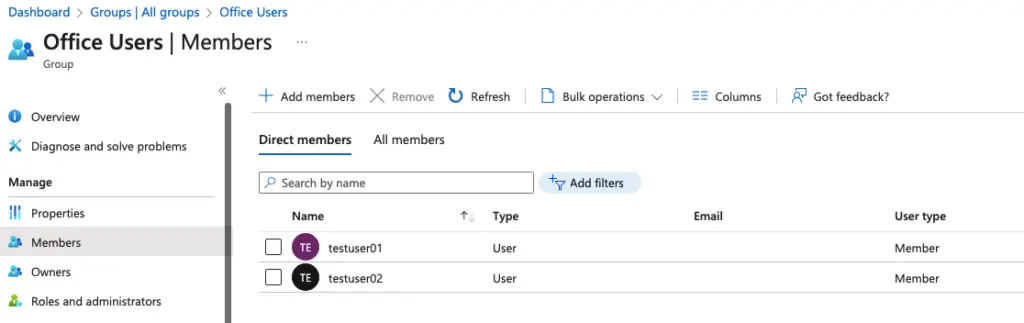
I’ve created an AD Group and added a few users.
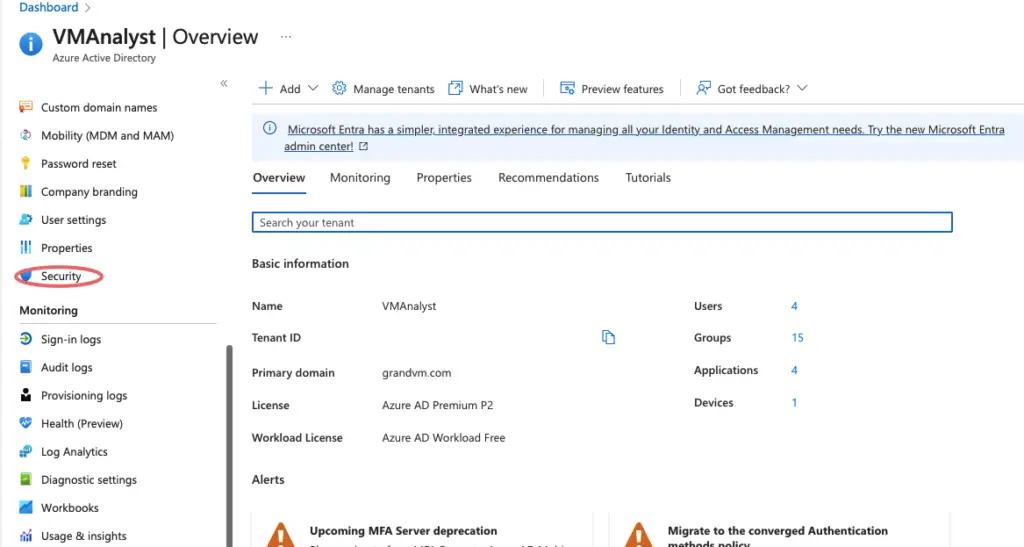
Browse to Active Directory > Security
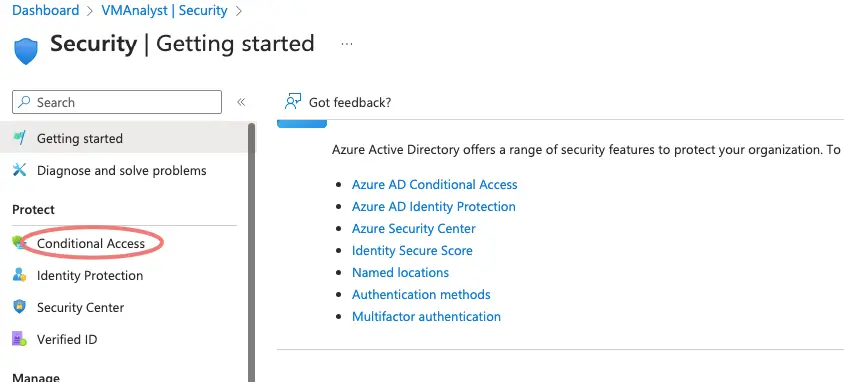
Browse Conditional Access > Policies.
