In this blog, we will verify our end-to-end connectivity and verify if NSX-T Is working properly
I’ve configured all these segments as per the previous blog
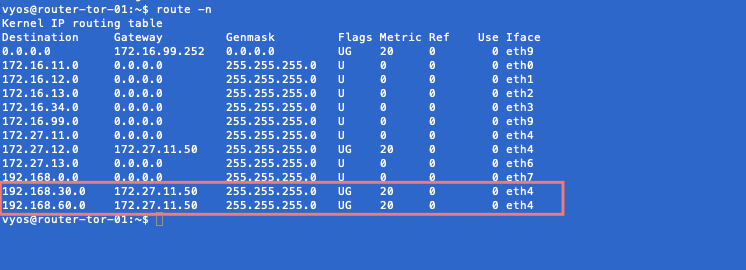
‘192.168.30.0’ network & ‘192.168.60.0’ are learned from ‘172.27.11.50’ and this is our Edge uplink1.
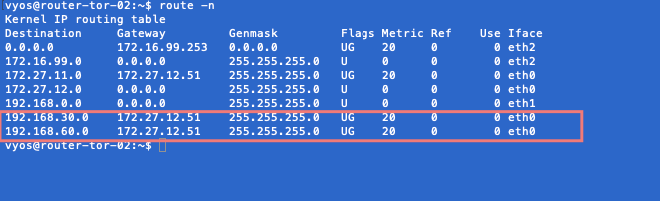
‘192.168.30.0’ network & ‘192.168.60.0’ are learned from ‘172.27.12.51’ and this is our Edge uplink2.
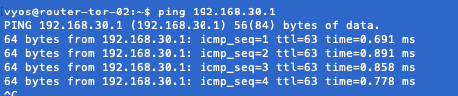
This shows my routing is working perfectly and we can now ping our segment gateway to verify it so this confirms our North-South routing is working as it should be.
Log into our edge and run get logical-router
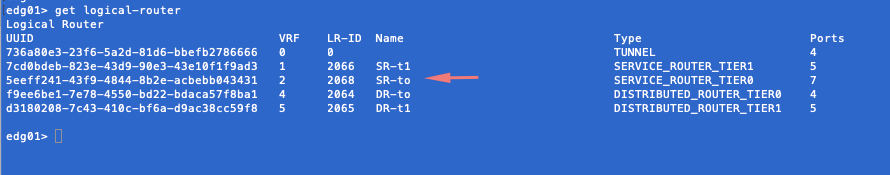
We need to connect to the Tier-0 Service Router to check further details. Note that the VRF ID for Tier-0 Service Router is ‘2’
vrf 2 & then run get route
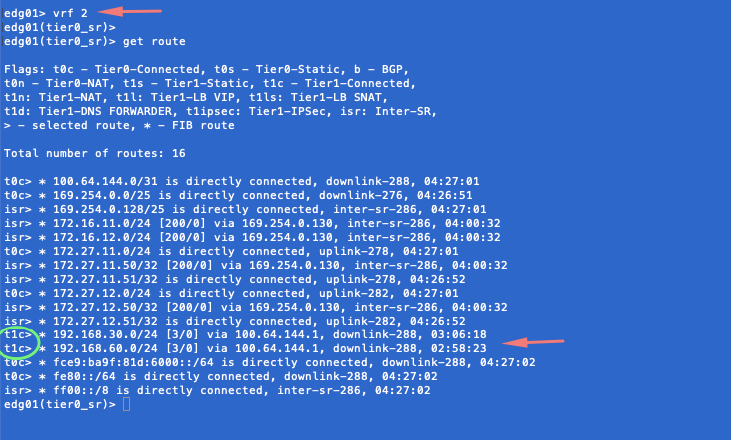
We see ’192.168.30.0/24’ network as t1c (Tier-1 Connected). That means our route is reaching till our Edge.
