Authentication (Who are you?)
Authentication is the process of establishing the identity of a person or service looking to access a resource. It involves the act of challenging a party for legitimate credentials and provides the basis for creating a security principal for identity and access control use. It establishes if they are who they say they are.
Authorization (What are you allowed to do?)
Authorization is the process of establishing what level of access an authenticated person or service has. It specifies what data they’re allowed to access and what they can do with it.
Azure Firewall
Azure Firewall is a managed, cloud-based, network security service that protects your Azure Virtual Network resources. It is a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability. It’s essentially a set of rules that dictate what sort of traffic is allowed.
eg: Allow Inbound Traffic for Remote Desktop Protocol (RDP), Secure Shell (SSH), and File Transfer Protocol (FTP). It also provides outbound, network-level protection for all ports and protocols, and application-level protection for outbound HTTP/S.
Azure DDoS Protection
DDOS attack would mean a flood of traffic to a website to take it down. Azure DDoS Protection service protects your Azure applications by scrubbing traffic at the network edge before it can impact your service’s availability. Within a few minutes of attack detection, you are notified using Azure Monitor metrics.
Network Security Group (NSG)
As the name suggests this is an extra layer of security that can be applied at the NIC or subnet level which gives us the ability to do micro-segmentation and control what sort of traffic is allowed to and from the VM
Application Security Group (ASG)
Allows Grouping VM’s and virtual machines into the application groups and applying security groups to control traffic flowing via it
- Once in the Azure portal, click on the menu in the upper-left and select Virtual Machine. Note the location of these machines, you’ll need that detail momentarily.
- Head back to the main menu and select All Services. In the search bar type: application security groups and select that service. On the Application Security group page, click the Add button.
- For resource group section click the drop-down menu and select the pre-existing resource group.
- Under the instance details section, set the name field to asgWebServers. Ensure the region is set to the same region as your Virtual Machines
- Click review and create.
Create a New Application Security Group
- Go to Network Security groups and click on the existing security group.
- Select Inbound security rules on the left, and click add.
- For Destination select Application Security group.
- For Destination application security group choose asgWebServers.
- The Destination port ranges are set to 80,443.
- Set Priority to 124.
- Under Name set to WebServers_Rule.
- Finally, click the add button. You’ll see this new rule amongst your list.
- Head back to the Azure menu in the upper-left and select Virtual Machine.
- Next, we attach the application security group to the networking interface of each VM.
- Select your first VM.
- Click the Networking tab, click Application security groups.
- Select Configure the application security group, select aswWebServers from the drop-down, press Save.
- Repeat the last two steps for your second VM.
Attach
Go to Application Security Groups and add rule
Azure Security Center
Security Center is a monitoring service that provides threat protection across all of your services both in Azure, and on-premises. Available in two tiers, Free (limited to assessments and recommendations only); Standard (full suite of security-related services including continuous monitoring, threat detection and just-in-time access control)

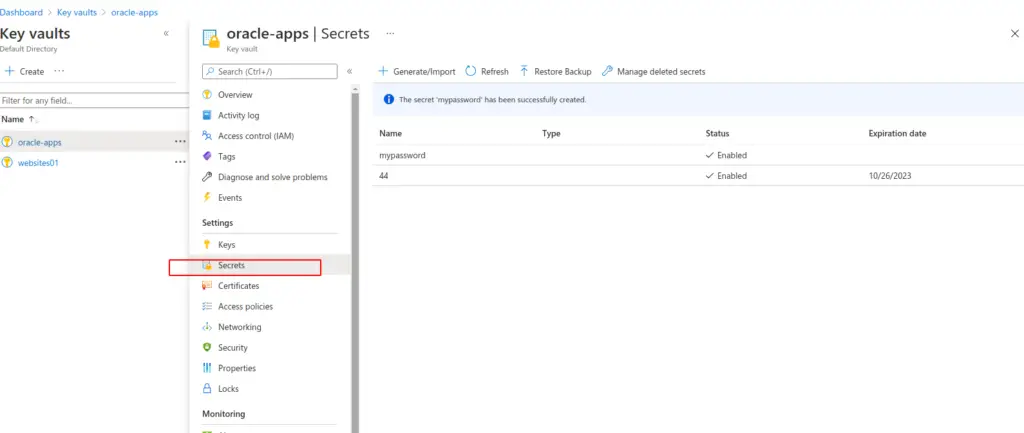
KeyVault
Azure Key Vault is a secret store: a centralized cloud service for storing application secrets. Key Vault helps you control your applications’ secrets by keeping them in a single central location and providing secure access, permissions control, and access logging.
If our database has a password and we wish to have our external consultants access to this database we can place the password in the key vault and provide access to individual applications they need info.

Passwords can be shared via secret keys

Microsoft Defender for Identity
Allows monitoring internal user behaviour. It will create a baseline based on the users regular activity and anything he does other than the default behaviour will be logged as suspicious.
Microsoft Azure Information Protection (MSIP)
This helps to classify and optionally protect documents and emails by applying labels or tags such as Important, sensitive etc. If a user wishes to send an email with a sensitive attachment to another colleague he can place the data with a tag in Azure Information protection. The recipient will get an email link thus we can analyse data flows, detect risky behaviour, track access to documents, prevent data leakage or misuse of confidential information.