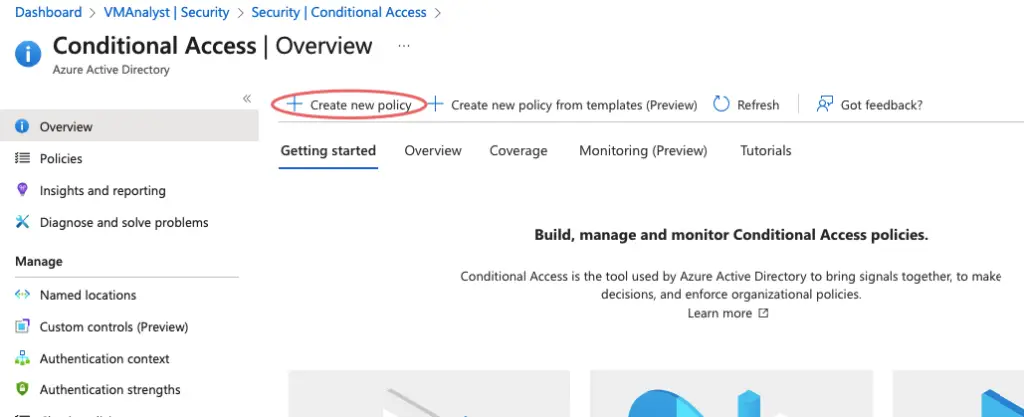
Click on New policy
Provide the following info
- Name of the policy
- Click Users and Groups> Include > Select Group we created
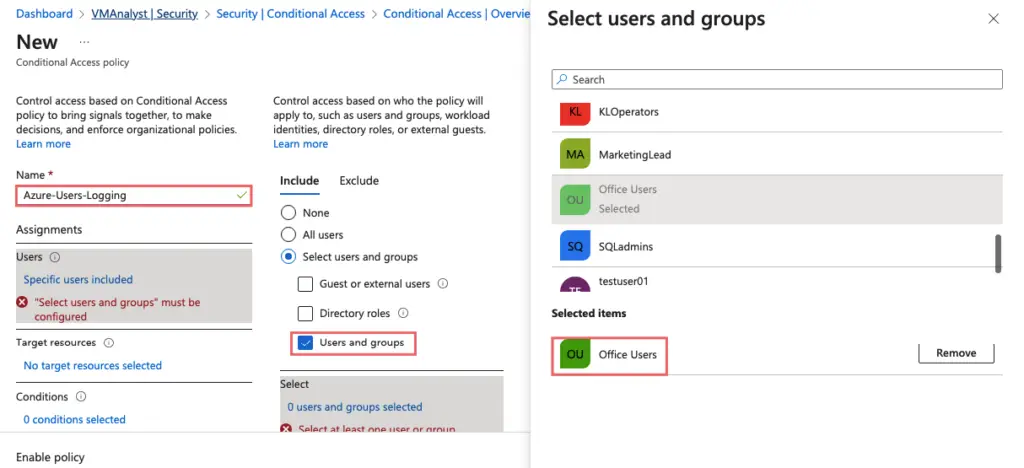
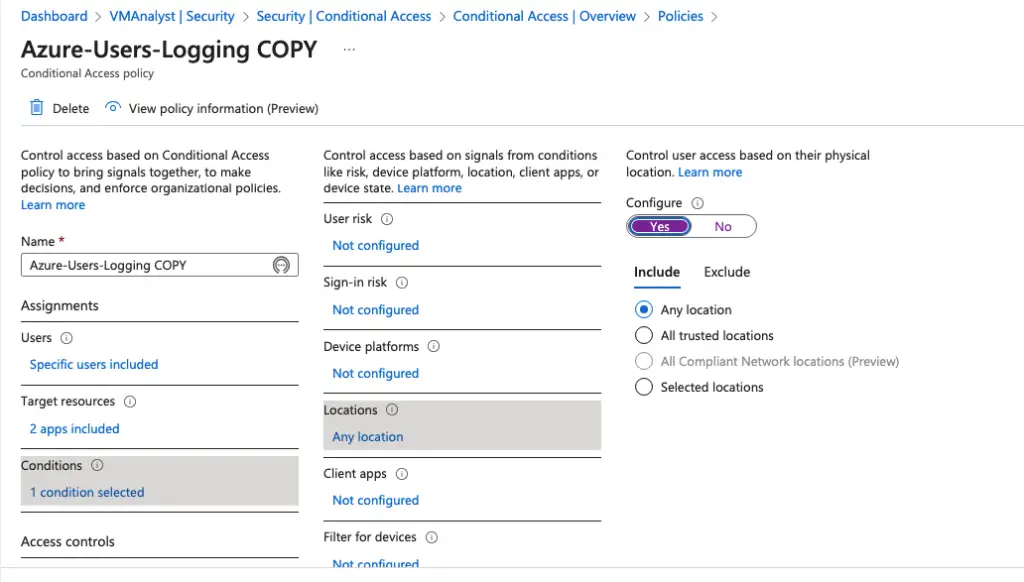
Click Conditions > Locations. Click on Yes and click Include and select Any location.
