An Azure policy is an access system that provides “Allow” or “Deny” on new or existing resources to which the policy applies. Azure Policy helps us to create, assign and manage policies via which we can enforce compliance and enable auditing across our organisation. For example, if we wish to use only US East Region to spin up our resources we can do so by creating an Azure Policy.
Advantages of using Azure Policies:
- Real-time policy evaluation and enforcement for all resources ensuring compliance.
- Apply policies to a Management Group with control across your entire organization.
- Real-time remediation of existing resource eg: Azure Backup
- Enforce a required tag and its value.
- Specify the resource types that your organization can deploy.
- Prohibit the creation of resources in a region or a location.
- Specify a set of virtual machine SKUs that your organization can deploy.
- Audit if Azure Backup service is enabled for all Virtual machines.
- Restrict access to services we don’t want being deployed.
Azure Policies can be implemented at various scopes within our organization such as
- Management groups
- Subscriptions
- Resource groups
- Individual resources
In this blog, we will restrict users from spinning up resources in any other region other than US East.
Log in to the Azure portal and search for Azure policy
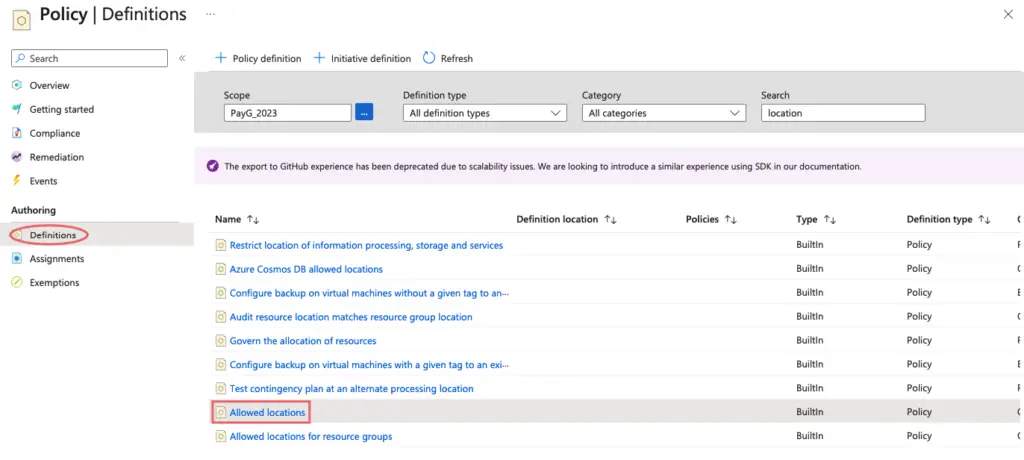
Under the Authoring – Definition tab, we can see the list of predefined policies – Click on the Allowed location policy.
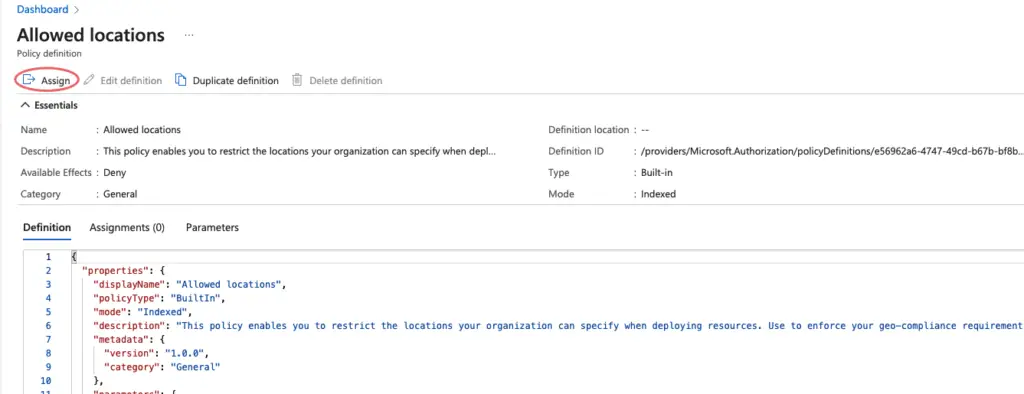
Towards the left side of the page, click on the Assign tab.
