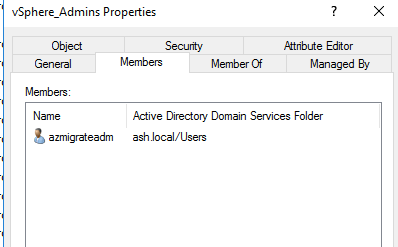
Create an AD security group and add the list of users that needs access to NSX in the group
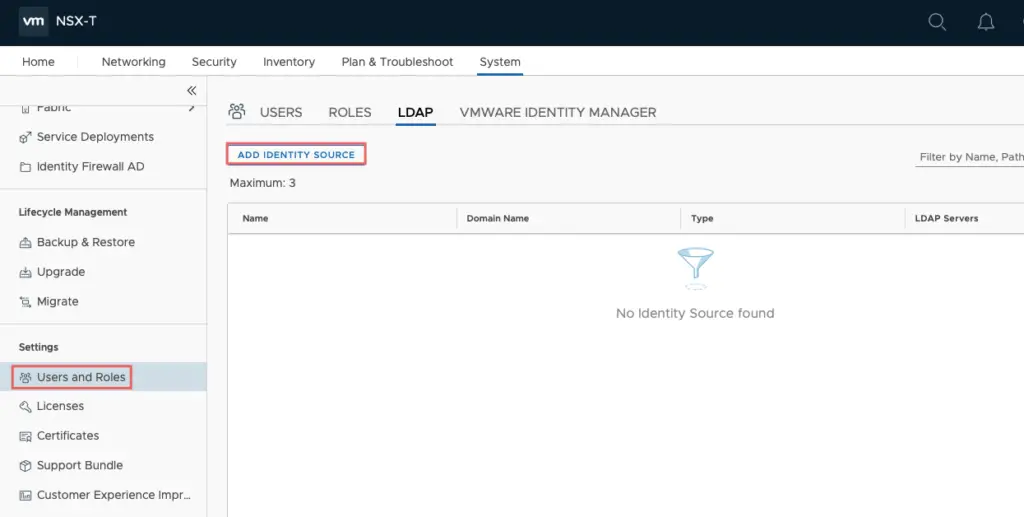
Navigate to System >Users & Roles >LDAP > Click on Add Identity Sources
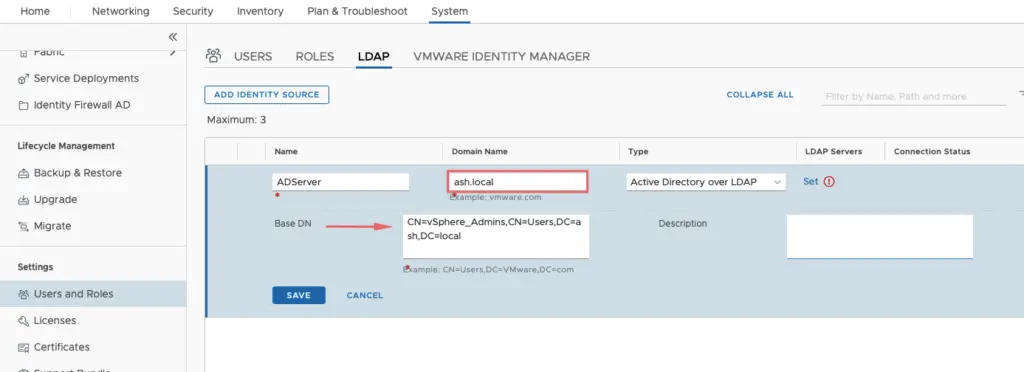
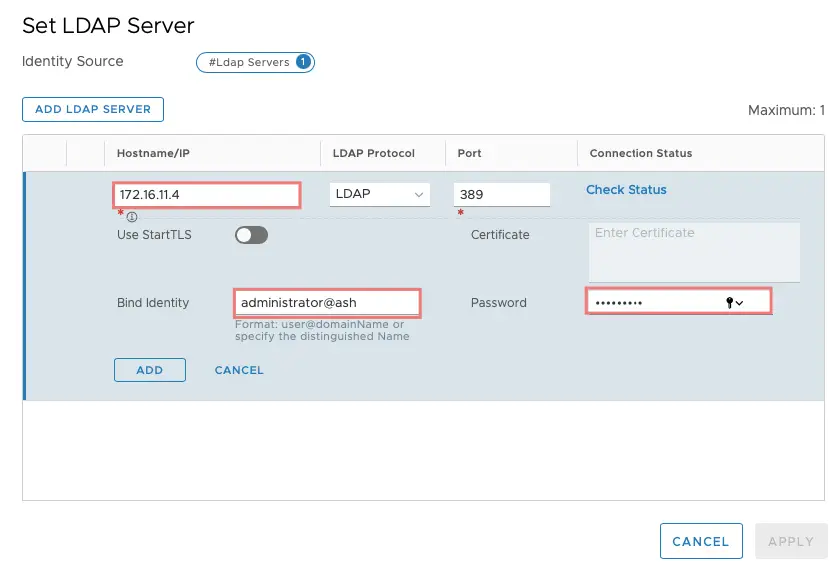
Provide all these details
Name: Some random name
Domain Name: ash.local
Type: Active Directory over LDAP.