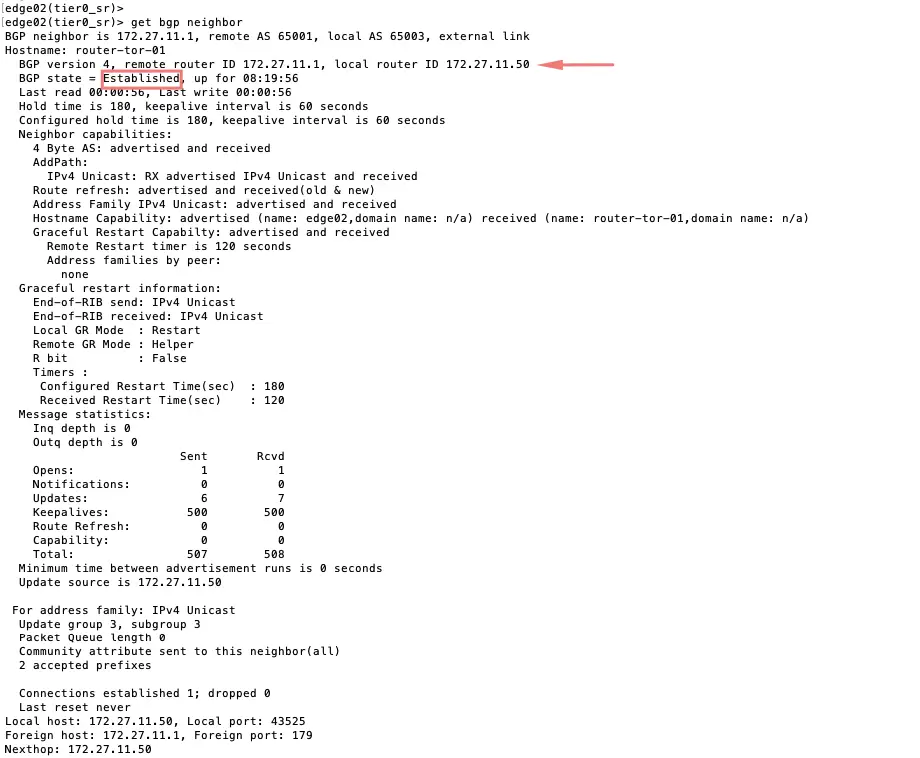
Run BGP neighbour and we can see (172.27.11.1 & 172.27.12.1).
Use ‘’traceroute’ command from vrf’s and edge to trace the packet.

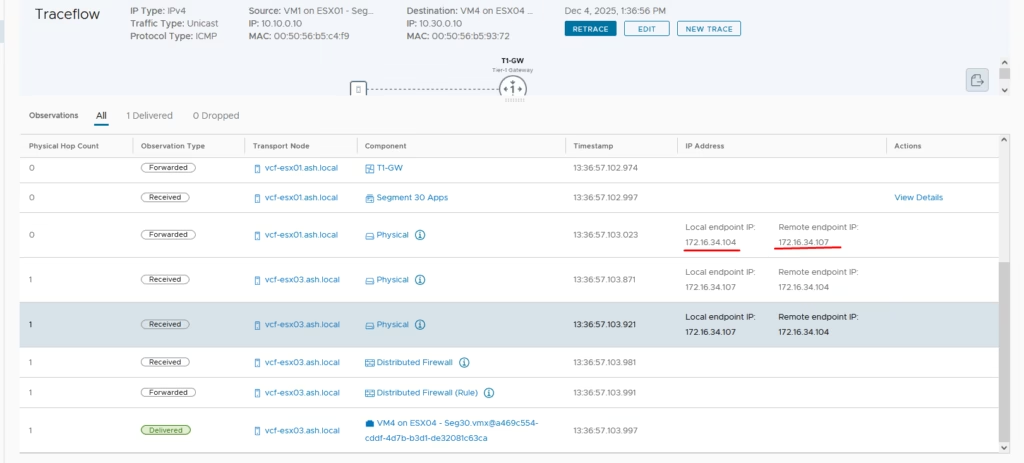
Traceflow in VMware NSX
VMware NSX offers a powerful built-in tool called Traceflow that helps you shine a light on packet journeys across your virtual network. Traceflow simulates the path of a packet through the NSX environment.