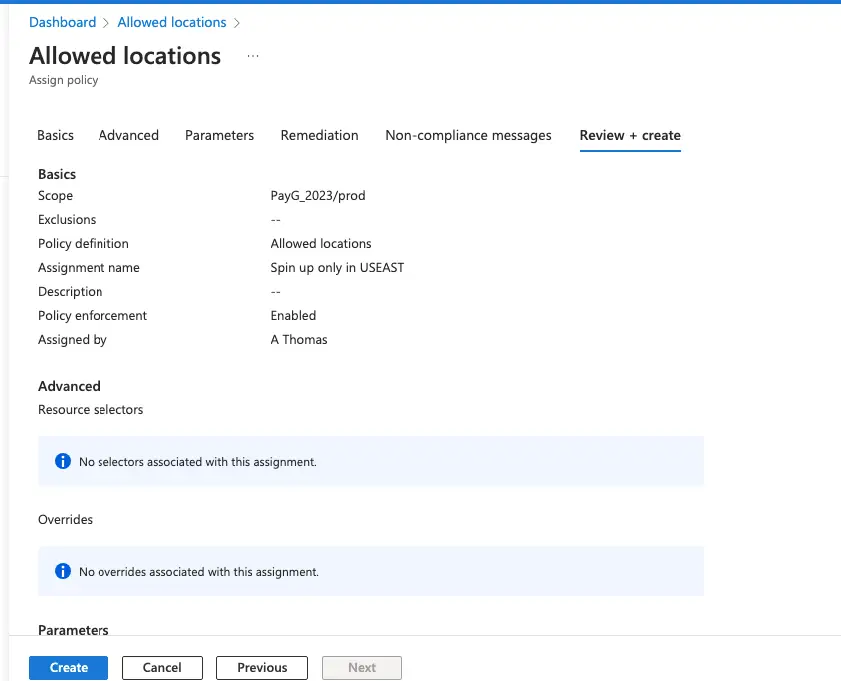
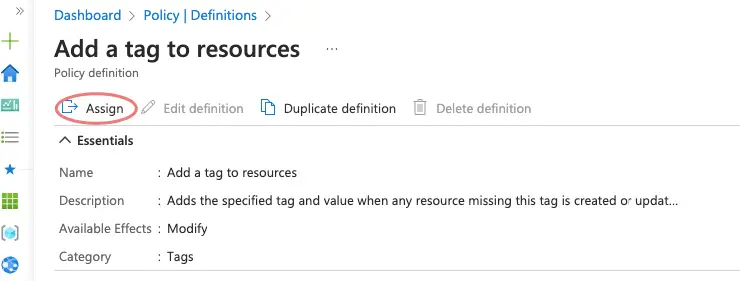
Choose the subscription and Scope
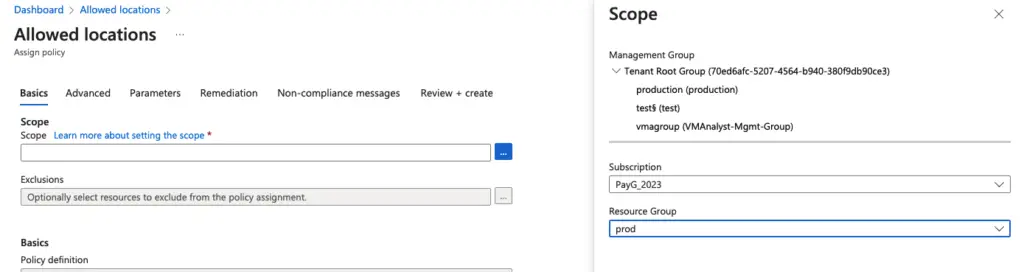
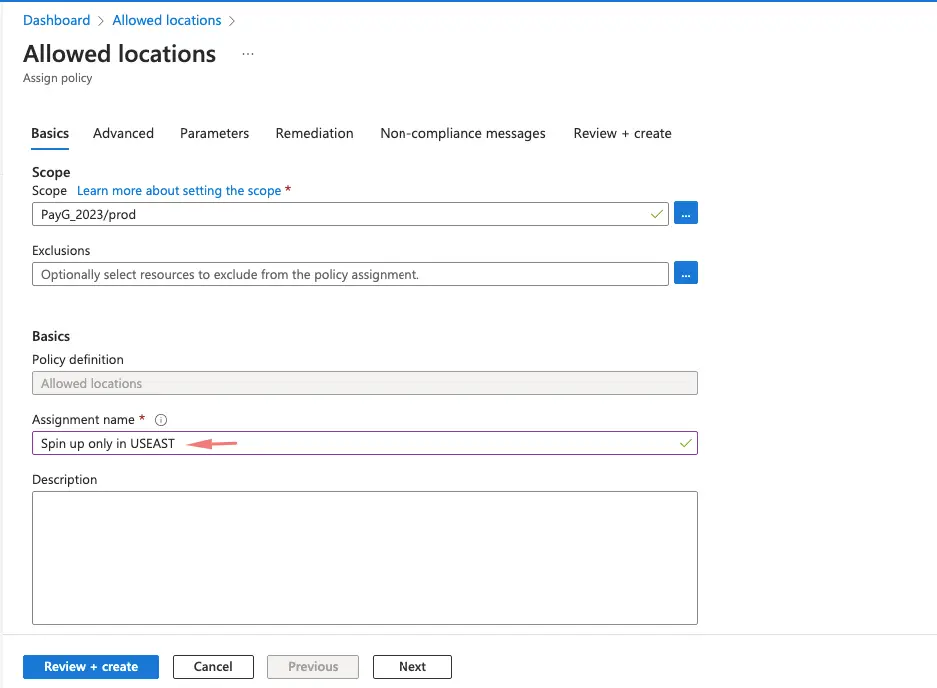
Give the policy assignment a name.