Base DN: Copy and paste the CN name of our group in AD
Hostname: IP Address or AD
Protocol: LDAP
Port: 389
Provide the administrator credentials of AD as well and click ADD
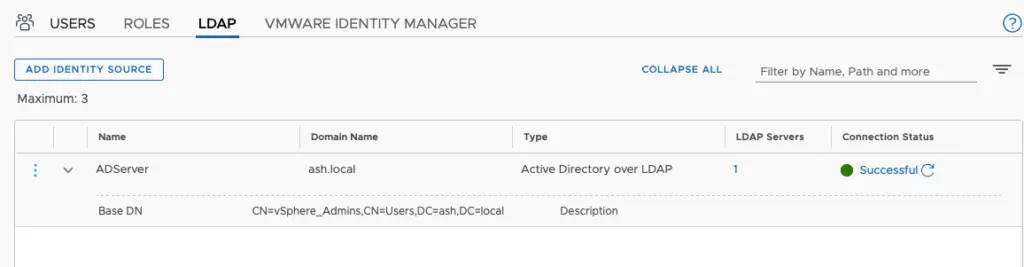
Once validated our LDAP connection will show as successful so thus we have added an identity source in NSX-T.
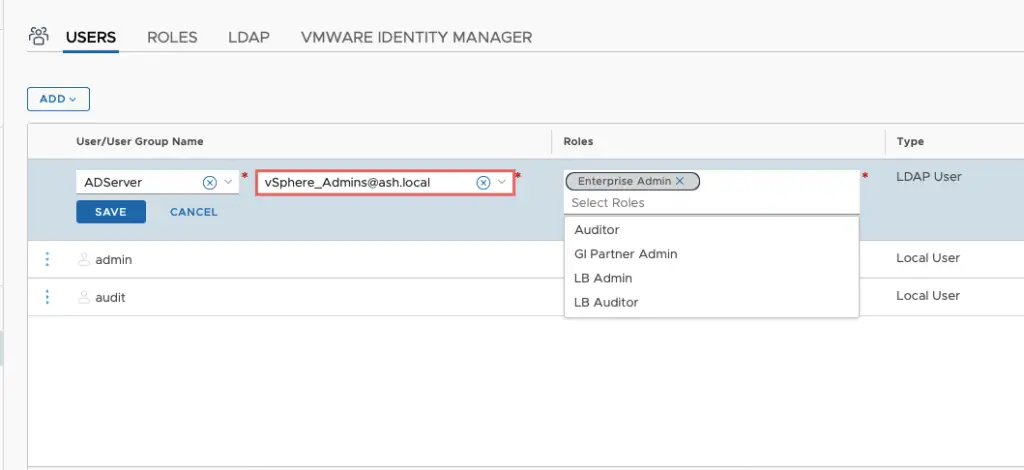
For associating users/groups from the AD we will go to the Users section and add the AD group. Under roles select Enterprise Admin
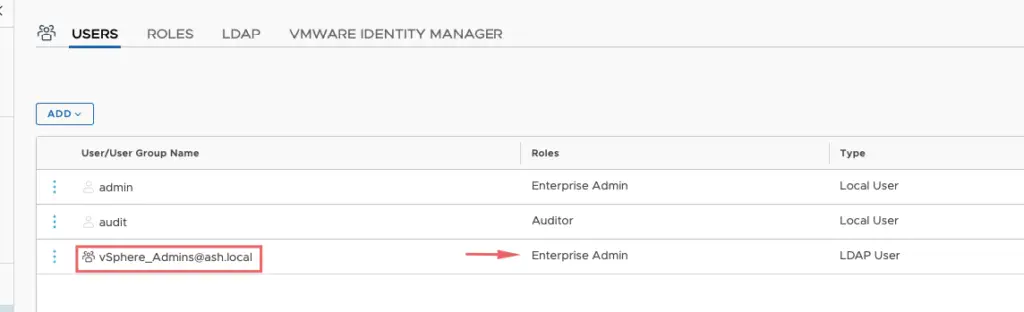
Our AD group vSphere_Admins now has enterprise admin privileges so any user added to this group now gets full permission to NSX-T UI.
Validate by logging on as user.