Azure Monitor
Azure Monitor maximizes the availability and performance of your applications by delivering a comprehensive solution for collecting, analyzing, and acting on telemetry from your cloud and on-premises environments. It helps you understand how your applications are performing and proactively identifies issues affecting them and the resources they depend on.
Azure Service Health
Azure Service Health is a suite of experiences that provide personalized guidance and support when issues with Azure services affect you. It can notify you, help you understand the impact of issues, and keep you updated as the issue is resolved. Azure Service Health can also help you prepare for planned maintenance and changes that could affect the availability of your resources.

Azure Monitor
It’s a solution to collect metrics from Azure all the time. It’s detailed monitoring across all Azure services which can be scoped as per our requirement.
Trust Center
Trust Center is a website resource containing information and details about how Microsoft implements and supports security, privacy, compliance, and transparency in all Microsoft cloud products and services. The Trust Center is an important part of the Microsoft Trusted Cloud Initiative, and provides support and resources for the legal and compliance community.
Service Trust Portal
The Service Trust Portal (STP) hosts the Compliance Manager service and is the Microsoft public site for publishing audit reports and other compliance-related information relevant to Microsoft’s cloud services.
Azure Sentinel (SIEM tool )
Centralised monitoring for all data collected by Azure/AWS. It protects the Cloud.


Azure Active Directory (Authentication, SSO, Application Management, B2B Identity Services, Device Management)
Azure AD is a cloud-based identity service. It has built in support for synchronizing with your existing on-premises Active Directory or can be used stand-alone. This means that all your applications, whether on-premises, in the cloud (including Office 365), or even mobile can share the same credentials. Administrators and developers can control access to internal and external data and applications using centralized rules and policies configured in Azure AD.AuthenticationSingle Sign-On (SSO)Application ManagementBusiness to Business (B2B) Identity ServicesDevice Management
Azure Multi-Factor Authentication
Multi-factor authentication (MFA) provides additional security for your identities by requiring two or more elements for full authentication.
These elements fall into three categories:
Something you know (e.g. password)Something you possess (e.g. mobile app)Something you are (e.g. fingerprint or face scan)
Azure Security Center – Usage Scenarios
Incident Response (Detect, Assess, Diagnose)Implement Recommendations
Azure Advanced Threat Protection (Azure ATP)
A cloud-based security solution that identifies, detects, and helps you investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Azure ATP is capable of detecting known malicious attacks and techniques, security issues, and risks against your network.
Azure Policies
Azure Policy is a service you can use to create, assign, and manage policies. These policies apply and enforce rules that your resources need to follow. These policies can enforce these rules when resources are created, and can be evaluated against existing resources to give visibility into compliance.
Initiatives
Initiatives work alongside policies in Azure Policy. An initiative definition is a set or group of policy definitions to help track your compliance state for a larger goal.
Role-Based Access Control
RBAC provides fine-grained access management for Azure resources, enabling you to grant users the specific rights they need to perform their jobs. RBAC is considered a core service and is included with all subscription levels at no cost.
Resource Locks
Resource locks are a setting that can be applied to any resource to block modification or deletion. Resource locks can set to either Delete or Read-only. Delete will allow all operations against the resource but block the ability to delete it. Read-only will only allow read activities to be performed against it, blocking any modification or deletion of the resource. Resource locks can be applied to subscriptions, resource groups, and to individual resources, and are inherited when applied at higher levels.
General Data Protection Regulation (GDPR)
As of May 25, 2018, a European privacy law — GDPR — is in effect. GDPR imposes new rules on companies, government agencies, non-profits, and other organizations that offer goods and services to people in the European Union (EU), or that collect and analyze data tied to EU residents. The GDPR applies no matter where you are located.
ISO/IEC 27018
Microsoft is the first cloud provider to have adopted the ISO/IEC 27018 code of practice, covering the processing of personal information by cloud service providers.
National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF)
NIST CSF is a voluntary Framework that consists of standards, guidelines, and best practices to manage cybersecurity-related risks. Microsoft cloud services have undergone independent, third-party Federal Risk and Authorization Management Program (FedRAMP) Moderate and High Baseline audits, and are certified according to the FedRAMP standards. Additionally, through a validated assessment performed by the Health Information Trust Alliance (HITRUST), a leading security and privacy standards development and accreditation organization, Office 365 is certified to the objectives specified in the NIST CSF.
Microsoft Privacy Statement
The Microsoft privacy statement explains what personal data Microsoft processes, how Microsoft processes it, and for what purposes.
Compliance Manager
Compliance Manager is a workflow-based risk assessment dashboard within the Trust Portal that enables you to track, assign, and verify your organization’s regulatory compliance activities related to Microsoft professional services and Microsoft cloud services such as Office 365, Dynamics 365, and Azure.
Azure Government Services
Azure Government is a cloud environment specifically built to meet compliance and security requirements for US government. Physically separated instance of Microsoft Azure, specifically for U.S. Government, meets complex compliance standards, designed to exceed U.S. Government requirements.