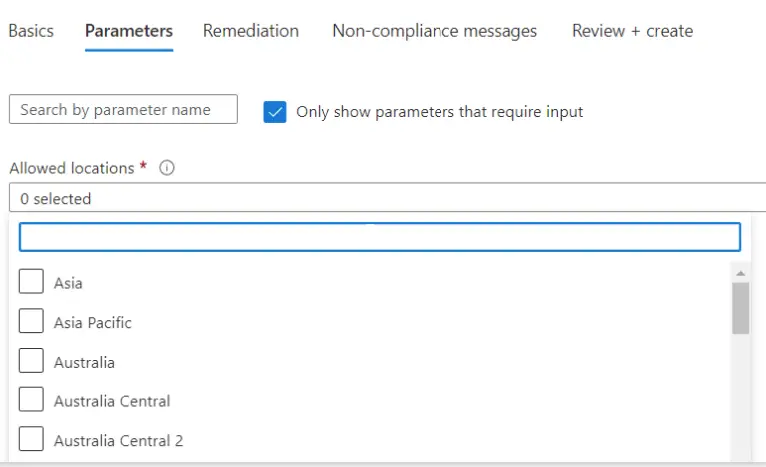
In the Parameters tab, search for US East
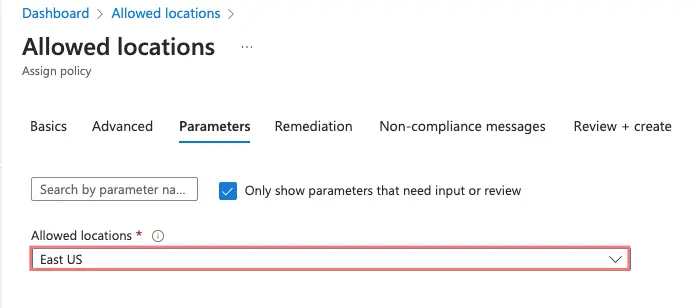
Select US East
Click Review and Create
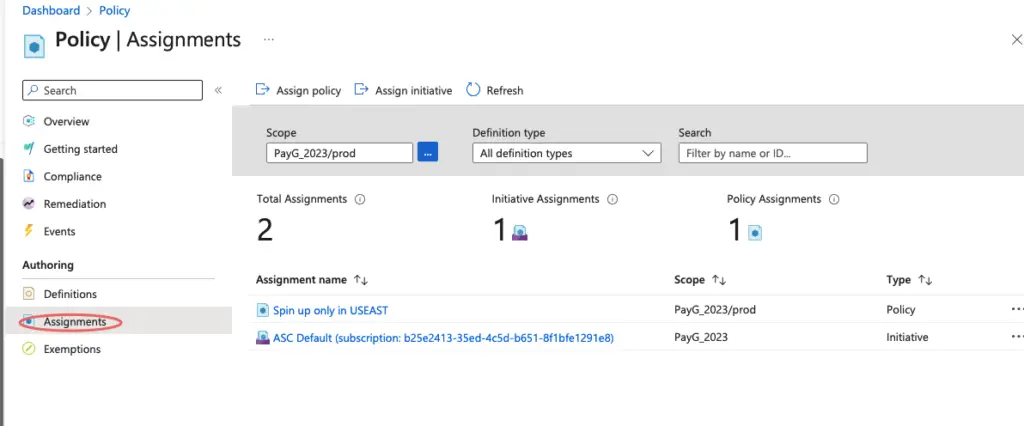
Our policy we created appears under the Assignment tab.