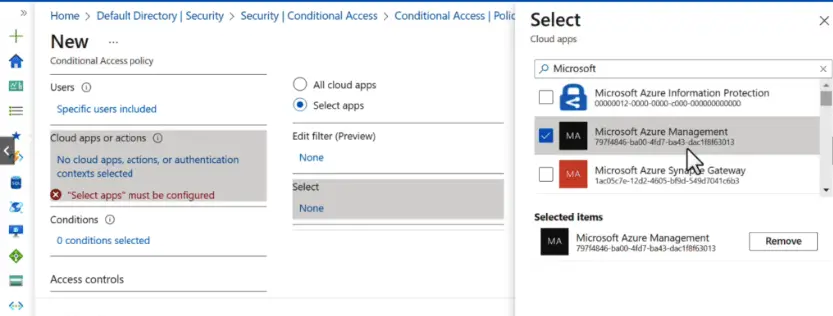
Under Cloud Apps, we will select Microsoft Azure Management
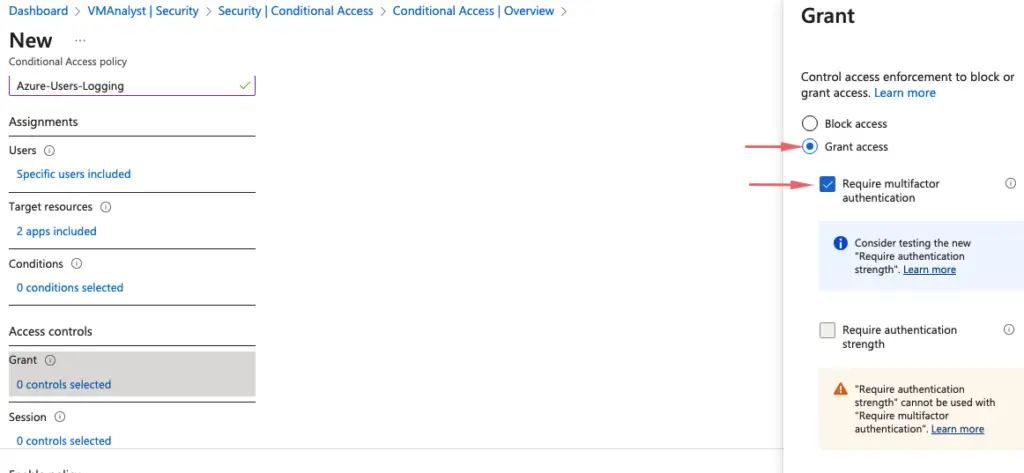
Under Access Control, we will choose to Grant Access and enable MFA and check the checkbox require multi-factor authentication
Click the On switch to enable the policy and click Create.
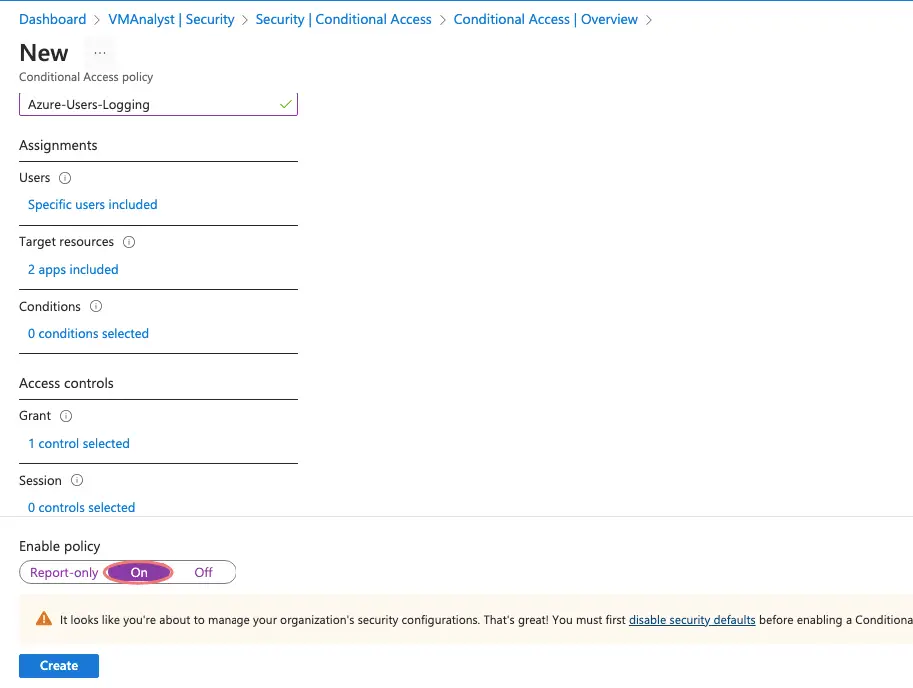
Our conditional access policy is thus created
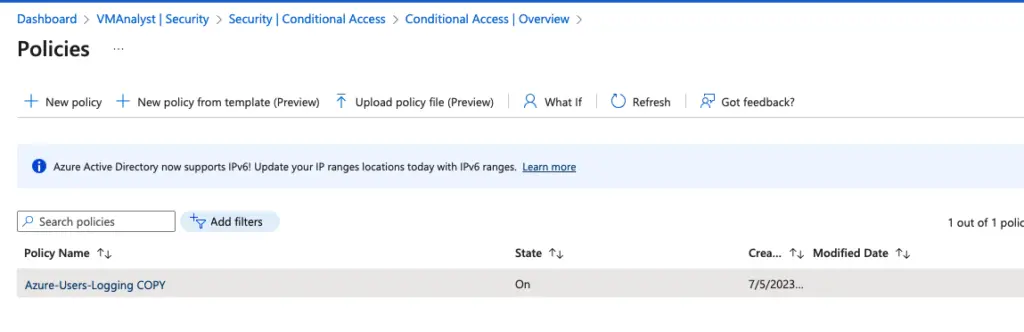
Authenticate via the testuser01 and see if we are getting the MFA request.

That’s it to configure Conditional Azure AD Multi-Factor Authentication.