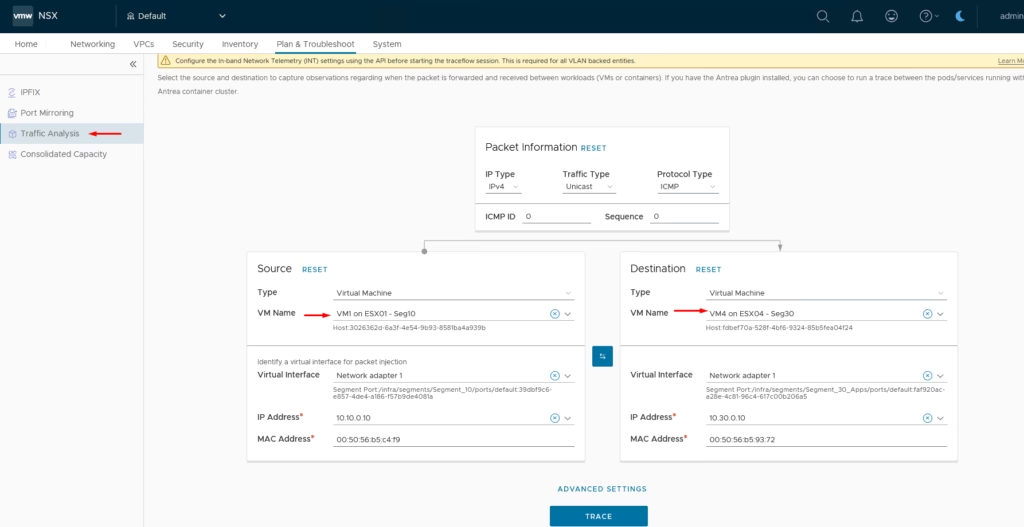
How It Works – Traceflow: VM1 (Seg10) to VM4 (Seg30)
When troubleshooting east–west traffic in NSX, Traceflow shows exactly how packets move between segments and across hosts.
Scenario
- Source: VM1 on ESX01, Seg10 — IP 10.10.0.10, MAC 00:50:56:b5:c4:f9
- Destination: VM4 on ESX04, Seg30 — IP 10.30.0.10, MAC 00:50:56:b5:93:72
Packet Journey
- When VM1 (10.10.0.10 on Seg10, ESX01) sends traffic to VM4 (10.30.0.10 on Seg30, ESX04), NSX Traceflow shows the following path:
- VM1 vNIC ingress → Packet generated at VM1 enters ESX01.
- DFW check (source) → Distributed Firewall evaluates rules locally at the vNIC.
- Routing decision (ESX01) → The DR (Distributed Router) instance on ESX01 checks its local routing table. Destination is Seg30, so traffic is forwarded to the Tier‑1 logical router.
- Tier‑1 LR → Routes packet from Seg10 VNI to Seg30 VNI.
- Geneve encapsulation → ESX01 encapsulates the packet with Geneve (UDP 6081), outer src/dst = ESX01 TEP → ESX04 TEP, inner payload = VM1 → VM4.
- Underlay transit → Encapsulated packet traverses the physical fabric.
- Decapsulation (ESX04) → ESX04 TEP strips Geneve, maps to Seg30.
- DFW check (destination) → Firewall rules applied at VM4’s vNIC.
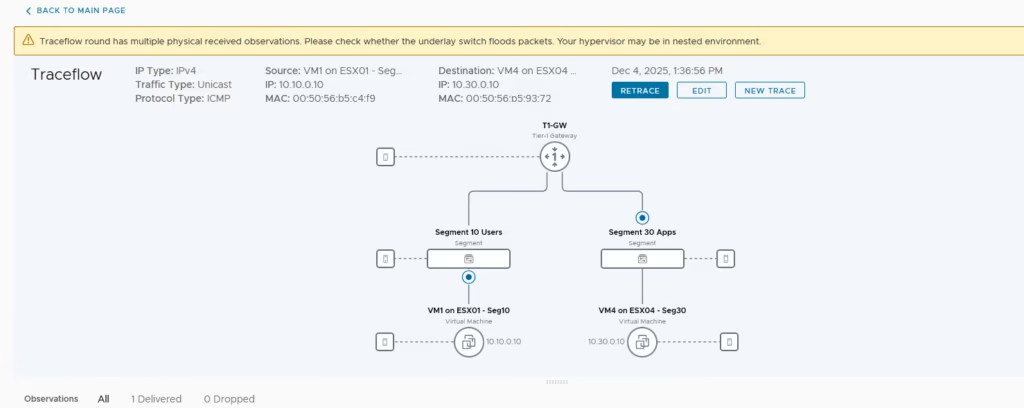
VM4 delivery → Packet delivered to VM4 (MAC 00:50:56:b5:93:72).