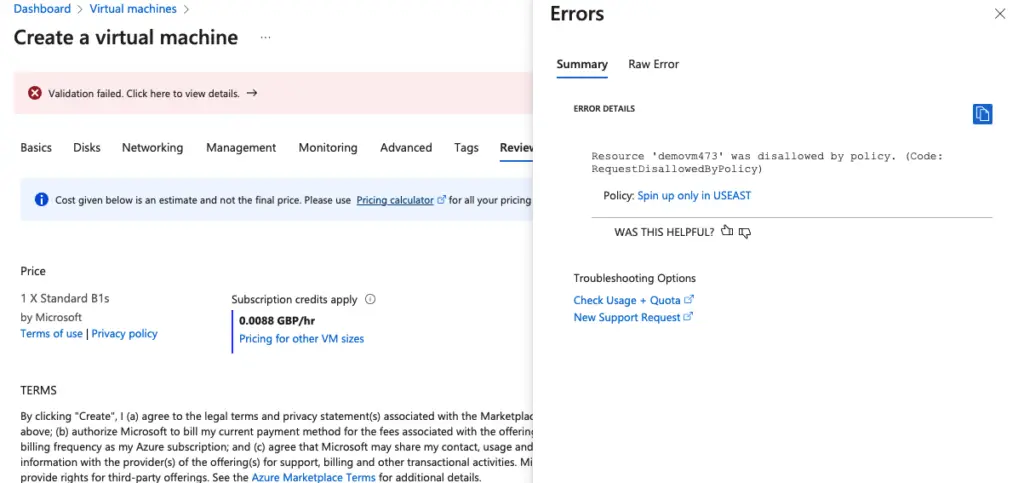
As we now attempt to create a new VM, in an alternate region the policy is evaluated and we will get an error preventing us to deploy the resource.
Applying Tags to Subscriptions
Under the Authoring – Definition tab, we can see the list of predefined policies – Click on Add a tag to resources
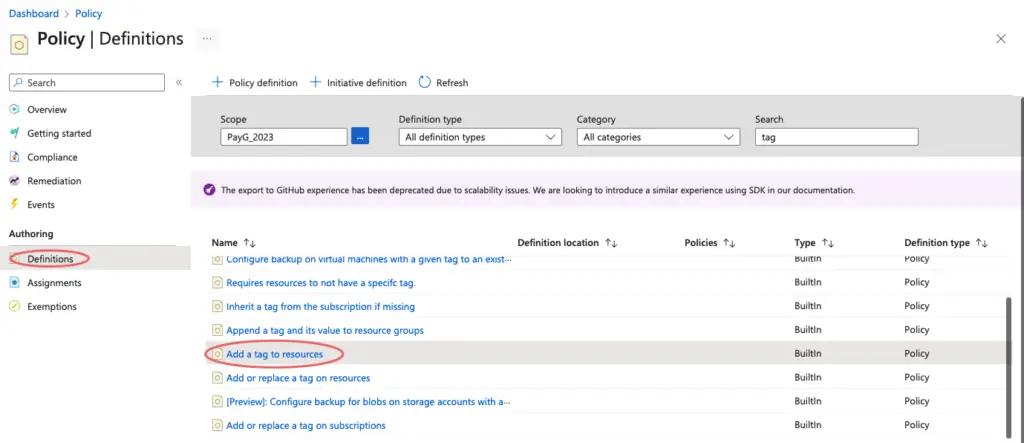
Towards the left side of the page, click on the Assign tab.
Give the policy assignment a name.
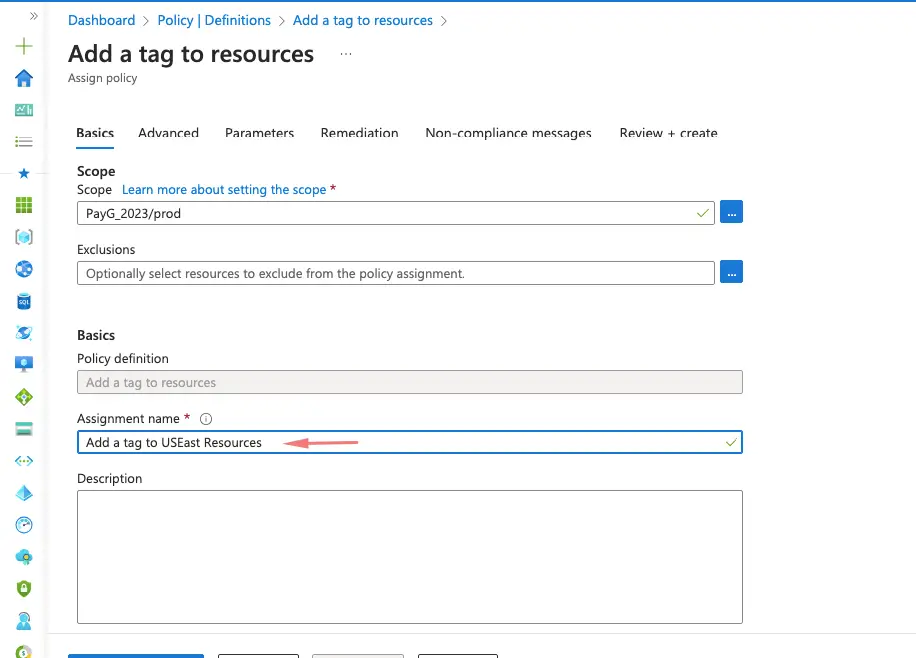
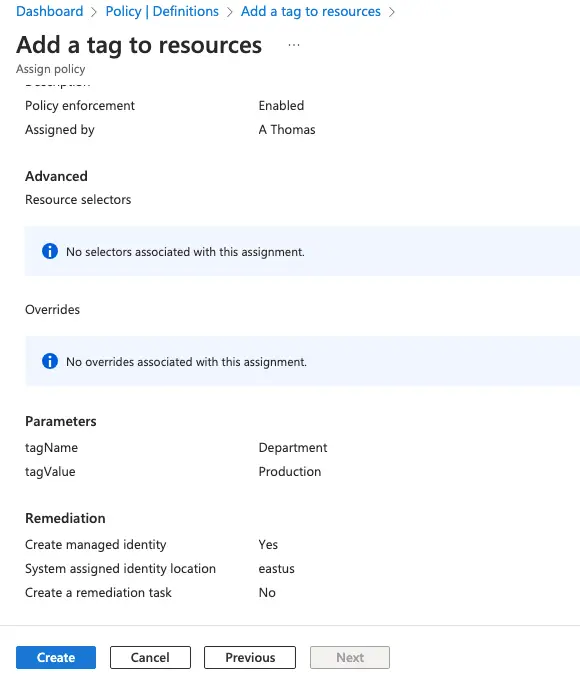
Under the parameters section define the tags needed
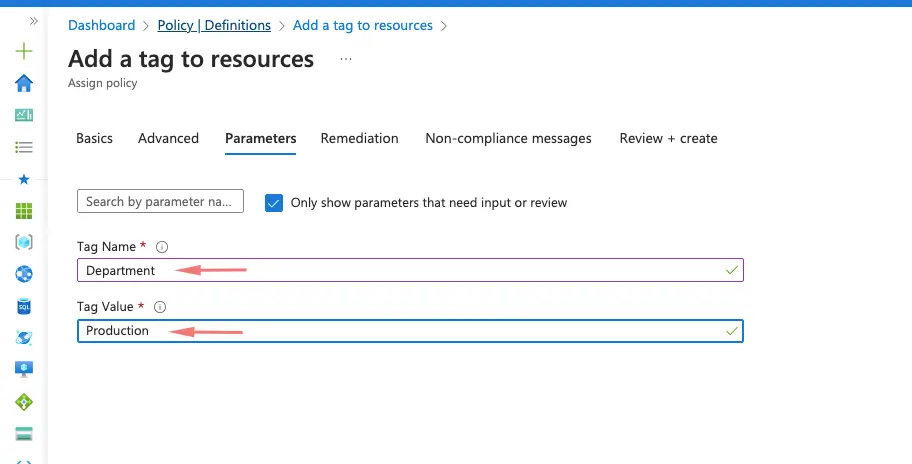
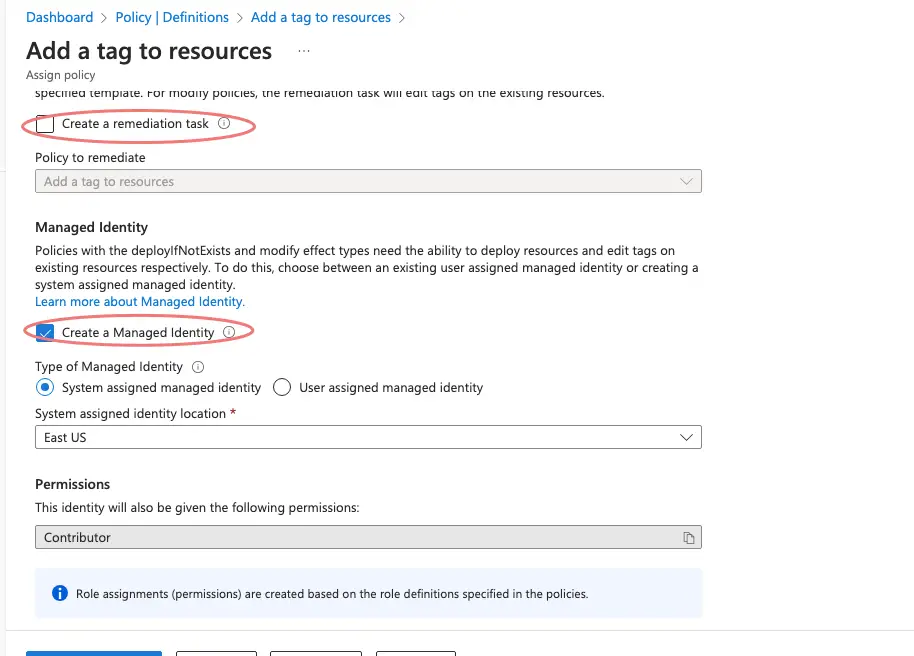
We have an option of creating a remediation task to correct any non-compliant resources if needed in this task.
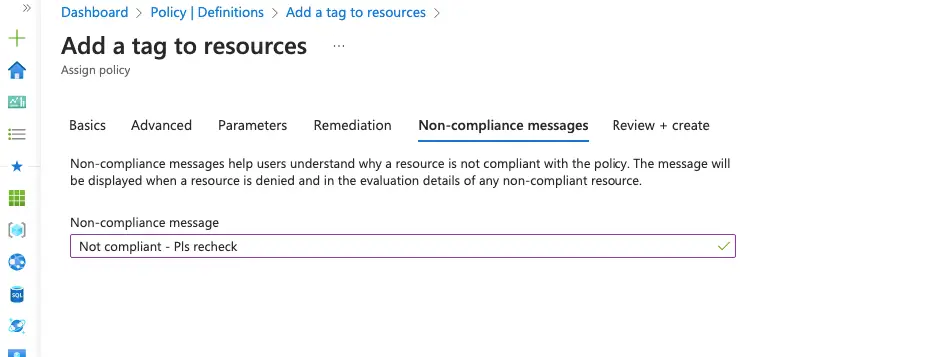
Give a message to display for non-compliance
Finally, click Review and Create
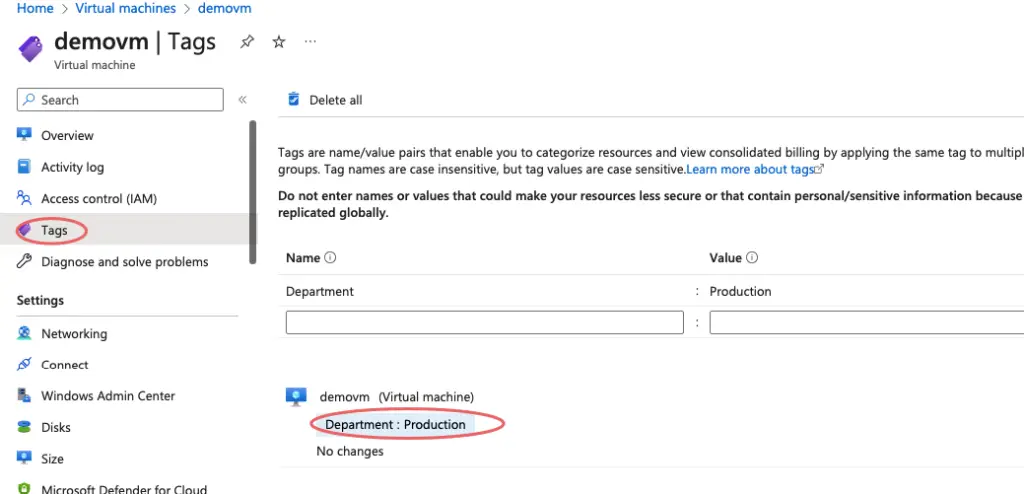
Under the VM, we can now see tags being applied via the policy.